This is Part 1 of a series dedicated to the science (and art) of managing Major Criminal Cases in law enforcement. In order to begin a discussion on this subject, though, it’s important to define what makes an investigation a Major Case Investigation in the first place.
My friend, Chief Dan McDevitt, defines Major Case Management in his popular book ‘Major Case Management: A Guide for Law Enforcement Managers‘ as follows:
“A Major Case is a real or suspected crime of such severity that it creates an intense public demand for identification, apprehension, and prosecution of the offender(s).”
– Chief Daniel McDevitt
Irrespective of how your own definition may vary from Chief Dan’s, this much is simple; Major Cases are serious criminal matters. The degree of ‘seriousness’, however, is almost entirely relative. A stabbing in Chicago may not, by itself, be ‘serious’ as viewed by the public at large. Conversely, a sexual assault on a small University Campus may be extremely ‘serious’.
Make no mistake… neither are good or acceptable, and both are, of course, unthinkable violations. The point here is that cases may be Major Cases (or not) by virtue of the relative socio-economic environment in which they are being investigated.

Attributes of a Major Case. You probably have a Major Case when..
All of that said, there are several attributes which are common in major case investigations:
- Resource Requirements – The amount of resources that an investigation unit must devote to a Major Case is substantial… far more than the average investigative case. This would include additional officers, overtime, forensics work, and the like. If your budget is shot in one fell swoop… you probably have a Major Case on your hands.
- Big Brother is Watching – Maybe the Mayor is involved. Maybe the ACLU. Black Lives Matter? The NRA, even. Major Cases are often associated with major non-law enforcement interest from groups claiming to be stakeholders. If Al Sharpton, Wayne LaPierre, or AG Jeff Sessions have chimed in… you probably have a Major Case on your hands.
- All Hands on Deck – Major Cases tend to redefine titles and organizational roles. Many of the Chiefs and Sheriffs I have interviewed on this topic describe pulling all types of duty assignments. Patrol officers become Detectives, who become Media Relations, and so on. If the chief cook is washing bottles… you probably have a Major Case on your hands.
- Media Attention – Many Major Cases capture the attention of the public and, subsequently, the media. In many cases, a local case can turn viral and suddenly there’s a CNN mobile satellite truck parked outside. What makes an investigation viral isn’t always clear, but it’s discussed HERE in some detail. If Wolf Blitzer calls your investigation ‘Breaking News’… you probably have a Major Case on your hands.
- There are Multiple Jurisdictions Involved – Because of the possible complexities of Major Cases, they quite often involve multiple agencies. Task Forces are regularly utilized in Major Cases, and are comprised of any number of people from across different law enforcement agencies, making the problem of staying organized even harder. Perhaps the City PD is working to support the local Sheriff’s Office – or vice versa. Maybe the State Bureau of Investigation is involved. Maybe the FBI. If you need ‘Hello My Name Is…” stickers during your case review… you probably have a Major Case on your hands.
Having placed some parameters around what defines a Major Case, we will look deeper into the unique problems associated with these types of investigations. Stay tuned for Part Two of this series.
 Douglas Wood is CEO of Crime Technology Solutions | Case Closed Software, a leading provider of serious investigation software to law enforcement, state bureaus, DA offices, and other investigative units. Doug can be reached directly HERE.
Douglas Wood is CEO of Crime Technology Solutions | Case Closed Software, a leading provider of serious investigation software to law enforcement, state bureaus, DA offices, and other investigative units. Doug can be reached directly HERE.


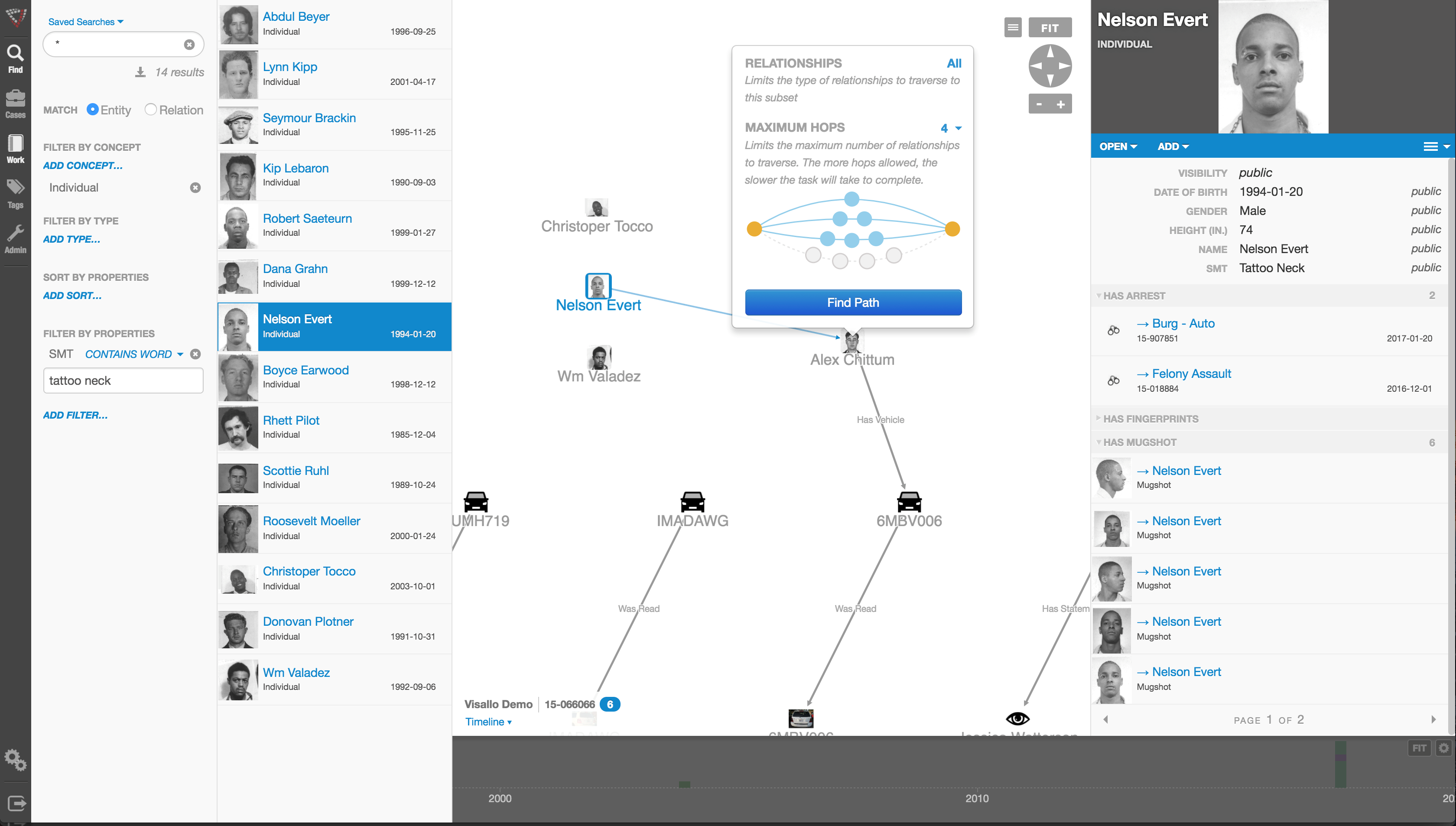
 Here’s an excellent, must-read article from Andrew Guthrie Ferguson, a Professor of Law at the
Here’s an excellent, must-read article from Andrew Guthrie Ferguson, a Professor of Law at the  Case Closed Software™
Case Closed Software™
 Great article from our friends at
Great article from our friends at 

