June 1, 2016 (Austin, TX) Crime Tech Solutions, LLC, a leading provider of analytics and investigation software for law enforcement and commercial markets, today announced that it has acquired Cleveland, TN based Case Closed Software in a cash transaction. The terms of the deal were not released, but according to Crime Tech Solutions’ founder and president Douglas Wood, the acquisition brings together two dynamic and fast-growing software companies with an unparalleled complement of technologies.
“For Crime Tech Solutions, the opportunity to add Case Closed Software into the fold was too good to pass up” said Mr. Wood. “We think that the technology offered by Case Closed helps to further differentiate us in the market as the price performance leader for this type of investigative solution.”
Crime Tech Solutions, based in the city of Leander, TX, delivers advanced analytics and investigation software to commercial investigators and law enforcement agencies across the globe. Their solution suite includes criminal intelligence software, sophisticated crime analytics with geospatial mapping, and powerful link analysis and visualization software. The company says that the addition of Case Closed Software expands those offerings even further.
Case Closed Software develops and markets investigative case management software specifically designed for law enforcement agencies. The suite is built around four primary software products including best-in-class investigative case management software, property and evidence tracking, a gang database tool, and an integrated link analysis and data visualization tool. The company also plans to release the solution as Case Closed Cloud for cloud-based access.
“Case Closed couldn’t be happier than to be joining Crime Tech Solutions,” said Keith Weigand, the company’s founder. “The blending of our technologies creates a suite that will add tremendous value to our mutual customers, and will be hard for others to duplicate.”
According to both Mr. Weigand and Mr. Wood, the name Case Closed will continue on as the product brand, given its widespread popularity and loyal customer base. Crime Tech Solutions is expected to retain all Case Closed employees, with Mr. Weigand joining as the company’s chief technical officer.
Crime Tech Solutions says it expects continued growth via ongoing software sales and strategic acquisitions.
About Crime Tech Solutions
(NOTE: Crime Tech Solutions is an Austin, TX based provider of crime and fraud analytics software for commercial and law enforcement groups. Our offerings include sophisticated Case Closed™ investigative case management and major case management, GangBuster™ gang intelligence software, powerful link analysis software, evidence management, mobile applications for law enforcement, comprehensive crime analytics with mapping and predictive policing, and 28 CFR Part 23 compliant criminal intelligence database management systems.)
Tag Archives: Palantir Technologies
Is the Most Dangerous Company in America?
Posted by Tyler Wood, Operations Manager at Crime Tech Solutions
 This is a very interesting read about the current big data analytics darling, Palantir Technologies. The article from GS Early appears on the Personal Liberty website HERE.
This is a very interesting read about the current big data analytics darling, Palantir Technologies. The article from GS Early appears on the Personal Liberty website HERE.
The original article follows…
“I was reading my newsfeeds and I came across a very interesting story about this highly secretive company that is apparently buying up as much Palo Alto, California real estate as it can get its hands on.
But that isn’t even the most interesting thing about them. What piques my interest is how this start-up that just added another $450 million to its funding — it now has about $20 billion in funding — got its money.
The company is called Palantir Technologies. If the name sounds familiar, it’s because it comes from JRR Tolkein’s trilogy of fantasy novels. In The Fellowship of the Ring, Saruman the wizard uses the Palantir of Orthanc, an indestructible sphere of dark crystal, to see into the future and communicate across the world.
That sounds geeky and innocuous enough, no?
But Palantir the company’s biggest clients are the FBI, SEC and the CIA. It is a Big Data company that also has corporate clients, but much of the work — from what anyone can tell — comes from hush-hush projects for the U.S. intelligence community.
This crystal ball of a company sounds less like a quaint fantasy than a key element of the “thought police” in Philip K. Dick’s dark science fiction tale “The Minority Report.”
In “The Minority Report,” the police used computers to predict when and where a crime would occur and apprehend the perpetrator before he actually committed the crime.
The crazy thing is, we’re now living in a world where Big Data makes that possible.
First, let me explain what Big Data is. Basically, now that our lives are completely recorded in various media — traffic cameras, debit card transactions, loyalty cards, phone calls, television shows watched, internet, social media, SMS texts, etc. — computers are powerful enough now to sort through all this data from all these sources and come up with predictive patterns for individuals and groups.
This is a very hot area for retail stores. But it also has enormous implications in a variety of industries; and many of them are helpful.
