Posted by Tyler Wood, Operations Manager at Crime Tech Solutions
 The topic of fraud is widely discussed, and the focus of thousands upon thousands of articles. Television shows such as Crime, Inc and American Greed have become popular due, in part, to our fascination with the topic of fraud.
The topic of fraud is widely discussed, and the focus of thousands upon thousands of articles. Television shows such as Crime, Inc and American Greed have become popular due, in part, to our fascination with the topic of fraud.
The organizations that are affected by fraud are also fascinated… but for entirely different reasons. Some estimates suggest that the US economy loses 11 trillion dollars each year due to one form of fraud or another. It’s little wonder, therefore, that the companies most frequently defrauded have been heavily investing in anti-fraud technologies at an increasing rate over the past decade or more.
The biggest problem with fraud, of course, is that it is always evolving in a very Darwinian fashion. Like a living, breathing entity, fraud schemes change over time in order to survive. As the targets of fraud schemes put new policies, procedures and/or systems to deter the activities, the schemes modify and find new ways to survive.
So, since the nature of criminal activity is such that they constantly change, how do investigators find a fool proof methodology to ensure they are 100% safe from them? The answer, of course, is that they can’t. They never will; at least not until we live in a world such as the one depicted in the 2002 film Minority Report, starring Tom Cruise. In that movie, criminals are arrested prior to committing a crime based upon the predictions of psychics called ‘Precogs’. Corporations and individual targets of fraud can only wish.
Nope, there are no Precogs running around locking up would-be practitioners of fraud that would protect banks, insurance companies, Medicaid and Medicare programs, victims of Ponzi schemes, victims of identity theft, and countless others. Instead, organizations rely upon skilled knowledge workers using purpose-built crime and fraud analytics technology that can detect anomalies in patterns, suspicious transactions, hotspot mapping, networks of fraudsters, and other sophisticated data analytics tools.
Crime and fraud analytics
Any discussion of analytics and investigation software must touch upon the topic of ‘big data’. No longer just a buzz word, big data literally fuels the insights gathered by organizations in every area of business. Naturally, then, organizations who have been traditionally targeted by fraudsters have increasingly invested in crime technology such as investigation software and analytics in order to exploit the phenomenon.
 Of course, big data in and by itself does nothing. It just sits there. Nobody has ever yelled “Help! We’ve been defrauded! Call the big data!” Big data is only useful when it can be transformed into ‘smart data’. In other words, understanding the big picture of costly fraudulent activities is not akin to understanding the specifics of ‘who’ is defrauding you, and ‘how’ they are doing it.
Of course, big data in and by itself does nothing. It just sits there. Nobody has ever yelled “Help! We’ve been defrauded! Call the big data!” Big data is only useful when it can be transformed into ‘smart data’. In other words, understanding the big picture of costly fraudulent activities is not akin to understanding the specifics of ‘who’ is defrauding you, and ‘how’ they are doing it.
Those questions can best be answered through the powerful data mining and link analysis software tools offered by Austin, TX based Crime Tech Solutions in partnership with Sterling, VA based Visallo. Effective link analysis complements big data analytics platforms, helping to expose previously undetected fraud, and the entities (people or organizations) committing it.
Link Analysis – Transforming big data into smart data
By definition, link analysis is a data analysis technique that examines relationships among people, places, and things. As a visual tool, link analysis provides users a powerful method to quickly understand and ‘see’ what is happening. Because of this, it is widely used by financial institutions such as banks and insurance companies to uncover criminal networks, improve fraud investigations, detect insider fraud, and expose money laundering schemes. Similarly, government agencies use link analysis to investigate fraud, enhance screening processes, uncover terrorist networks and investigate criminal activities.
At Crime Tech Solutions, we liken the question of how to detect and deter fraud to ‘How do you eat an elephant?’ The answer, of course, is one bite at a time. If big data is the elephant, comprehensive link analysis software is part of the one ‘bite’ at a time. Or should we say ‘byte’.
(NOTE: Crime Tech Solutions is an Austin, TX based provider of investigation software and analytics for commercial and law enforcement groups. We proudly support the Association of Certified Fraud Examiners (ACFE), International Association of Chiefs of Police (IACP), Association of Law Enforcement Intelligence Units (LEIU) and International Association of Crime Analysts (IACA). Our offerings include sophisticated link analysis software, an industry-leading investigation case management solution, and criminal intelligence database management systems.)
All posts by Crime Tech Solutions (www.crimetechsolutions.com)
What is Crime Analysis?
Posted by Tyler Wood Crime Tech Solutions, your source for investigation software.
The information provided on this page comes primarily from Boba, R. (2008: Pages 3 through 6) Crime Analysis with Crime Mapping. For a full discussion of the crime analysis discipline, refer to the book which can be obtained through www.sagepub.com.
Over the past 20 years, many scholars have developed definitions of crime analysis. Although definitions of crime analysis differ in specifics, they share several common components: all agree that crime analysis supports the mission of the police agency, utilizes systematic methods and information, and provides information to a range of audiences. Thus, the following definition of crime analysis is used as the foundation of this initiative:
Crime analysis is the systematic study of crime and disorder problems as well as other police–related issues—including sociodemographic, spatial, and temporal factors—to assist the police in criminal apprehension, crime and disorder reduction, crime prevention, and evaluation.