 Posted by Tyler Wood, Director of Operations at Case Closed Software.
Posted by Tyler Wood, Director of Operations at Case Closed Software.
 The notion that law enforcement fusion centers regularly violate individuals’ privacy rights as they capture intelligence on gangs, terrorist activities, organized crime, and other threats to public safety is simply not true. That, according to a study published in the
The notion that law enforcement fusion centers regularly violate individuals’ privacy rights as they capture intelligence on gangs, terrorist activities, organized crime, and other threats to public safety is simply not true. That, according to a study published in the 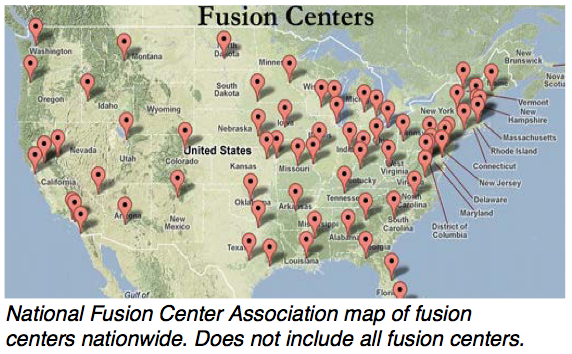 There are approximately 80 fusion centers in the United States. They were created in response to the 9/11 terrorist attacks. The attacks exposed the requirement for greater information sharing and improved intelligence capabilities at all law enforcement levels. According to the article’s author, the idea was to have the key pieces of data funneled into fusion centers so that highly trained analysts could stay atop of threats and correspond with local law enforcement agencies on these potential threats.
There are approximately 80 fusion centers in the United States. They were created in response to the 9/11 terrorist attacks. The attacks exposed the requirement for greater information sharing and improved intelligence capabilities at all law enforcement levels. According to the article’s author, the idea was to have the key pieces of data funneled into fusion centers so that highly trained analysts could stay atop of threats and correspond with local law enforcement agencies on these potential threats. The notion that law enforcement fusion centers represent ‘Big Brother’, and that data is being stored and disseminated about people irrespective of whether they are suspected of criminal activity is simply wrong, according to Professor Carter.
The notion that law enforcement fusion centers represent ‘Big Brother’, and that data is being stored and disseminated about people irrespective of whether they are suspected of criminal activity is simply wrong, according to Professor Carter. “Fusion centers are following the federal regulatory code, 28 CFR Part 23, that is the legal standard for collecting information,” Carter said. “That code says you have to establish a criminal predicate, basically probable cause, to keep information on identifiable individuals.”
“Fusion centers are following the federal regulatory code, 28 CFR Part 23, that is the legal standard for collecting information,” Carter said. “That code says you have to establish a criminal predicate, basically probable cause, to keep information on identifiable individuals.” Crime Tech Solutions
Crime Tech Solutions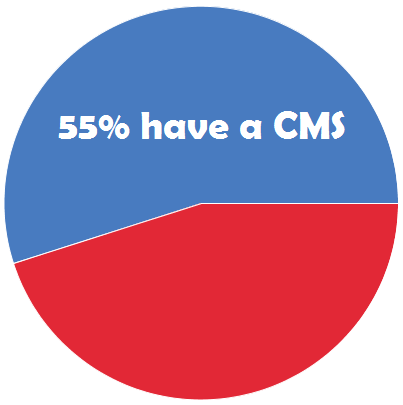 According to the study, just 55% of U.S. law enforcement agencies currently utilize investigative case management software (CMS), and the majority of users are unhappy with their current systems.
According to the study, just 55% of U.S. law enforcement agencies currently utilize investigative case management software (CMS), and the majority of users are unhappy with their current systems.