It is certainly a tool that law enforcement and our intelligence services would find valuable to root out potential terrorists or groups that are planning some terrorist act. It is also useful to find people who are attempting to elude authorities. And being able to get ahead of the some of the more devious players on Wall Street and their illegal trading schemes would be nice.
But you can see where this could be turned on Americans, just as easily as the NSA turned its endeavors on to less than righteous paths.
Palantir is raising eyebrows in the epicenter of digital startups because most companies, once they reach a certain size, move out of Palo Alto and build a campus in some surrounding town.
Not Palantir. It now owns about 10-15 percent of all the available space in Palo Alto, more than 250,000 square feet. It is the fourth most valuable venture backed company in the world.
The irony in the article was, the concern wasn’t about its biggest client or what it’s doing for the CIA, it was the fact that it’s eating up all the available commercial space in Palo Alto and not leaving room for new startups.
My concern is a bit deeper. The CIA could have quietly gone to one of the major Big Data firms like Accenture or IBM and worked with them on whatever it is they needed. But instead they essentially built their own company, where there are much fewer people to throw up roadblocks to the work being done. I have no problem with government using Big Data to protect us; my concern is when intelligence and enforcement agencies have unfettered use of it.
But, there’s no turning back the clock. We are in the Big Data, cybersecurity age and plenty of these companies already exist. Usually their goal is help their clients sell more lavender soap in February or figure out what kind of salad greens a 37-year-old mother of two prefers to buy at 7 p.m. on a Wednesday evening.
On a fundamental level, it’s best to keep your digital footprint light. Make sure you have secure passwords that aren’t just 1234 or your pet’s name. Most browsers have an “incognito” mode that won’t track your browser history. But truth be told, if someone really wants your history, they can get it.
If you’re more serious about hiding your footprints, look into encrypted services like Tor (www.torproject.com) that will protect against traffic analysis (browser history, instant messaging, etc.). It’s free and very good.
Transactions in bitcoins is a way to keep your footprint light in the marketplace.
And if you’re looking to make money on the trend, there are any number of companies that are at the forefront of cybersecurity (Palo Alto Networks, FireEye, Synamtec) and Big Data (Accenture, IBM, Teradata, Oracle).
–GS Early“
(NOTE: Crime Tech Solutions is an Austin, TX based provider of crime and fraud analytics software for commercial and law enforcement groups. We proudly support the Association of Certified Fraud Examiners (ACFE), International Association of Chiefs of Police (IACP), Association of Law Enforcement Intelligence Units (LEIU) and International Association of Crime Analysts (IACA). Our offerings include sophisticated link analysis software, comprehensive crime mapping and predictive policing, and criminal intelligence database management systems.)
Link Analysis and Crime – An examination.
Posted by Tyler Wood, Operations Manager at Crime Tech Solutions
 The topic of fraud is widely discussed, and the focus of thousands upon thousands of articles. Television shows such as Crime, Inc and American Greed have become popular due, in part, to our fascination with the topic of fraud.
The topic of fraud is widely discussed, and the focus of thousands upon thousands of articles. Television shows such as Crime, Inc and American Greed have become popular due, in part, to our fascination with the topic of fraud.
The organizations that are affected by fraud are also fascinated… but for entirely different reasons. Some estimates suggest that the US economy loses 11 trillion dollars each year due to one form of fraud or another. It’s little wonder, therefore, that the companies most frequently defrauded have been heavily investing in anti-fraud technologies at an increasing rate over the past decade or more.
The biggest problem with fraud, of course, is that it is always evolving in a very Darwinian fashion. Like a living, breathing entity, fraud schemes change over time in order to survive. As the targets of fraud schemes put new policies, procedures and/or systems to deter the activities, the schemes modify and find new ways to survive.