Clarification of each aspect of this definition helps to demonstrate the various elements of crime analysis. Generally, to study means to inquire into, investigate, examine closely, and/or scrutinize information. Crime analysis, then, is the focused and systematic examination of crime and disorder problems as well as other police-related issues. Crime analysis is not haphazard or anecdotal; rather, it involves the application of social science data collection procedures, analytical methods, and statistical techniques.
More specifically, crime analysis employs both qualitative and quantitative data and methods. Crime analysts use qualitative data and methods when they examine non-numerical data for the purpose of discovering underlying meanings and patterns of relationships. The qualitative methods specific to crime analysis include field research (such as observing characteristics of locations) and content analysis (such as examining police report narratives). Crime analysts use quantitative data and methods when they conduct statistical analysis of numerical or categorical data. Although much of the work in crime analysis is quantitative, crime analysts use simple statistical methods, such as frequencies, percentages, means, and rates. Typical crime analysis tools include link analysis and crime mapping software.
The central focus of crime analysis is the study of crime (e.g., rape, robbery, and burglary); disorder problems (e.g., noise complaints, burglar alarms, and suspicious activity); and information related to the nature of incidents, offenders, and victims or targets of crime (targets refer to inanimate objects, such as buildings or property). Crime analysts also study other police-related operational issues, such as staffing needs and areas of police service. Even though this discipline is called crime analysis, it actually includes much more than just the examination of crime incidents.
Although many different characteristics of crime and disorder are relevant in crime analysis, the three most important kinds of information that crime analysts use are sociodemographic, spatial, and temporal. Sociodemographic information consists of the personal characteristics of individuals and groups, such as sex, race, income, age, and education. On an individual level, crime analysts use sociodemographic information to search for and identify crime suspects. On a broader level, they use such information to determine the characteristics of groups and how they relate to crime. For example, analysts may use sociodemographic information to answer the question, “Is there a white, male suspect, 30 to 35 years of age, with brown hair and brown eyes, to link to a particular robbery?” or “Can demographic characteristics explain why the people in one group are victimized more often than people in another group in a particular area?”
The spatial nature of crime and other police-related issues is central to understanding the nature of a problem. In recent years, improvements in computer technology and the availability of electronic data have facilitated a larger role for spatial analysis in crime analysis. Visual displays of crime locations (maps) and their relationship to other events and geographic features are essential to understanding the nature of crime and disorder. Recent developments in criminological theory have encouraged crime analysts to focus on geographic patterns of crime, by examining situations in which victims and offenders come together in time and space.
Finally, the temporal nature of crime, disorder, and other police-related issues is a major component of crime analysis. Crime analysts conduct several levels of temporal analysis, including (a) examination of long-term patterns in crime trends over several years, the seasonal nature of crime, and patterns by month; (b) examination of mid-length patterns, such as patterns by day of week and time of day; and (c) examination of short-term patterns, such as patterns by day of the week, time of day, or time between incidents within a particular crime series.
The final part of the crime analysis definition—”to assist the police in criminal apprehension, crime and disorder reduction, crime prevention, and evaluation” generally summarizes the purpose and goals of crime analysis. The primary purpose of crime analysis is to support (i.e., “assist”) the operations of a police department. Without police, crime analysis would not exist as it is defined here.
The first goal of crime analysis is to assist in criminal apprehension, given that this is a fundamental goal of the police. For instance, a detective may be investigating a robbery incident in which the perpetrator used a particular modus operandi (i.e., method of the crime). A crime analyst might assist the detective by searching a database of previous robberies for similar cases.
Another fundamental police goal is to prevent crime through methods other than apprehension. Thus, the second goal of crime analysis is to help identify and analyze crime and disorder problems as well as to develop crime prevention responses for those problems. For example, members of a police department may wish to conduct a residential burglary prevention campaign and would like to target their resources in areas with the largest residential burglary problem. A crime analyst can assist by conducting an analysis of residential burglary to examine how, when, and where the burglaries occurred along with which items were stolen. The analyst can then use this information to develop crime prevention suggestions, (such as closing and locking garage doors) for specific areas.
Many of the problems that police deal with or are asked to solve are not criminal in nature; rather, they are related to quality of life and disorder. Some examples include false burglar alarms, loud noise complaints, traffic control, and neighbor disputes. The third goal of crime analysis stems from the police objective to reduce crime and disorder. Crime analysts can assist police with these efforts by researching and analyzing problems such as suspicious activity, noise complaints, code violations, and trespass warnings. This research can provide officers with information they can use to address these issues before they become more serious criminal problems.
The final goal of crime analysis is to help with the evaluation of police efforts by determining the level of success of programs and initiatives implemented to control and prevent crime and disorder and measuring how effectively police organizations are run. In recent years, local police agencies have become increasingly interested in determining the effectiveness of their crime control and prevention programs and initiatives. For example, an evaluation might be conducted to determine the effectiveness of a two-month burglary surveillance or of a crime prevention program that has sought to implement crime prevention through environmental design (CPTED) principles within several apartment communities. Crime analysts also assist police departments in evaluating internal organizational procedures, such as resource allocation (i.e., how officers are assigned to patrol areas), realignment of geographic boundaries, the forecasting of staffing needs, and the development of performance measures. Police agencies keep such procedures under constant scrutiny in order to ensure that the agencies are running effectively.
