Posted by Tyler Wood, Operations Manager at Crime Tech Solutions
 The topic of fraud is widely discussed, and the focus of thousands upon thousands of articles. Television shows such as Crime, Inc and American Greed have become popular due, in part, to our fascination with the topic of fraud.
The topic of fraud is widely discussed, and the focus of thousands upon thousands of articles. Television shows such as Crime, Inc and American Greed have become popular due, in part, to our fascination with the topic of fraud.
The organizations that are affected by fraud are also fascinated… but for entirely different reasons. Some estimates suggest that the US economy loses 11 trillion dollars each year due to one form of fraud or another. It’s little wonder, therefore, that the companies most frequently defrauded have been heavily investing in anti-fraud technologies at an increasing rate over the past decade or more.
The biggest problem with fraud, of course, is that it is always evolving in a very Darwinian fashion. Like a living, breathing entity, fraud schemes change over time in order to survive. As the targets of fraud schemes put new policies, procedures and/or systems to deter the activities, the schemes modify and find new ways to survive.
So, since the nature of criminal activity is such that they constantly change, how do investigators find a fool proof methodology to ensure they are 100% safe from them? The answer, of course, is that they can’t. They never will; at least not until we live in a world such as the one depicted in the 2002 film Minority Report, starring Tom Cruise. In that movie, criminals are arrested prior to committing a crime based upon the predictions of psychics called ‘Precogs’. Corporations and individual targets of fraud can only wish.
Nope, there are no Precogs running around locking up would-be practitioners of fraud that would protect banks, insurance companies, Medicaid and Medicare programs, victims of Ponzi schemes, victims of identity theft, and countless others. Instead, organizations rely upon skilled knowledge workers using purpose-built crime and fraud analytics technology that can detect anomalies in patterns, suspicious transactions, hotspot mapping, networks of fraudsters, and other sophisticated data analytics tools.
Crime and fraud analytics
Any discussion of analytics and investigation software must touch upon the topic of ‘big data’. No longer just a buzz word, big data literally fuels the insights gathered by organizations in every area of business. Naturally, then, organizations who have been traditionally targeted by fraudsters have increasingly invested in crime technology such as investigation software and analytics in order to exploit the phenomenon.
 Of course, big data in and by itself does nothing. It just sits there. Nobody has ever yelled “Help! We’ve been defrauded! Call the big data!” Big data is only useful when it can be transformed into ‘smart data’. In other words, understanding the big picture of costly fraudulent activities is not akin to understanding the specifics of ‘who’ is defrauding you, and ‘how’ they are doing it.
Of course, big data in and by itself does nothing. It just sits there. Nobody has ever yelled “Help! We’ve been defrauded! Call the big data!” Big data is only useful when it can be transformed into ‘smart data’. In other words, understanding the big picture of costly fraudulent activities is not akin to understanding the specifics of ‘who’ is defrauding you, and ‘how’ they are doing it.
Those questions can best be answered through the powerful data mining and link analysis software tools offered by Austin, TX based Crime Tech Solutions in partnership with Sterling, VA based Visallo. Effective link analysis complements big data analytics platforms, helping to expose previously undetected fraud, and the entities (people or organizations) committing it.
Link Analysis – Transforming big data into smart data
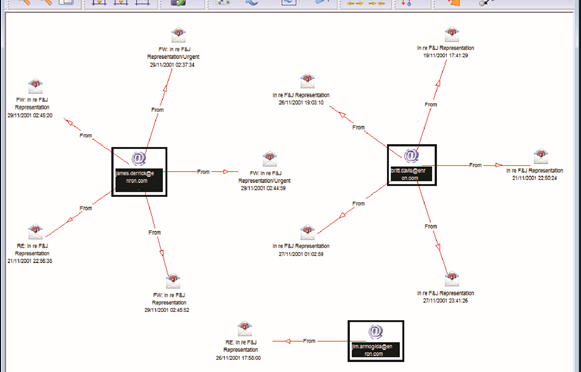
By definition, link analysis is a data analysis technique that examines relationships among people, places, and things. As a visual tool, link analysis provides users a powerful method to quickly understand and ‘see’ what is happening. Because of this, it is widely used by financial institutions such as banks and insurance companies to uncover criminal networks, improve fraud investigations, detect insider fraud, and expose money laundering schemes. Similarly, government agencies use link analysis to investigate fraud, enhance screening processes, uncover terrorist networks and investigate criminal activities.
