Introduction

Investigations of human traffickers, and the subsequent rescue of victims, is a very complex undertaking. Unlike more traditional criminal investigations, there is rarely ‘one suspect’, ‘one victim’, or ‘one location’.
Instead, the crime of human trafficking takes place in a shady world that consists of multiple entities. Multiple perpetrators who work for multiple criminal organizations. Multiple victims who are trafficked by multiple pimps in multiple locations. These variables can make human trafficking a hidden crime that is difficult to investigate. The cost of not investigating, however, is the loss of lives, the loss of freedom, and the loss of innocence.
One particularly complicating feature of human trafficking investigations is the relationships between victims and traffickers. Traffickers initially use force, fraud, or coercion to lure their victims and force them into labor or commercial sexual exploitation. They seek out victims who may be susceptible to their lies for a variety of reasons including economic hardship, psychological or emotional instability, or other socio-economic disadvantages.

Once lured by the traffickers, victims rarely have an opportunity to speak out or call for help. Language barriers, fear of their attackers, lack of a social safety net, and a general feeling of helplessness overwhelm the victims. Thus, the crime becomes difficult to investigate.
But investigate we must. The cost of turning our backs on this global problem is simply too high.
This overview will focus on some best practices for managing investigations into human trafficking, the capture of perpetrators, and the rescue of victims. A haphazard approach to these sensitive and complex investigations is likely to cause more harm than good, and these best practices are designed to help your organization maximize your productivity and safely rescue more victims.
Best Practice #1 – Stay Organized
The first best practice we need to discuss is ‘Staying Organized’. What might start off as a Tip that a young girl is being sold for sex in a local hotel may quickly grow in scope to include multiple victims, multiple locations, multiple pimps, and multiple abusers. These criminal enterprises thrive in the dark and, like cockroaches, simply scatter and disappear once light is shone. The practice of staying organized helps ensure that no intelligence or evidence falls through the cracks, giving the traffickers time to scatter and hide.

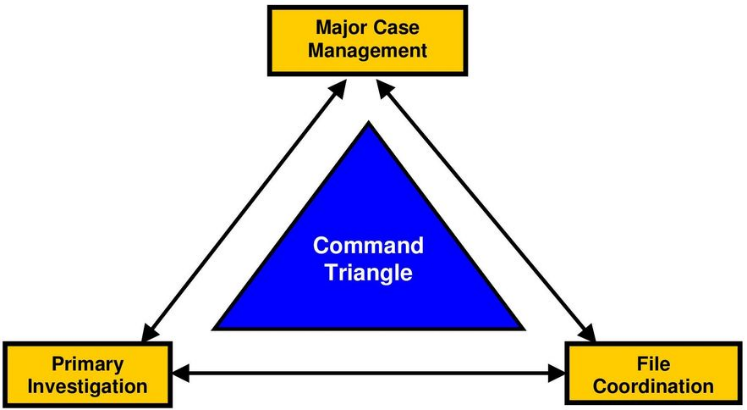
Use investigation case management software. There are simply too many ‘moving parts’ within a human trafficking enterprise to attempt to stay organized without a purpose-built database. Spreadsheets, notes, cloud folders… these are all yesterday’s tools that cannot adequately manage today’s investigations.
With your case management software, track every tip that you receive. Some tips may be stronger than others. Some may lead to full-blown investigations, and some may not. In any case, track and store each tip that you receive as you never, ever know when information from those tips may become relevant to your ongoing investigations.
Triage every tip you can. Spend a moment to search your case management system to determine if anything about a tip relates to any current or past investigation. You can’t do this with paper files or spreadsheets. Perform some online research on the subject(s) of the tips to gauge how reliable the information might be. If the tip initially lacks the actionable or credible information to assign resources, keep the data in the case management system for future use. If the tip does contain actionable and credible information, use the case management system to prepare an actual Investigative Case and assign resources immediately.

Importantly, in terms of Staying Organized, use your case management process to track each action being taken on the investigation. Did someone perform some Open Source Intelligence on the suspected location? Log that information electronically so that it does not fall through the cracks.
Has an agent visited the suspected location to determine if there are likely victims there? Log that into the system. Store any videos or photographs that the investigator made and attach them right to that case.
Log and maintain notes and related files on every action taken on your human trafficking cases. Make them safe, secure, and easy to access by other team members.
Organization is the KEY to any criminal investigation, and even more so for investigations into human trafficking.
Best Practice #2 – Securely Share Information in Real-Time
Investigations into human trafficking and victim rescues are complex and cannot occur in a vacuum. Much like the criminal enterprises themselves have multiple roles such as kidnappers, transporters, handlers, and pimps for example, so must your investigation team have specialized roles. Your undercover ‘john’ cannot be the same as your public-facing advocate, for example.