In summary, the primary objective of crime analysis is to assist the police in reducing and preventing crime and disorder. Present cutting edge policing strategies, such as hotspots policing, problem-oriented policing, disorder policing, intelligence-led policing, and CompStat management strategies, are centered on directing crime prevention and crime reduction responses based on crime analysis results. Although crime analysis is recognized today as important by both the policing and the academic communities, it is a young discipline and is still being developed. Consequently, it is necessary to provide new and experienced crime analysts with training and assistance that improves their skills and provides them examples of best practices from around the country and the world. http://crimetechsolutions.com
Insurance Fraud and Terrorist Financing – A bloody mix.
Published by Tyler Wood, Operations Manager at Crime Tech Solutions
December 7, 2015 – Nice post on LinkedIn today written by Aaron Denbo, Lead Trainer at Frauducate Counter-Fraud Academy…

The game has changed. Insurance Fraud isn’t the “quiet fraud” committed by otherwise “normal” people fudging a bit on their past driving experience, prior injuries, work status, or income. It is an $80 BILLION dollar a year problem and it funds and fuels organized crime rings, drug cartels, and terrorism. In a recent article by Christopher Tidball at PropertyCasualty360, “We’re seeing organized trans-national crime rings that are using insurance fraud as a vehicle to fund illegal activities.”
$80 BILLION is a lot of money. That’s a lot of well-funded death and destruction that can be bought and that’s just from the Insurance Fraud front.
That $80 BILLION also includes terrorism, which is more poignant than ever in the wake of both the Paris and the San Bernardino, California terrorist attacks. Combating insurance fraud – and fraud in general — has never been more important.
Now those of us who are counter-fraud professionals and have completed training in identifying, detecting, and investigating fraud and work fraud cases know that what we do is important. Your friends and family probably have a general understanding of what you do but have you connected your work to combating organized crime or terrorism? Have you thought of your work as part of a bigger piece that just might combat the next wave of terrorism? Have you thought of your fraud fighting in terms of making it so that some bad people with bad intentions might just not be able to make that extra explosive device because you disrupted their funding?
After San Bernardino, after Paris, after …. [insert next terror attack here]maybe we should think of ourselves not just as fraud fighters but also as disrupters and agitators to terror groups and organized crime rings. It is a change in awareness and mentality that I’m advocating here, an expansive sense of purpose. Terrorism Finance is more than just working Anti-Money Laundering cases now or leaving that to a problem that the banking sector has to face. It means our insurance fraud investigations are more than just money for our companies or agencies. It means we’re playing for keeps now.
__
Crime Tech Solutions delivers powerful link and social network analysis software to insurance companies to find hidden and suspicious connections between people, places, and things.
Uncovering Fraud means Uncovering Non-Obvious Relationships
Posted by Tyler Wood, Operations Manager at Crime Tech Solutions
Although no fraud prevention measures are ever 100% foolproof, significant progress can be achieved by looking beyond the individual data points to the relationships between them. This is the science of link analysis.
Looking at data relationships isn’t straightforward and doesn’t necessarily mean gathering new or more data. The key to battling financial crimes it is to look at the existing data in a new way – namely, in a way that makes underlying connections and patterns using powerful but proven tools such as the Sentinel Visualizer software offered by Crime Tech Solutions.
Unlike most other ways of looking at data, link analysis charts are designed to exploit relationships in data. That means they can uncover patterns difficult to detect using traditional representations such as tables.
Now, we all know that there are various types of fraud – first-party, insurance, and e-commerce fraud, for instance. What they all have in common is the layers of dishonesty to hide the crime. In each of these types of fraud, link analysis from Crime Tech Solutions offers a significant opportunity to augment existing methods of fraud detection, making evasion substantially more difficult.
Let’s take a look at first-party fraud. This type of fraud involves criminals who apply for loans or credit cards but who have no intention of ever paying the money back. It’s a serious problem for banks, who lose tens of billions of dollars every year to this form of fraud. It’s hard to detect and the fraudsters are good at impersonating good customers until the moment they do their ‘Bust-Out,’ i.e. cleaning out all their accounts and disappearing.
Another factor is the nature of the relationships between the participants in the fraud ring. While these characteristics make these schemes very damaging, it also renders them especially vulnerable to link analysis methods of fraud detection.
That’s because a first-party fraud ring involves a group of people sharing a subset of legitimate contact information and bogus information, and then combining them to create a number of synthetic identities. With these fake identities, fraudsters open new accounts for new forms of loans.
The fraudsters’ accounts are used in a normal manner with regular purchases and timely payments so that the banks gain confidence and slowly increase credit over time. Then, one day… Poof! The credit cards are maxed out and everyone has disappeared. The fraudsters are long gone and ready to hit the next bank down the road.
Gartner Group believes in a layered model for fraud prevention that starts with simple discrete methods but progresses to more elaborate types of analysis. The final layer, Layer 5, is called “Entity Link Analysis” and is designed to leverage connections in data in order to detect organized fraud.
In other words, Gartner believes that running appropriate entity link analysis queries can help organizations identify probable fraud rings during or even before the fraud occurs.
Shame on Wynyard Group
Posted by Douglas Wood
Wynyard Group, a New Zealand based provider of “crime fighting technology” has hit a new low. No, not in stock price or profitability… those are pretty low already.
Instead the company, who seemingly issues a press release every time someone buys new toilet paper, has sought to capitalize on the horrific events this past week in Paris. A new low indeed.