At Crime Tech Solutions, we liken the question of how to detect and deter fraud to ‘How do you eat an elephant?’ The answer, of course, is one bite at a time. If big data is the elephant, comprehensive link analysis software is part of the one ‘bite’ at a time. Or should we say ‘byte’.
(NOTE: Crime Tech Solutions is an Austin, TX based provider of investigation software and analytics for commercial and law enforcement groups. We proudly support the Association of Certified Fraud Examiners (ACFE), International Association of Chiefs of Police (IACP), Association of Law Enforcement Intelligence Units (LEIU) and International Association of Crime Analysts (IACA). Our offerings include sophisticated link analysis software, an industry-leading investigation case management solution, and criminal intelligence database management systems.)
Tag Archives: fraud
The Name Game Fraud
 Posted by Douglas Wood, Editor. Alright everybody, let’s play a game. The name game!
Posted by Douglas Wood, Editor. Alright everybody, let’s play a game. The name game!
“Shirley, Shirley bo Birley. Bonana fanna fo Firley. Fee fy mo Mirley. Shirley!” No, not THAT name game. (Admit it… you used to love singing the “Chuck” version, though.)
The name game I’m referring to is slightly more sinister, and relates to the criminal intent to deceive others for gain by slightly misrepresenting attributes in order to circumvent fraud detection techniques. Pretty much anywhere money, goods, or services are dispensed, folks play the name game.
Utilities, Insurance, Medicaid, retail, FEMA. You name it.
Several years ago, I helped a large online insurance provider determine the extent to which they were offering insurance policies to corporations and individuals with whom they specifically did not want to do business. Here’s what the insurer knew:
- They had standard application questions designed to both determine the insurance quote AND to ensure that they were not doing business with undesirables. These questions included things such as full name, address, telephone number, date of birth, etc… but also questions related to the insured property. “Do you live within a mile of a fire station?”, Does your home have smoke detectors?”, and “Is your house made of matchsticks?”
- On top of the questions, the insurer had a list of entities with whom the knew they did not want to do business for one reason or another. Perhaps Charlie Cheat had some previously questionable claims… he would have been on their list.
In order to circumvent the fraud prevention techniques, of course, the unscrupulous types figured out how to mislead the insurer just enough so that the policy was approved. Once approved, the car would immediately be stolen. The house would immediately burn down, etc.
The most common way by which the fraudsters misled the insurers was a combination of The Name Game and modifying answers until the screening system was fooled. Through a combination of investigative case management and link analysis software, I went back and looked at several months of historical data and found some amazing techniques used by the criminals. Specifically, I found one customer who made 19 separate online applications – each time changing just one attribute or answer slightly – until the policy was issued. Within a week of the policy issue, a claim was made. You can use your imagination to determine if it was a legitimate claim. 😀
This customer, Charlie Cheat (obviously not his real name), first used his real name, address, telephone number, and date of birth… and answered all of the screening questions honestly. Because he did not meet the criteria AND appeared on an internal watch list for having suspicious previous claims, his application was automatically denied. Then he had his wife, Cheri Cheat, complete the application in hopes that the system would see a different name and approve the policy. Thirdly, he modified his name to Charlie Cheat, Chuck E. Cheat, and so on. Still no go. His address went from 123 Fifth Street to 123-A 5th Street. You get the picture.
Then he began to modify answers to the screening questions. All of a sudden, he DID live within a mile of a fire station… and his house was NOT made of matchsticks… and was NOT located next door to a fireworks factory. After almost two dozen attempts, he was finally issued the policy under a slightly revised name, a tweak in his address, and some less-than-truthful answers on the screening page. By investing in powerful investigative case management software with link analysis and fuzzy matching this insurer was able to dramatically decrease the number of policies issued to known fraudsters or otherwise ineligible entities.
Every time a new policy is applied for, the system analyzes the data against previous responses and internal watch lists in real time. In other words, Charlie and Cheri just found it a lot more difficult to rip this insurer off. These same situations occur in other arenas, costing us millions annually in increased taxes and prices. So, what happened to the Cheats after singing the name game?
Let’s just say that after receiving a letter from the insurer, Charlie and Cheri started singing a different tune altogether.
Using Link Analysis to untangle fraud webs
Posted by Douglas Wood, Editor.
