Posted by Douglas Wood, Editor. http://www.linkedin.com/in/dougwood
Florida psychic found guilty of fraud. You think she’d have seen this coming, no?…
http://www.sun-sentinel.com/news/local/crime/fl-rose-marks-verdict-20130926,0,4382976.story?page=2
Madoff accountant could be spending more than just weekends with Bernie…
http://www.stamfordadvocate.com/news/article/Greenwich-man-faces-federal-charges-in-Madoff-4847586.php
Real Housewife in Real Trouble. Teresa Giudice talks about fraud charges…
http://radaronline.com/exclusives/2013/09/teresa-giudice-fraud-charges-crying-andy-cohen/
Medicare fraud trouble in Fargo? Aw geez. Where’s Marge Gunderson when ya need ‘er?
http://www.minotdailynews.com/page/content.detail/id/578432/Wash–doctor-in-ND-court-on-Medicare-fraud-charges.html
Posted by Douglas G. Wood. Click on ABOUT for more information and follow Financial Crimes Weekly on Twitter @FightFinCrime
Monthly Archives: September 2013
SEC taking stock of analytics (and a cool use case for stock exchanges)
 Posted by Douglas Wood, Editor.
Posted by Douglas Wood, Editor.
I read with interest today an article about the SEC’s use of analytics in the ongoing fight against financial crimes. The link to that article is below. It reminded me of some work I once did with a major stock exchange around insider trading.
As a passionate anti-fraud technologist, I was thrilled with the challenge of helping the stock exchange better recognize cases of illegal insider trading. The results of the work we did was pretty cool.
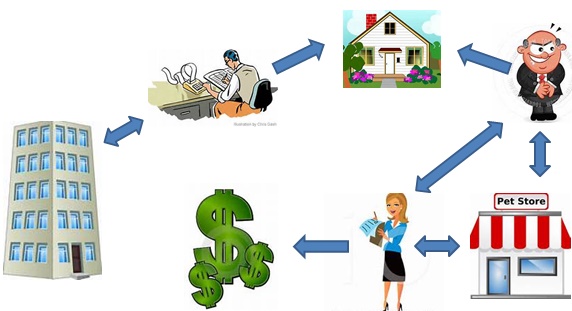
The stock exchange – as do all exchanges – had a great deal of data at their disposal. They knew, for example, the names of each and every ‘insider’ within every company listed on their exchange. Insiders include senior executives, board members, legal counsel, auditors, and so on. Basically, everyone who knew – or ought to have known – about an upcoming event that would likely cause a significant change in stock price.
They also knew, of course, the identity of investors who traded profitably prior to the public release of that information. The problem was exposing the hidden relationships that might exist between Insiders and investors.
Here is an actual example… Joe Blow was an associate partner at the independent accounting firm responsible for auditing the quarterly financial results of publicly traded Company A. By definition, Joe is an insider. He knows Company A’s financials. Jane Doe dumped her entire position in Company A mere days ahead of what turned out to be very poor results. The stock plummeted, and Jane was saved from significant losses. She was seemingly a complete outsider. So, did she somehow know Joe Blow (or any other insider)? Or was she just one lucky gal.
Using link analysis, crime mapping, and behavioral analytics, we set about the challenge of finding out. Here’s what the analytics exposed:
Joe Blow, the insider by way of being employed at Company A’s auditing firm, shared an address with… oh, let’s call him “Rich Quick”. Rich held no positions with Company A whatsoever. He did, however, own a pet food store with a lovely young lady. Can you guess her name? Yep.. Jane Doe. So, the analytics exposed that Company A had an insider relationship with Joe Blow. Joe lived with Rich Quick. Rich owned a business with Jane Doe. Coincidence? Not likely.
Without the ability to draw out hidden links between individuals and organizations, this case may never have been discovered. It’s like Six Degrees of Kevin Bacon, only with much higher stakes. All of the suspects were investigated and prosecuted.
(Note: All the names in this example are fictitious, but the case is not. If your name happens to be Jane Doe, Joe Blow, Rich Quick… or if you work for an organization called Company A, rest assured that I’m not talking about you.)
Here is the link to the SEC article. http://fcw.com/articles/2013/09/18/sec-taps-analytics-to-predict-risk.aspx?s=fcwdaily_190913 .