Undoubtedly sought out by Wynyard Group’s PR team, the New Zealand Herald published an article today featuring the company’s CEO Craig Richardson referencing the Paris attacks and touting how his company ‘expected’ to increase revenues by 50% due to rising demand. (This is the same company, remember, who ten weeks ago announced wider than expected losses.)
Note to Wynyard Group: The bodies in Paris aren’t yet cold. Using this as a publicity and marketing tool is despicable. Disgustingly despicable.
Anyone who can analyze a simple financial statement knows that Wynyard Group is burning cash. Still, as a publicly traded entity whose mission ought to be to deliver stakeholder value, does the company not have a requirement for common decency? Apparently not. Using the mass slaughter of hundreds of innocent people for the purpose of yet another news article reeks of desperation, and it ought to sicken anyone associated with that company.
In the unlikely case that the New Zealand Herald reached out without prodding from Wynyard Group, the answer from any C-Level executive anywhere ought to have been “The attacks in Paris are heartbreaking, and our hearts go out to the victims and their families’… not “We expect to sell more stuff.”
At this point, Mr. Richardson, you can pretty much drop the mic and walk off stage. There’s really nothing you can do that will be more classless. At least I’d like to think that’s the case.
Wynyard Group shares were down over 1.5% today.
Policing in my hometown (Winnipeg) gets smart
Posted by Douglas Wood, Crime Tech Solutions
As a native Winnipeg boy, this article in the Winnipeg Sun caught my attention…
 The government of Manitoba, Canada won’t be making good on its 2011 election pledge to put an extra 50 cops on the streets to combat crime and keep Winnipeg neighborhoods safe.
The government of Manitoba, Canada won’t be making good on its 2011 election pledge to put an extra 50 cops on the streets to combat crime and keep Winnipeg neighborhoods safe.
That may seem odd for a city with the highest violent crime rate in the country. But as policing resources shift away from boots on the ground to more crime-analysis based law enforcement, it’s not more sworn officers the Winnipeg Police Service wants, it’s more resources for so-called smart policing strategies.
“The interest of Winnipeg Police Service is not in officers so much as in crime analysis and smart policing and they have a different approach,” Justice Minister Gord Mackintosh told a legislative committee on Monday. “They do not have an interest in just adding more.” The New Democratic Party promised voters during the last provincial election that it would fund 50 additional officers if re-elected. But four years later, the province has only funded 23 more officers. And there won’t be any new funding for more officers, said Mackintosh.
“The commitment was 50 more officers and we’re now at the equivalent of 23,” said Mackintosh. “The city has requested that the election commitment not be implemented as enunciated during the campaign.” It’s a major shift from years past when provincial parties regularly pledged to put more cops on the street by directly funding the Winnipeg Police Service. The former government was the first to make the promise in 1995 when it promised 40 more police officers for Winnipeg.
The province now directly pays for the salaries and benefits of 172 Winnipeg officers, according to a 2014 report.
And while that funding is expected to continue, the city doesn’t want more money for cops. They want it to help fund other aspects of policing, including more preventative measures, said Mackintosh.
“This is a different approach that is gaining momentum not just here in Winnipeg but in other jurisdictions across the continent,” said Mackintosh. “It’s really about hot spot policing now, it’s about data analysis, looking at the types of offences where they occur, the time of day.” Winnipeg police board chairman Coun. Scott Gillingham confirmed the city isn’t looking for more funding to expand the police complement further. He says police are looking to hire more crime analysts, which can be civilians, not more cops.
“The opportunity and the need would be to focus on preventative measures through things like the smart policing initiative (and) intelligence-led policing,” said Gillingham.
What police also need, though, is more help with the additional workload they’ve taken on as they deal increasingly with mental health patients, Child and Family Services cases and soaring domestic abuse calls.
Police may be moving towards a more data-based approach to law enforcement, but they’ve also become a service of last resort for a growing number of tough social service cases, including tracking down chronic runaway wards of the state on a regular basis.
Which means they’re going to need a lot more support from provincial agencies to pick up some of that slack.
Winnipeg police may not need more boots on the ground. After all, Winnipeg does have the most cops per capita of any Canadian city, and has for some time.
But the province is going to have to figure out how to better manage the social service cases that are landing increasingly at the doorstep of police.
Crime Mapping. More than Law Enforcement?
Posted by Crime Tech Solutions
Geographic information systems aren’t exactly new. Drugstore chain Walgreens has used the technology for close to 15 years for market planning.
More recently, however, the company has endowed that visual information with location-specific data—and published far more broadly, so that store managers and its corporate real estate team can use it for planning.
The system, called WalMap, can be used to visualize local community trends. A spike in flu medication prescriptions could help store managers decide earlier to order more vaccine, preventing shortages. Walgreens sales executives can reference trends in supplier conversations. Plus, the interactive maps can be used by the corporate planning team to determine the best place for a new store, based on community demographics, competitor information, and sales trend information. They can even be viewed on an iPad.
“Ten years, our teams had to print out a map and take it with them. Now they can bring their mobile device, and have access to updated sales, demographics and other targeted information,” said Jillian Elder, director of enterprise location intelligence for Walgreens.
Occasionally the maps serve a higher purpose. Managers in Texas in September were able to help local authorities predict the next targets for a local crime spree. “With some of our visualizations, we were able to put a stop to this,” Elder said.
The resource houses millions of maps available to companies that want to overlay proprietary data with the most up-to-data public information about specific locations. There are literally millions of maps published there. Most internal teams have access to basic information; Elder’s team created a special addition specifically for Walgreens’ real estate, strategy, and mergers and acquisition teams.