NOTE: This article originally appeared HERE by Jane Antonio. I think it’s a great read…
Link analysis has become an important technique for discovering hidden relationships involved in healthcare fraud. An excellent online source, FierceHealthPayer:AntiFraud, recently spoke to Vincent Boyd Bryant about the value of this tool for payer special investigations units.
A former biometric scientist for the U.S. Department of Defense, Bryant has 30 years of experience in law enforcement and intelligence analysis. He’s an internationally-experienced investigations and forensics expert who’s worked for a leading health insurer on government business fraud and abuse cases.
How does interactive link analysis help insurers prevent healthcare fraud? Can you share an example of how the tool works?
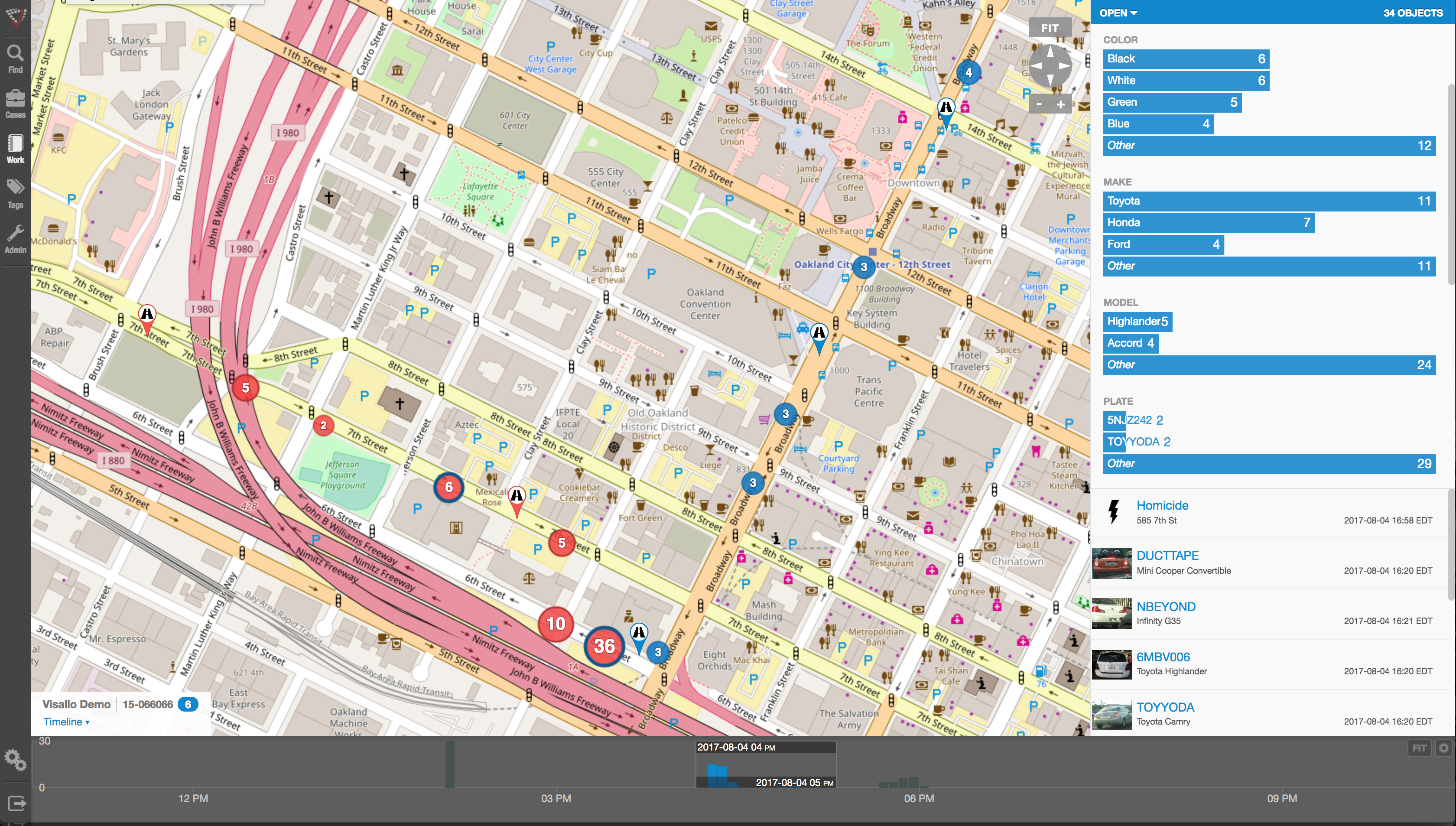
One thing criminals do best is hide pots of money in different places. As a small criminal operation becomes successful, it will often expand its revenue streams through associated businesses. Link analysis is about trying to figure out where all those different baskets of revenue may be. Insurers are drowning in a sea of theft. Here’s where link analysis becomes beneficial. Once insurers discover a small basket of money lost to a criminal enterprise, then serious research needs to go into finding out who owns the company, who they’re associated with, what kinds of business they’re doing and if there are claims associated with it.