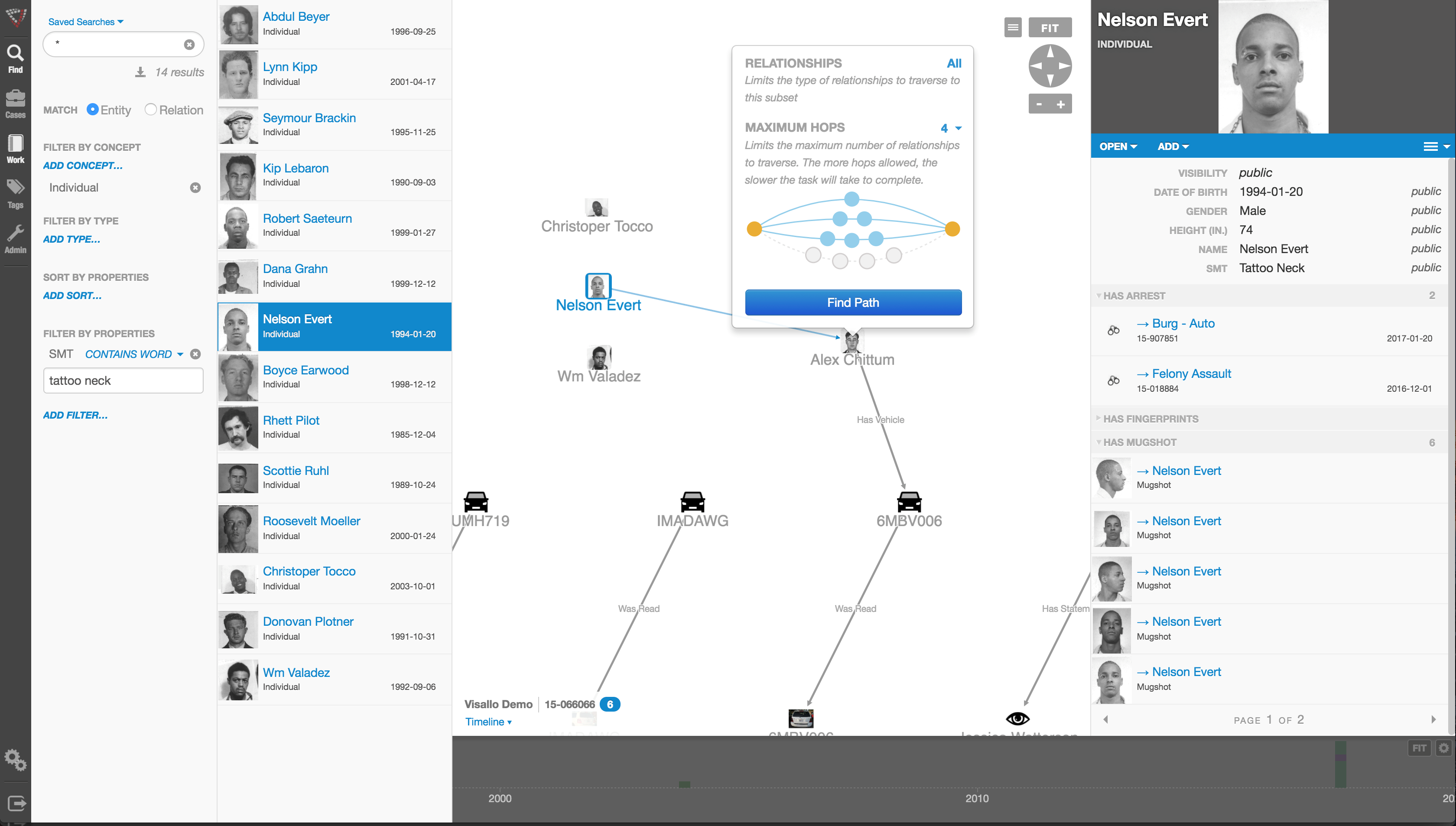
So, since the nature of criminal activity is such that they constantly change, how do investigators find a fool proof methodology to ensure they are 100% safe from them? The answer, of course, is that they can’t. They never will; at least not until we live in a world such as the one depicted in the 2002 film Minority Report, starring Tom Cruise. In that movie, criminals are arrested prior to committing a crime based upon the predictions of psychics called ‘Precogs’. Corporations and individual targets of fraud can only wish.
Nope, there are no Precogs running around locking up would-be practitioners of fraud that would protect banks, insurance companies, Medicaid and Medicare programs, victims of Ponzi schemes, victims of identity theft, and countless others. Instead, organizations rely upon skilled knowledge workers using purpose-built crime and fraud analytics technology that can detect anomalies in patterns, suspicious transactions, hotspot mapping, networks of fraudsters, and other sophisticated data analytics tools.