As of the latest FAQ information on its corporate web site, Walgreens generated more than $76 billion in sales last year across more than 8,300 locations across the United States and Puerto Rico.
Professor urges increased use of technology in fighting crime
 Posted by Crime Tech Solutions
Posted by Crime Tech Solutions
This article originally appeared HERE in Jamaica Observer. It’s an interesting read…
A University of the West Indies (UWI) professor is calling for the increased use of technology by developing countries, including Jamaica, to assist in the fight against crime.
Professor Evan Duggan, who is Dean of the Faculty of Social Sciences, said there have been “amazing advancements” in information and communications technologies (ICT), over the past six decades, which offer great potential for improving security strategies.
The academic, who was addressing a recent National Security Policy Seminar at UWI’s Regional Headquarters, located on the Mona campus, pointed to Kenya as a developing country that has employed the use of inexpensive technology in its crime fighting initiatives.
“Potential applications and innovations have been implemented through the use of powerful but not very expensive technologies that have allowed law enforcers to make enormous leaps in criminal intelligence, crime analysis, emergency response and policing,” he said.
He pointed to the use of a variety of mobile apps for crime prevention and reporting, web facilities, and citizen portals for the reporting of criminal activity.
Professor Duggan said that in order for Jamaica to realise the full benefit of technology in crime fighting, national security stakeholders need to engage local application developers.
“I would enjoin our stakeholders to engage the extremely creative Jamaican application developers, who now produce high quality apps for a variety of mobile and other platforms. I recommend interventions to assist in helping these groups to cohere into a unified force that is more than capable of supplying the applications we need,” he urged.
The UWI Professor pointed to the Mona Geoinformatic Institute as one entity that has been assisting in fighting crime, through analyses of crime data as well as three dimensional (3D) reconstruction of crime scenes; and mapping jurisdictional boundaries for police posts and divisions, as well as the movement of major gangs across the country.
In the meantime, Professor Duggan called for “purposeful activism” in the fight against crime and lawlessness which, he said, are “serious deterrents to economic development and national growth prospects” and could derail the national vision of developed country status by 2030.
“In the current global landscape where security challenges are proliferating across borders and have taken on multifaceted physiognomies, all hands on deck are vital,” he stressed.
“We need to …consolidate pockets of research excellence in this area …to provide the kinds of insight that will lead to more fruitful and productive collaborative engagements that are required to help us better understand the security challenges and threats from crime in order to better inform our national security architecture and direction,” he added.
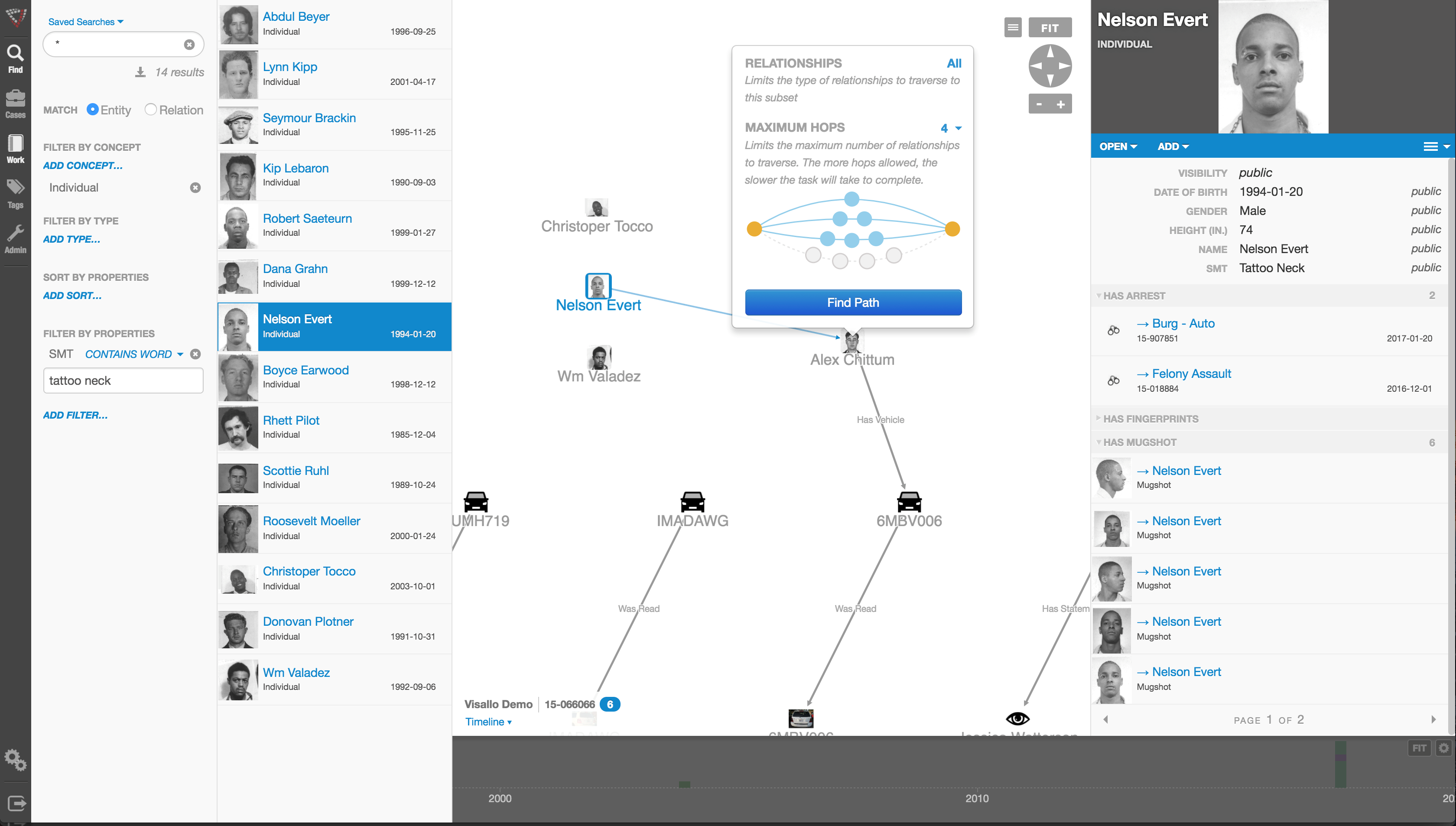
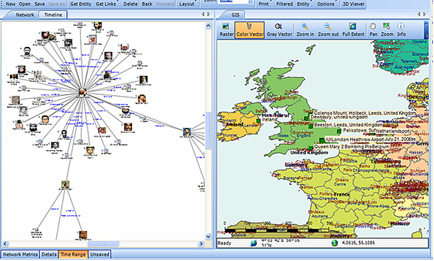
What is Link / Social Network Analysis?