You may find a clinic, for example, connected to and working near a pharmacy, a medical equipment supplier, a home healthcare services provider and a construction company. Diving into those companies and what they do, you find that they’re serving older patients for whom multiple claims from many providers exist. The construction company may be building wheelchair ramps on homes. And you may find that the providers are claiming payment for dead people. Overall, using this tool requires significant curiosity and a willingness to look beyond the obvious.
Any investigation consists of aggregating facts, generating impressions and creating a theory about what happened. Then you work to confirm or disconfirm your theory. It’s important to have tools that let you take large masses of facts and visualize them in ways that cue you to look closer.
Let’s say you investigate a large medical practice and interview “Doctor Jones.” The day after the interview, you learn through link analysis that he transferred $11 million from his primary bank account to the Cayman Islands. And in looking at Dr. Jones’ phone records, you see he called six people, each of whom was the head of another individual practice on whose board Dr. Jones sits. Now the investigation expands, since the timing of those phone calls was contemporaneous to the money taking flight.
Why are tight clusters of similar entities possible indicators of fraud, waste or abuse?
Bryant: When you find a business engaged in dishonest practices and see its different relationships with providers working out of the same building, this gives rise to reasonable suspicion. The case merits a closer look. Examining claims and talking to members served by those companies will give you an indication of how legitimate the operation is.
What are the advantages of link analysis to payer special investigation units, and how are SIUs using its results?
Bryant: Link analysis can define relationships through data insurers haven’t always had, data that traditionally belonged to law enforcement.
Link analysis results in a visual reference that can take many forms: It can look like a family tree, an organizational chart or a time line. This reference helps investigators assess large masses of data for clustering and helps them arrive at a conclusion more rapidly.
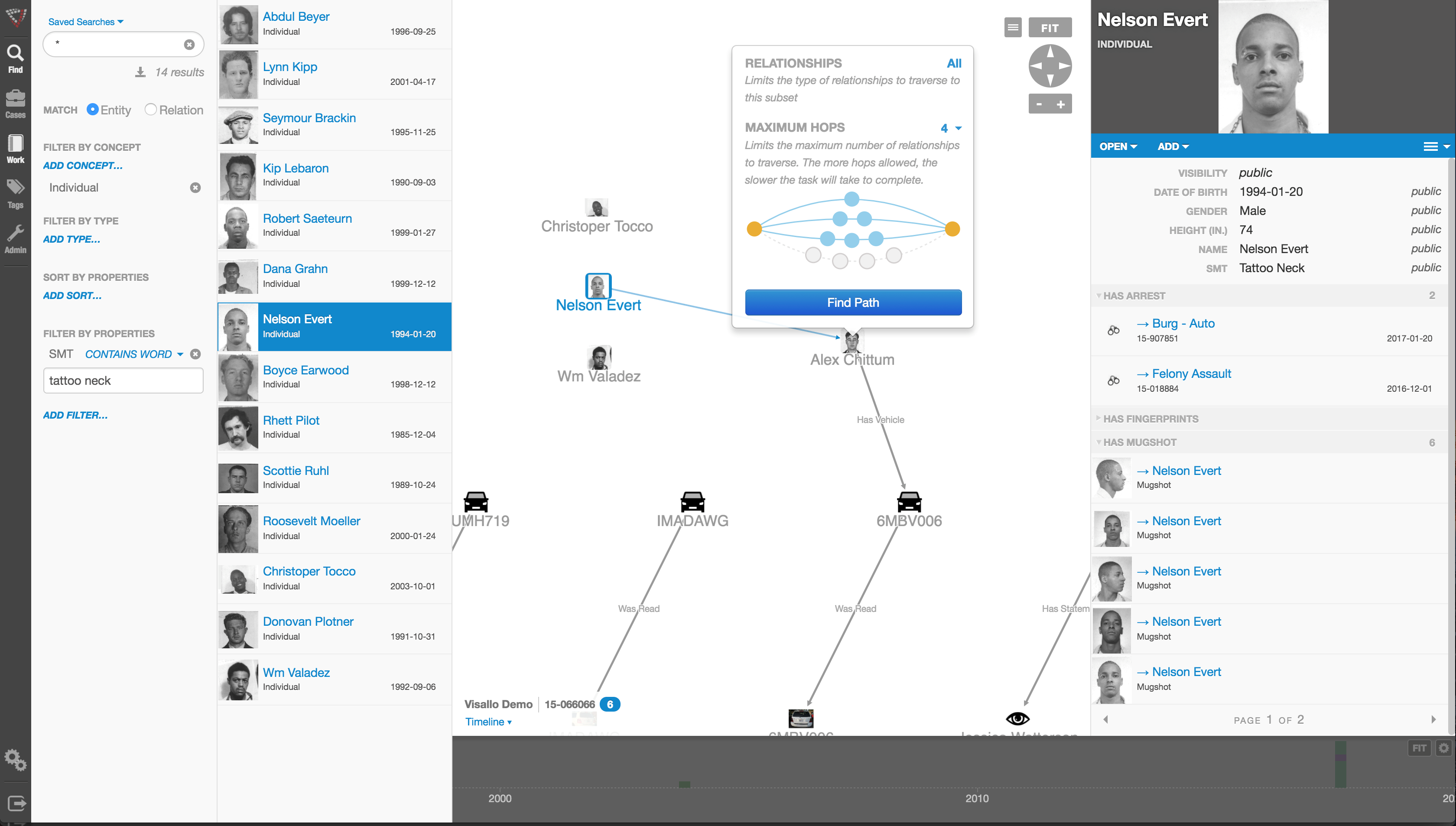
Using link analysis, an investigator can dump in large amounts of data–such as patient lists from multiple practices–and see who’s serving the same patient. This can identify those who doctor shop for pain medication, for example. Link analysis can chart where this person was and when, showing the total amount of medication prescribed and giving you an idea of how the person is operating.