Prayers, Caregivers, and Breaking Bad – Selected Financial Crimes Snapshot 9/18/2013
Posted by Douglas Wood, Editor. http://www.linkedin.com/in/dougwood
Does KYC mean Know Your Caregiver?
http://onlineathens.com/breaking-news/2013-09-18/savannah-woman-sentenced-51-months-federal-prison-embezzling-71k-elderly
Another great example of the need for systematic 314(b) programs?
http://www.chicagotribune.com/news/local/suburbs/joliet_romeoville/ct-tl-0926-sw-joliet-financial-crime-20130918,0,464668.story
Breaking Bad? Financial Crimes Investigator indicted for fraud.
http://www.timesofisrael.com/senior-financial-crimes-investigator-indicted-for-fraud-theft/
Holy Fraud Scheme! Better say their prayers.
http://greece.greekreporter.com/2013/09/16/sdoe-reveals-monastery-fraud/
Posted by Douglas G. Wood. Click on ABOUT for more information.
Financial Crimes and Technology
Posted by Douglas Wood, Editor.
In the midst of preparing for a presentation last week, I entered the term “financial crimes” into my internet search engine. I’ve probably done this same search a hundred times, but seemingly never took notice of the staggering number of results. Over two million of them!
Among those results are a stunning number of definitions, news reports, and general articles. But with so many links to seemingly unconnected terms such as check fraud, credit card fraud, medical fraud, insider trading, bank fraud, health care fraud, tax evasion, bribery, identity theft, counterfeiting, and money laundering – it must appear to the uninitiated that an understanding of ‘financial crimes’ requires an Einstein-like intelligence pedigree.
To those involved in the daily prevention / detection / and investigation of financial crimes, however, the term can be effectively boiled down to:
1) Intentional deception made for personal gain, and
2) The illegal process of concealing the source of those gains.
Everything else – all that other noise – simply falls underneath that definition, and only a cohesive combination of human intelligence and technology can take a bite out of those crimes.
Of course, most companies that are targets of these crimes invest heavily in different forms of technology for enterprise fraud management and anti-money laundering systems. There are dozens of vendors in this market with varying levels of functionality and service offerings.
The problem with too many of those offerings, however, is that they do not account for organizational truths such as functional (and data) silos, data quality issues, changing criminal tactics, human limitations, and big data.
A complete enterprise solution for financial crimes management must include automated processes for:
Customer Onboarding – Knowing the customer is the first step an organization can take to prevent financial crimes. A holistic view of an entity – customers, partners, employees – provides a very clear view of what is already known about the entity including their past interactions and relationships with other entities.
Flexible Rules-Based Alert Detection – A robust rules-based alert detection process must provide out-of-box functionality for the types of crimes outlined at the beginning of this article. At the same time, it should be flexible enough for an organization to modify or create rules as criminal activities evolve.
Predictive Analytics – Expected by analysts to become a 5.25B industry by 2018, predictive analytics ensures that big data is scrutinized and correlated with present and past historical trends. Predictive analytics utilizes a variety of statistics and modeling techniques and also uses machine information, data mining, and Business Intelligence (BI) tools to make predictions about the future behaviors including risk and fraud.
Social Network Analysis – Also known as Fraud Network Analysis, this emerging technology helps organizations detect and prevent fraud by going beyond rules and predictive analytics to analyze all related activities and relationships within a network. Knowing about shared telephone numbers, addresses or employment histories allows companies to effectively ‘cluster’ groups of suspected financial crime perpetrators. The key here, however, is context. Many technologies can build these networks and clusters for review, but precious few can provide the key “what does this mean” element that business users require.
Investigation Management and Adjudication – Incorporating key elements of enterprise case management, collaboration, link visualization, information dissemination and knowledge discovery, this layer of functionality is designed to uncover insights which aid in investigating complex incidents. The result ought to be actionable visualization of critical entities, and documented results for potential litigation and regulatory compliance.
Anti-Money Laundering (AML) and Regulatory Compliance – With record fines being assessed to financial institutions globally, AML compliance is very clearly a major requirement within a financial crimes management solution. The oversight requirements grow almost daily, but at a minimum include out of box functionality for suspicious activity monitoring, regulatory reporting, watch list filtering, customer due diligence, Currency Transaction Report (CTR) processing, and the Foreign Account Tax Compliance Act (FATCA) compliance.
Now, there are clearly many more dynamics than can be summarized here but hopefully the point is made. The only way that organizations can continue to drive fraud and money laundering out is via a happy marriage between skilled financial crimes professionals and the flexible/adaptable technology that empowers them.
Posted by Douglas G. Wood. Click on ABOUT for more information.