Posted by Crime Tech Solutions
Some linkage data, such as telephone call detail records, may be simple but voluminous, with uniform node and link types and a great deal of regularity. Other data, such as law enforcement data, may be extremely rich and varied, though sparse, with elements possessing many attributes and confidence values that may change over time.
Various techniques are appropriate for distinct problems. For example, heuristic, localized methods might be appropriate for matching known patterns to a network of financial transactions in a criminal investigation. Efficient global search strategies, on the other hand, might be best for finding centrality or severability in a telephone network.
Link analysis can be broken down into two components—link generation, and utilization of the resulting linkage graph.
Link Generation
Link generation is the process of computing the links, link attributes and node attributes. There are several different ways to define links. The different approaches yield very different linkage graphs. A key aspect in defining a link analysis is deciding which representation to use.
Explicit Links
A link may be created between the nodes corresponding to each pair of entities in a transaction. For example, with a call detail record, a link is created between the originating telephone number and the destination telephone number. This is referred to as an explicit link.
Aggregate Links
A single link may be created from multiple transactions. For example, a single link could represent all telephone calls between two parties, and a link attribute might be the number of calls represented. Thus, several explicit links may be collapsed into a single aggregate link.
Inferred Relationships
Links may also be created between pairs of nodes based on inferred strengths of relationships between them. These are sometimes referred to as soft links, association links, or co-occurrence links. Classes of algorithms for these computations include association rules, Bayesian belief networks and context vectors. For example, a link may be created between any pair of nodes whose context vectors lie within a certain radius of one another. Typically, one attribute of such a link is the strength of the relationship it represents. Time is a key feature that offers an opportunity to uncover linkages that might be missed by more typical data analysis approaches. For example, suppose a temporal analysis of wire transfer records indicates that a transfer from account A to person X at one bank is temporally proximate to a transfer from account B to person Y at another bank. This yields an inferred link between accounts A and B. If other aspects of the accounts or transactions are also suspicious, they may be flagged for additional scrutiny for possible money laundering activity.
A specific instance of inferred relationships is identifying two nodes that may actually correspond to the same physical entity, such as a person or an account. Link analysis includes mechanisms for collapsing these to a single node. Typically, the analyst creates rules or selects parameters specifying in which instances to merge nodes in this fashion.
Utilization
Once a linkage graph, including the link and node attributes, has been defined, it can be browsed, searched or used to create variables as inputs to a decision system.
Visualization
In visualizing linking graphs, each node is represented as an icon, and each link is represented as a line or an arrow between two nodes. The node and link attributes may be displayed next to the items or accessed via mouse actions. Different icon types represent different entity types. Similarly, link attributes determine the link representation (line strength, line color, arrowhead, etc.).
Standard graphs include spoke and wheel, peacock, group, hierarchy and mesh. An analytic component of the visualization is the automatic positioning of the nodes on the screen, i.e., the projection of the graph onto a plane. Different algorithms position the nodes based on the strength of the links between nodes or to agglomerate the nodes into groups of the same kind. Once displayed, the user typically has the ability to move nodes, modify node and link attributes, zoom in, collapse, highlight, hide or delete portions of the graph.
Variable Creation
Link analysis can append new fields to existing records or create entirely new data sets for subsequent modeling stages in a decision system. For example, a new variable for a customer might be the total number of email addresses and credit card numbers linked to that customer.
Search
Link analysis query mechanisms include retrieving nodes and links matching specified criteria, such as node and link attributes, as well as search by example to find more nodes that are similar to the specified example node.
A more complex task is similarity search, also called clustering. Here, the objective is to find groups of similar nodes. These may actually be multiple instances of the same physical entity, such as a single individual using multiple accounts in a similar fashion.
Network Analysis
Network analysis is the search for parts of the linkage graph that play particular roles. It is used to build more robust communication networks and to combat organized crime. This exploration revolves around questions such as:
- Which nodes are key or central to the network?