What types of data does link analysis integrate?
Bryant: Any type of data that can be sorted and tied together can be loaded into the tool. Examples include telephone records, addresses, vehicle information, corporate records that list individuals serving on boards and banking and financial information. Larger supporting documents can be loaded and linked to the charts, making cases easier to present to a jury.
Linked analysis can pull in data from state government agencies, county tax records or police records from state departments of correction and make those available in one bucket. In most cases, this is more efficient than the hours of labor needed to dig up these types of public records through site visits.
Is there anything else payers should know about link analysis that wasn’t covered in the above questions?
Bryant: The critical thing is remembering that you don’t know what you don’t know. If a provider or member is stealing from the plan in what looks like dribs and drabs, insurers may never discover the true extent of the losses. But if–as a part of any fraud allegation that arises–you look at what and who is associated with the subject of the complaint, what started as a $100,000 questionable claims allegation can expose millions of dollars in inappropriate billings spread across different entities.
Perhaps a nice change at NICE Actimize?
Posted by Douglas Wood, Editor. http://www.linkedin.com/in/dougwood
Though not publicly released, news out of NICE Actimize is that long-time CEO Amir Orad is leaving the company effective May 1. Indicative of the ‘what a small world this is’ nature of the financial crimes technology marketplace, former Pegasystems co-founder and head of Americas for BAE Systems Detica, Joe Friscia, will be taking over the helm at that time.
Mr. Orad led NICE Actimize’s product and strategy functions prior to his five year tenure as CEO. During his tenure, he scaled the business size over six-fold. He is also a founding board member at BillGuard the venture backed personal finance analytics and security mobile app company.
Prior to Actimize, Orad was co-founder and CMO of Cyota a cyber security and payment fraud cloud company protecting over 100 million online users, acquired by RSA Security for $145M. Following the acquisition, he was VP Marketing at RSA.
I’ve known both Amir and Joe for several years, and have a tremendous amount of respect for both gentlemen. While it’s sad to see Amir leave the organization, I know that his rather large shoes will be more than adequately filled by Mr. Friscia.