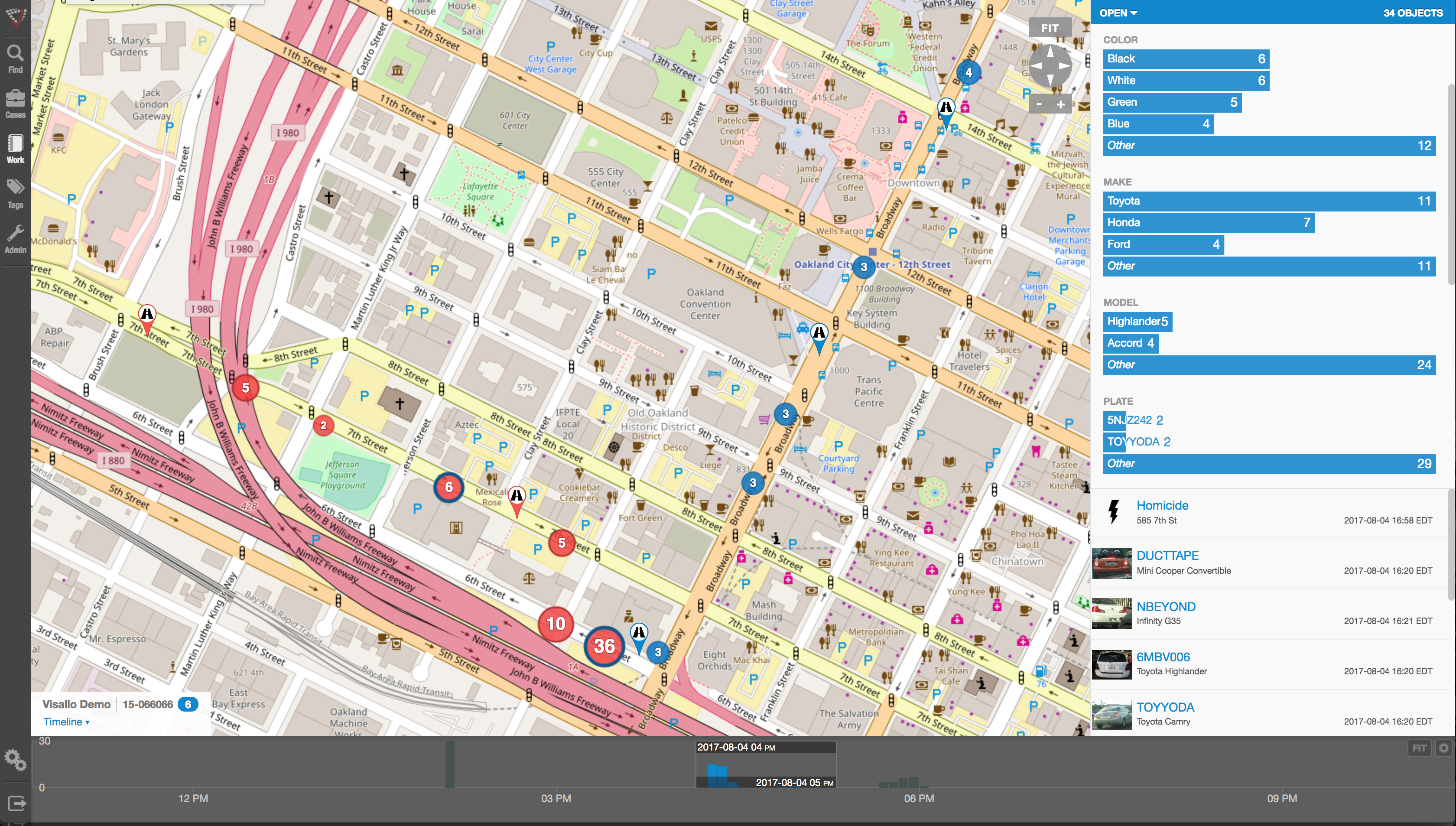
Crime and fraud analytics
Any discussion of analytics and investigation software must touch upon the topic of ‘big data’. No longer just a buzz word, big data literally fuels the insights gathered by organizations in every area of business. Naturally, then, organizations who have been traditionally targeted by fraudsters have increasingly invested in crime technology such as investigation software and analytics in order to exploit the phenomenon.
 Of course, big data in and by itself does nothing. It just sits there. Nobody has ever yelled “Help! We’ve been defrauded! Call the big data!” Big data is only useful when it can be transformed into ‘smart data’. In other words, understanding the big picture of costly fraudulent activities is not akin to understanding the specifics of ‘who’ is defrauding you, and ‘how’ they are doing it.