- Which links can be severed or strengthened to most effectively impede or enhance the operation of the network?
- Can the existence of undetected links or nodes be inferred from the known data?
- Are there similarities in the structure of subparts of the network that can indicate an underlying relationship (e.g., modus operandi)?
- What are the relevant sub-networks within a much larger network?
- What data model and level of aggregation best reveal certain types of links and sub-networks?
- What types of structured groups of entities occur in the data set?
Applications
Link analysis tools such as those provided by Crime Tech Solutions are increasingly used in law enforcement investigations, detecting terrorist threats, fraud detection, detecting money laundering, telecommunications network analysis, classifying web pages, analyzing transportation routes, pharmaceuticals research, epidemiology, detecting nuclear proliferation and a host of other specialized applications. For example, in the case of money laundering, the entities might include people, bank accounts and businesses, and the transactions might include wire transfers, checks and cash deposits. Exploring relationships among these different objects helps expose networks of activity, both legal and illegal.
What is Geospatial Crime Mapping?
 Posted by Crime Tech Solutions with information gathered from Wikipedia.
Posted by Crime Tech Solutions with information gathered from Wikipedia.
Here’s a fact: Any understanding of where and why crimes occur can help prevent future crimes.
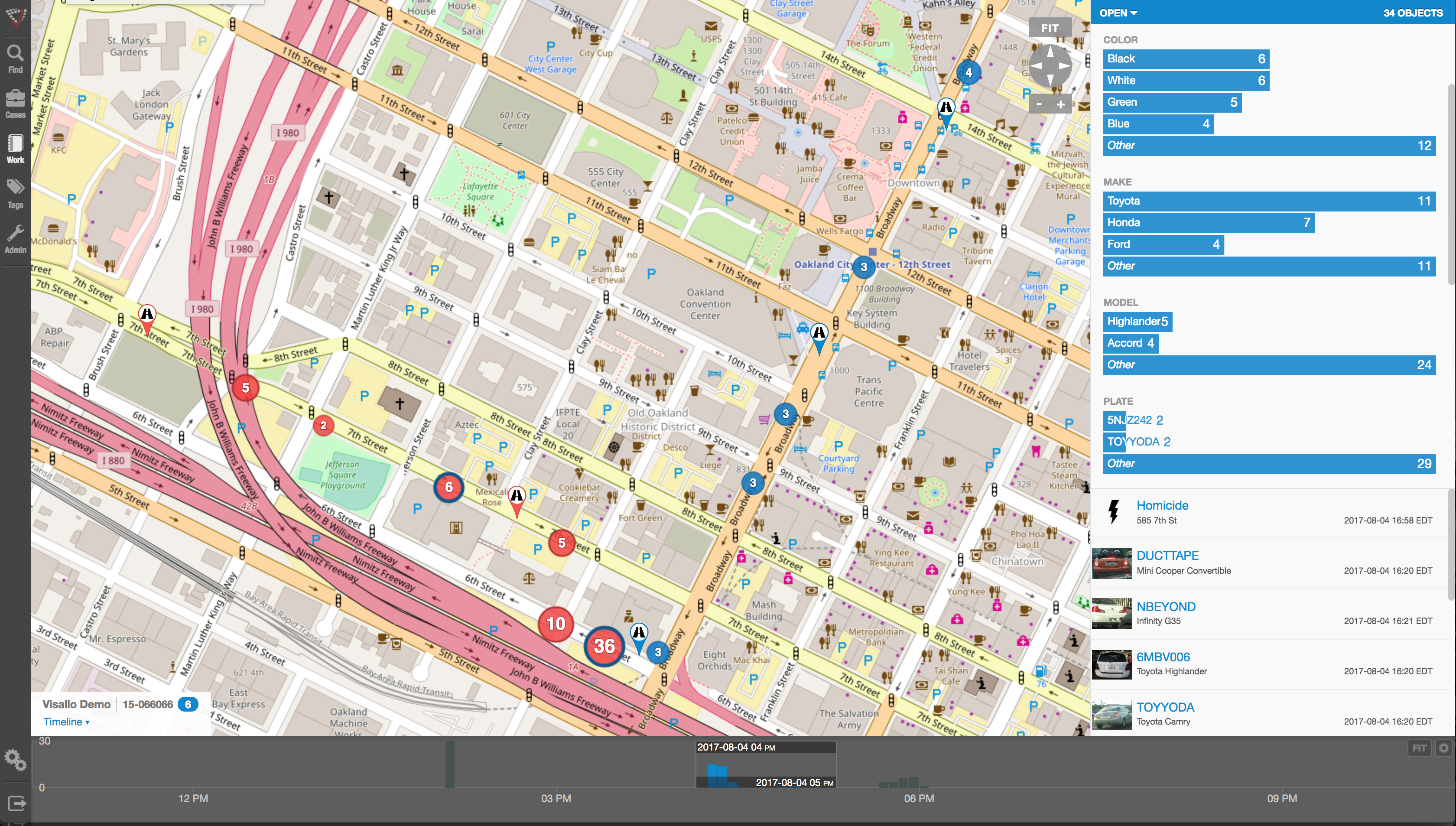
Mapping crime can help law enforcement protect citizens more effectively. Simple maps that display the locations where crimes or concentrations of crimes have occurred can be used to help direct patrols to places they are most needed. Policymakers can use more complex maps to observe trends in criminal activity; such maps can prove invaluable in solving criminal cases. For example, detectives can use maps to better understand the hunting patterns of serial criminals and to hypothesize where these offenders might live.