Joe’s background is well-suited to this new position, and all of us here at FightFinancialCrimes wish him well. Joe joined Detica when BAE Systems acquired Norkom Technologies in early 2011, where he served as General Manager and Executive Vice President of the Americas. Joe led the rapid growth of Norkom in the Americas, with direct responsibility for sales, revenue and profit as well as managing multi-discipline teams based in North America. Prior to Norkom, Joe helped start Pegasystems Inc in 1984, a successful Business Process Management software company that went public in 1996.
Best of luck to Amir in his new ventures, and to Joe as he guides Actimize into it’s next phase.
Robbing the Casket, What Happens In Vegas, and Railroad Ripoffs: Selected Financial Crimes Snapshot 12/21/2013
To all of our readers… Have a great Christmas season and see you in 2014!
Posted by Douglas Wood, Editor. http://www.linkedin.com/in/dougwood
Another case of worker’s compensation premium fraud. You may recall my previous post on this subject. It’s worth reading.
http://manasquan.patch.com/groups/police-and-fire/p/owner-of-wallbased-roofing-company-indicted-for-fraud-and-theft
You’ve heard of robbing the cradle. This is robbing the casket, I suppose…
http://www.13abc.com/story/24279926/funeral-home-owner-charged-with-theft-fraud
He’ll have 8 years to choo choo choose a new way to make a living…
http://newyork.cbslocal.com/2013/12/21/8-years-in-prison-for-former-lirr-conductor-in-fraud-scheme/
What happens in Vegas… Stays in a federal penitentiary.
http://www.lasvegassun.com/news/2013/dec/20/man-gets-11-years-15-million-mortgage-fraud-scheme/
Bananas, Politicians and Navy Blue: Selected Financial Crimes Snapshot 01/02/2013
Posted by Douglas Wood, Editor. http://www.linkedin.com/in/dougwood
Be sure to check out “Investigating the Investigations” Part One and Two! In the meantime, here are this week’s weird headlines:
I can’t believe he tried to slip this one past investigators. Maybe he’ll win on a peel…
http://www.wjla.com/articles/2013/12/maurice-owens-to-appear-in-court-on-metro-banana-peel-fraud-charges-97541.html
A dishonest politician? Now I’ve heard everything!
http://www.wishtv.com/news/indiana/nw-indiana-politician-to-admit-6-wire-fraud-counts
He couldn’t just wait for Black Friday like everyone else?
http://www.hillsdale.net/article/20131202/NEWS/131209942
Navy blue about this one…
http://www.pbs.org/newshour/bb/military/july-dec13/navy_11-27.html
Investigating the Investigations.
Posted by Douglas Wood, Editor.
A few years ago, I read a book called Fraud Analytics by Delena Spann. Ms. Spann is with the U.S. Secret Service, Electronic & Financial Crimes Task Force. The book is an overview of investigation analytics with specific information about some former technology leaders in this area.
The IBM i2 toolset is discussed, along with offerings from Raytheon, Centrifuge, and SAS, and FMS’ Link Analytics, and others. (My friend Chris Westphal, formerly of Raytheon Visual Analytics, by the way, published his book ‘Data Mining for Intelligence, Fraud & Criminal Detection’ a few years ago and is another one I strongly recommend.)
Both books offer advice and use cases on how technology can be applied in the fight against crime. A few months ago, I summarized the types of technology being put to use as tools to prevent, detect, and investigate fraud and other criminal activities. (It’s worth a quick read.) What I’m investigating today, however, is… well, investigations.
“IMA is the most critical connection between technology and investigators.”
In my technology summary, I termed this area Investigation Management & Adjudication (IMA). IMA is the most critical connection between technology and humans within an enterprise fraud management ecosystem. Incorporating key elements of enterprise case management, collaboration, link visualization, information dissemination and knowledge discovery, this layer of functionality is designed to uncover insights which aid in investigating complex incidents. The result ought to be actionable visualization of critical entities, and documented results for potential litigation and regulatory compliance.
IBM i2 has long been considered a thought and market leader in this segment – deservedly or not. Palantir Technologies plays in this area as well. Perhaps no company is more in tune with this market, though, than Visallo with their leading investigation analytics platform. Each platform clearly adds value to investigation case management solutions by providing powerful, emerging functionalities that allow easy and intuitive consumption of data in any form. For investigators, the more data – and the easier that data is to consume – the better.