Of course, big data in and by itself does nothing. It just sits there. Nobody has ever yelled “Help! We’ve been defrauded! Call the big data!” Big data is only useful when it can be transformed into ‘smart data’. In other words, understanding the big picture of costly fraudulent activities is not akin to understanding the specifics of ‘who’ is defrauding you, and ‘how’ they are doing it.
Those questions can best be answered through the powerful data mining and link analysis software tools offered by Austin, TX based Crime Tech Solutions in partnership with Sterling, VA based Visallo. Effective link analysis complements big data analytics platforms, helping to expose previously undetected fraud, and the entities (people or organizations) committing it.
Link Analysis – Transforming big data into smart data
By definition, link analysis is a data analysis technique that examines relationships among people, places, and things. As a visual tool, link analysis provides users a powerful method to quickly understand and ‘see’ what is happening. Because of this, it is widely used by financial institutions such as banks and insurance companies to uncover criminal networks, improve fraud investigations, detect insider fraud, and expose money laundering schemes. Similarly, government agencies use link analysis to investigate fraud, enhance screening processes, uncover terrorist networks and investigate criminal activities.
At Crime Tech Solutions, we liken the question of how to detect and deter fraud to ‘How do you eat an elephant?’ The answer, of course, is one bite at a time. If big data is the elephant, comprehensive link analysis software is part of the one ‘bite’ at a time. Or should we say ‘byte’.
(NOTE: Crime Tech Solutions is an Austin, TX based provider of investigation software and analytics for commercial and law enforcement groups. We proudly support the Association of Certified Fraud Examiners (ACFE), International Association of Chiefs of Police (IACP), Association of Law Enforcement Intelligence Units (LEIU) and International Association of Crime Analysts (IACA). Our offerings include sophisticated link analysis software, an industry-leading investigation case management solution, and criminal intelligence database management systems.)
IBM Crime Analytics: Missing the mark? CTS Hits the bullseye!
 Posted by Crime Tech Solutions – Your source for analytics in the fight against crime and fraud.
Posted by Crime Tech Solutions – Your source for analytics in the fight against crime and fraud.
September 7, 2015. IBM announced this week a major update to its IBM i2 Safer Planet intelligence portfolio that includes a major overhaul of the widely used Analyst’s Notebook product. The product, which has become increasingly abandoned by its user base over the past five years, is now being positioned as ‘slicker‘ than previous versions.
IBM suggests that the new version scales from one to 1,000 users and can ingest petabytes of information to visualize. (A single petabyte roughly translates to 20,000,000 four-drawer filing cabinets completely filled with text).
That’s a lot of data. Seems to me that analysts are already inundated with data… now they need more?
This all begs the question: “Where is IBM headed with this product?”
The evidence seems to point to the fact that IBM wants this suite of products to compete head-to-head with money-raising machine and media darling Palantir Technologies. If I’m IBM, that makes sense. Palantir has been eating Big Blue’s lunch for a few years now, particularly at the lucrative US Federal market level. Worse yet, for IBM i2, is the recent news of a new competitor with even more powerful technology.
If I’m a crime or fraud analyst, however, I have to view this as IBM moving further and further away from my reality.
The reality? Nobody has ever yelled “Help! I’ve been robbed. Call the petabytes of ‘slick’ data!” No, this tiring ‘big data’ discussion is not really part of the day to day work for the vast majority of analysts. Smart people using appropriate data with intuitive and flexible crime technology solutions… that’s the reality for most of us.
So, as IBM moves their market-leading tool higher and higher into the stratosphere, where does the industry turn for more practical desktop solutions with realistic pricing? For more and more customers around the world, the answer is a crime and fraud link analytics tool from Crime Tech Solutions.
No, it won’t ingest 20,000,000 four-drawer filing cabinets of data, and it’s more ‘efficient‘ than ‘slick‘. Still, the product has been around for decades as a strong competitor to Analysts Notebook, and is well-supported by a network of strategic partners around the world. Importantly, it is the only American made and supported alternative. Period. It’s also, seemingly, the last man standing in the market for efficient and cost-effective tools that can be used by real people doing their real jobs.
Asking data questions
Posted by Douglas Wood, Editor. http://www.linkedin.com/in/dougwood.
A brief read and good perspective from my friend Chris Westphal of Raytheon. The article is by Anna Forrester of ExecutiveGov.com.
Federal managers should invest in technology that would help them extract insights from data and base their investment decision on the specific problems and information they want to learn and solve, Federal Times reported Friday.