Products like CrimeMap Pro™ from Crime Tech Solutions are used by analysts in law enforcement agencies to map, visualize, and analyze crime incident patterns. It is a key component of crime analysis and the CompStat policing strategy. Mapping crime, using Geographic Information Systems (GIS), allows crime analysts to identify crime hot spots, along with other trends and patterns.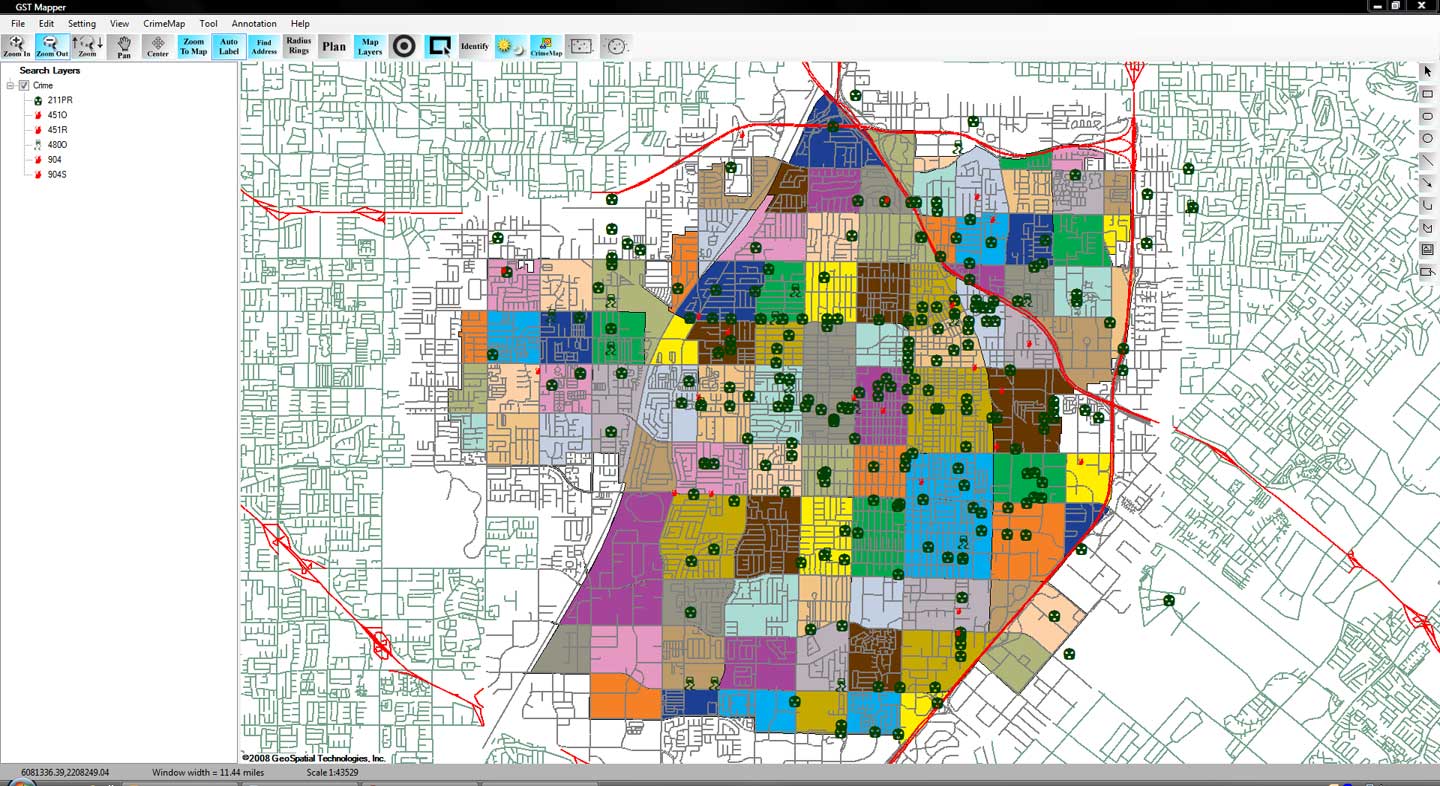
Crime analysts use crime mapping and analysis to help law enforcement management (e.g. the police chief) to make better decisions, target resources, and formulate strategies, as well as for tactical analysis (e.g. crime forecasting, geographic profiling). New York City does this through the CompStat approach, though that way of thinking deals more with the short term. There are other, related approaches with terms including Information-led policing, Intelligence-led policing, Problem-oriented policing, and Community policing. In some law enforcement agencies, crime analysts work in civilian positions, while in other agencies, crime analysts are sworn officers.
From a research and policy perspective, crime mapping is used to understand patterns of incarceration and recidivism, help target resources and programs, evaluate crime prevention or crime reduction programs (e.g. Project Safe Neighborhoods, Weed & Seed and as proposed in Fixing Broken Windows), and further understanding of causes of crime.
The boom of internet technologies, particularly web-based geographic information system (GIS) technologies, is opening new opportunities for use of crime mapping to support crime prevention. Research indicates that the functions provided in web-based crime mapping are less than in most traditional crime mapping software. In conclusion, existing works of web-based crime mapping focus on supporting community policing rather than analytical functions such as pattern analysis and prediction.