“Users want actionable intelligence, not endless queries.”
What makes for good IMA? A few things, actually. First among them is the technology’s ability to adapt to the way human beings think and act. Users want actionable intelligence, not endless queries. IMA tools, therefore, ought to interact with the investigator in a consultative way that a fellow investigator would. “Hey, have you thought about this, Mr. Investigator?” and “Maybe you should look at that.”
Second, IMA ought to have context. Technologies that simply point to two entities and say, ‘Hey these things look linked‘ are great but leave all of the thinking up to Mr. Investigator. The IMA tools that I like have contextual values associated to those links. ‘Hey, these things look linked AND here’s why that’s important’. Big difference.
Third, IMA should bring the investigations to closure. There are a lot of data mining tools out there that allow querying with case management. How, though, does the investigator get to the point where an investigation is solved and prosecutable? Once again, the most functional IMA products act the way humans do. They package up the results of the investigation in an easy-to-comprehend document that can be shared internally or with police. No loose ends.
“Every investigation ends with an investigator.”
Predictive analytics, big data, and real-time alert scoring are the current industry buzzwords. They should be. They’re important. At the end of the day, however, every investigation ends with an investigator. Putting the right tools in their hands is often the difference between success and failure in an entire enterprise investigation system.
That’s precisely what Crime Tech Solutions, LLC does. Please take a moment to look us over.
Part Two of this series is now available HERE.
Death Deterrents, Texas Teeth, and 'The Big Easy' Money – Selected Financial Crimes Snapshot 11/07/2013
Posted by Douglas Wood, Editor. http://www.linkedin.com/in/dougwood
Chinese woman sentenced to death for fraud. Ouch. That’s definitely a deterrent…
http://abcnews.go.com/International/wireStory/chinese-woman-sentenced-death-200m-fraud-20785445
70 year old Orthodontist sentenced to two years. Fraud laws in Texas have some real teeth in them…
http://www.kfdm.com/shared/news/top-stories/stories/kfdm_vid_7425.shtml
Think they’ll throw the (school) book at her?…
http://www.philly.com/philly/news/local/20131107_Charter_school_founder_s_fraud_trial_gets_underway.html
New Orleans cops charged. To Protect and Serve (themselves)…
http://www.wwltv.com/news/eyewitness/mikeperlstein/Two-NOPD-officers-have-first-court-date-on-payroll-fraud-issue-231068431.html
Drag Queens, Silk Road Shutdowns, and Video Killed the Real Estate Fraud – Selected Financial Crimes Snapshot 10/29/2013
Posted by Douglas Wood, Editor. http://www.linkedin.com/in/dougwood
Perhaps there is no Spanish term for “lay low, fraudster”?
http://www.latimes.com/local/lanow/la-me-ln-youtube-video-leads-to-arrest-of-man-wanted-in-fraud-case-20131010,0,1636077.story#axzz2j9ClBao3
Feds take down “eBay for drugs” site. I wonder if “Buy it Now” was popular?
http://krebsonsecurity.com/2013/10/feds-take-down-online-fraud-bazaar-silk-road-arrest-alleged-mastermind/
Drag Queen Shakedowns… Only on Bourbon Street.
http://theadvocate.com/news/7402011-123/celebrity-scam-artist-arrested-in
Shockers, Lawyers, and Worst Boss Ever – Selected Financial Crimes Snapshot 10/11/2013
Posted by Douglas Wood, Editor. http://www.linkedin.com/in/dougwood
Shipping a car to Nigeria? Seems like an awful lot of work for a fairly stupid scam…
http://finance.yahoo.com/news/fraud-conviction-man-reported-car-133000007.html
SHOCKER! Online advertising is often fraudulent!
http://www.sfgate.com/technology/businessinsider/article/4-Ad-Execs-Just-Admitted-That-Online-Adtech-Is-4888221.php
Why is it so darned hard to feel sorry for lawyers?
http://www.sun-sentinel.com/news/local/crime/fl-rothstein-attorney-arraign-20131011,0,4341539.story
“Here’s your paycheck. Gonna need half of it back, though.” Worst. Boss. Ever.
http://www.latimes.com/local/lanow/la-me-ln-contractor-indicted-fraud-wages-20131010,0,296609.story
Posted by Douglas G. Wood. Click on ABOUT for more information and follow Financial Crimes Weekly on Twitter @FightFinCrime