Rutrell Yasin writes that the above managers should follow three steps as they seek to compress the high volume of data their agencies encounter in daily tasks and to derive value from them.
According to Shawn Kingsberry, chief information officer for the Recovery Accountability and Transparency Board, federal managers should first determine the questions they need to ask of data then create a profile for the customer or target audience.
Next, they should locate the data and their sources then correspond with those sources to determine quality of data, the report said. “Managers need to know if the data is in a federal system of records that gives the agency terms of use or is it public data,” writes Yasin.
Finally, they should consider the potential impact of the data, the insights and resulting technology investments on the agency.
Yasin reports that the Recovery Accountability and Transparency Board uses data analytics tools from Microsoft, SAP and SAS and link analysis tools from Palantir Technologies.
According to Chris Westphal, director of analytics technology at Raytheon, organizations should invest in a platform that gathers data from separate sources into a single data repository with analytics tools.
Yasin adds that agencies should also appoint a chief data officer and data scientists or architects to assist the CIO and CISO on these areas.
Part 2: Investigating the Investigations – X Marks the Spot
Posted by Douglas Wood, Editor. http://www.linkedin.com/in/dougwood
Part One of this series is HERE.
Most of the financial crimes investigators I know live in a world where they dream of moving things from their Inbox to their Outbox. Oh, like everyone else, they also dream about winning the lottery, flying without wings, and being naked in public. But in terms of the important roles they perform within both public and private sectors, there is simply Investigating (Inbox) and Adjudication (Outbox). Getting there requires a unique blend of their own capabilities, the availability of data, and the technology that allows them to operate. In the diagram below, ‘X‘ marks the spot where crimes are moved from the Inbox to the Outbox. Without any of those three components, an investigation becomes exponentially more difficult to conclude.
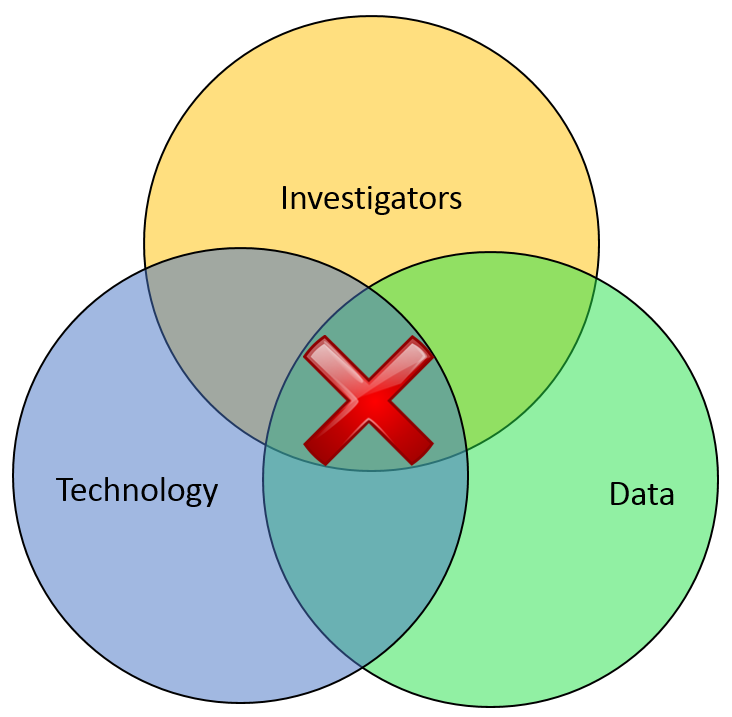
In part one of this article two weeks ago, I wrote about the Investigation Management & Adjudication (IMA) side of financial crimes investigations. I coined that term to call out what is arguably the most integral component of any enterprise fraud management (EFM) ecosystem. The original EFM overview is here.
“The job is almost unrecognizable to those who once used rotary phones in smoke filled offices…
Twenty years ago, IMA was based primarily upon human eyes. Yes, there were technology tools available such as Wordperfect charts and Lotus 1-2-3 spreadsheets, but ultimately it was the investigator who was tasked with finding interesting connections across an array of data elements including handwritten briefs, telephone bills, lists of suspect information, and discussions with other investigators. The job got done, though. Things moved from the Inbox to the Outbox, arrests were made and prosecutions were successful. Kudos, therefore, to all of the investigators who worked in this environment.
Fast forward to today, and the investigator’s world is dramatically different. The job is the same, of course, but the tools and mass availability of data has made the job almost unrecognizable to those who once used rotary phones in smoke filled offices. Organizations began building enterprise data warehouses designed to provide a single version of the truth. Identity Resolution technology was implemented to help investigators recognize similarities between entities in that data warehouse. And today, powerful new IMA tools are allowing easy ingestion of that data, improved methods for securely sharing across jurisdictions, automated link discovery, non-obvious relationship detection, and interactive visualization tools, and -importantly – packaged e-briefs which can be understood and used by law enforcement, prosecutors, or adjudication experts.
“Without any of these components, everything risks falling to the outhouse…
With all these new technologies, surely the job of the Investigator is becoming easier? Not so fast.
IMA tools – and other EFM tools – do nothing by themselves. The data – big data – does nothing by itself. It just sits there. The best investigators – without tools or data – are rendered impotent. Only the combination of skilled, trained investigators using the best IMA tools to analyze the most useful data available results in moving things from the Inbox to the Outbox. Without any of these components… everything eventually risks falling to the Outhouse.
Kudos again, Mr. and Mrs. Investigator. You’ll always be at the heart of every investigation. Here’s hoping you solve for X every day.
Investigating the Investigations.
Posted by Douglas Wood, Editor.
A few years ago, I read a book called Fraud Analytics by Delena Spann. Ms. Spann is with the U.S. Secret Service, Electronic & Financial Crimes Task Force. The book is an overview of investigation analytics with specific information about some former technology leaders in this area.
The IBM i2 toolset is discussed, along with offerings from Raytheon, Centrifuge, and SAS, and FMS’ Link Analytics, and others. (My friend Chris Westphal, formerly of Raytheon Visual Analytics, by the way, published his book ‘Data Mining for Intelligence, Fraud & Criminal Detection’ a few years ago and is another one I strongly recommend.)
Both books offer advice and use cases on how technology can be applied in the fight against crime. A few months ago, I summarized the types of technology being put to use as tools to prevent, detect, and investigate fraud and other criminal activities. (It’s worth a quick read.) What I’m investigating today, however, is… well, investigations.
“IMA is the most critical connection between technology and investigators.”
In my technology summary, I termed this area Investigation Management & Adjudication (IMA). IMA is the most critical connection between technology and humans within an enterprise fraud management ecosystem. Incorporating key elements of enterprise case management, collaboration, link visualization, information dissemination and knowledge discovery, this layer of functionality is designed to uncover insights which aid in investigating complex incidents. The result ought to be actionable visualization of critical entities, and documented results for potential litigation and regulatory compliance.
IBM i2 has long been considered a thought and market leader in this segment – deservedly or not. Palantir Technologies plays in this area as well. Perhaps no company is more in tune with this market, though, than Visallo with their leading investigation analytics platform. Each platform clearly adds value to investigation case management solutions by providing powerful, emerging functionalities that allow easy and intuitive consumption of data in any form. For investigators, the more data – and the easier that data is to consume – the better.
“Users want actionable intelligence, not endless queries.”
What makes for good IMA? A few things, actually. First among them is the technology’s ability to adapt to the way human beings think and act. Users want actionable intelligence, not endless queries. IMA tools, therefore, ought to interact with the investigator in a consultative way that a fellow investigator would. “Hey, have you thought about this, Mr. Investigator?” and “Maybe you should look at that.”
Second, IMA ought to have context. Technologies that simply point to two entities and say, ‘Hey these things look linked‘ are great but leave all of the thinking up to Mr. Investigator. The IMA tools that I like have contextual values associated to those links. ‘Hey, these things look linked AND here’s why that’s important’. Big difference.
Third, IMA should bring the investigations to closure. There are a lot of data mining tools out there that allow querying with case management. How, though, does the investigator get to the point where an investigation is solved and prosecutable? Once again, the most functional IMA products act the way humans do. They package up the results of the investigation in an easy-to-comprehend document that can be shared internally or with police. No loose ends.
“Every investigation ends with an investigator.”
Predictive analytics, big data, and real-time alert scoring are the current industry buzzwords. They should be. They’re important. At the end of the day, however, every investigation ends with an investigator. Putting the right tools in their hands is often the difference between success and failure in an entire enterprise investigation system.
That’s precisely what Crime Tech Solutions, LLC does. Please take a moment to look us over.
Part Two of this series is now available HERE.