The key to ensuring that everyone involved in the investigation is successful is sharing information. In an environment where traffickers are always on the lookout for potential risks to their operation, it’s of utmost importance that your operational team all be on the same page so that no missteps occur.
This type of alerting and information sharing cannot be done by text messages or word-of-mouth. It must occur within a fool-proof system of secure information sharing where there is no room for ambiguity. Lives depend upon it.
All of the actions and intelligence that is gathered during an investigation should be securely stored in your case management system. The moment a member of the investigation team submits new information, all other permitted team members should have secure, online access to the new information whether they are notes, videos, photographs or other file types. The removal of ambiguity or misinterpretation is key to ensuring that all team members are aware of the case status at all times.

As an aside, for multi-jurisdictional investigations, teams should ensure that individual members can view the information in the language of their choice in real-time. If the information was entered by an investigator in Brazil using Portuguese, that information should immediately be readable to a team member in Colombia who understands only Spanish. Always focus on ensuring your team members have access to accurate information in real-time. When time is lost, the cockroaches scatter.

In those unique situations where individual team members do NOT require access to the information, perhaps because an investigation is particularly sensitive or involves public officials, your case management system should have capabilities to disallow them from viewing the update. This keeps information in the correct hands, while still furthering the integrity of the data-sharing requirement.
Only when information is shared in real-time can managers and team leaders best determine the next steps for the investigation and rescue of victims.
Best Practice #3 – Maintain Investigation Privacy and Integrity
As mentioned above, human trafficking organizations are like cockroaches. The moment they sense something is going to shine a light on them, they disappear into the woodwork. This most tragic of outcomes is painful for both the investigators and victims alike.
Keeping the investigation lights off, therefore, must be a strategic goal of human trafficking investigations. Assigning roles to your team, and ensuring that all members are adhering to those roles, is one way to keep your actions covert and secure. If a team member’s role is to pose as an interested buyer of sex, that team member should probably not also be involved in general reconnaissance of crime scenes where he or she may be recognized.

Another way to ensure privacy and integrity is to utilize cutting-edge access policies to ensure that information is not accessed by outsiders or, worse yet, an insider to your team. Ensure, therefore, that EVERY SINGLE KEYSTROKE into your case management system is logged and reviewable. If your suspect organization packed up and left mere days before your major rescue and arrest operation, its important to know how that happened. Who accessed the information in your case management system, and why?
Make sure that the information your team is electronically storing is secure. Very secure. Use globally recognized and proven data security standards to protect all data and access to it. Ensure that all team members are trained and well-versed on any systems you are using for investigations.
There can never be too much integrity in a human trafficking investigation, and there can never be too much privacy. Loose lips sink ships. The same goes for loose investigation procedures. The line between a rescued victim and a lost opportunity is thin. Use investigation privacy and integrity to walk that line more effectively.
Best Practice #4 – Share Information with Senior Law Enforcement or Trusted Partners
As a team of human trafficking investigators, you recognize the seriousness and horror of human beings – like you, like me, like our daughters, sons, and grandchildren – being bought and sold for pleasure. You understand the misery of the victims and feel compelled to help. Good. That makes you a good person.
Law Enforcement agencies, however, do not typically act as emotional human beings. They have full caseloads involving homicides, drugs, corruption, and a host of other traditional crimes. Too often, they view human trafficking as merely ‘prostitution’. If a person wants to sell his or her body in exchange for money, there are no victims and, therefore, these cases can often receive a very low priority. Many times, they are dismissed out of hand.
The job of the human trafficking investigation team, therefore, is to get the attention of senior local law enforcement partners in a direct and meaningful manner… one that compels the officers to work with your team in rescues and arrests.

Our history and background suggest that engaging senior law enforcement ‘too early’ adds risk to the investigation. Remember, loose lips sink ships, and these cases are often viewed as unimportant.
Sadly, our experience also shows that involving senior partners ‘too late’ is problematic as police departments are often reluctant to become involved in situations that they have not directly controlled and cannot easily verify the integrity of the work done prior to their involvement.
So, the answer of when to involve your senior partners is unique to each case and each situation. That decision can’t be covered in detail here. Instead, the method used to involve local senior law enforcement – whenever that transpires – is a factor that you can and should control to maximize the potential for a successful operation.

Going in to meet with your prospective law enforcement partner should be a pleasant experience. Your team has built a good case and you’re ready to involve the authorities to help finalize the operation. Going in unprepared, however, will result in disappointment or disaster. As advocates for the prosecution of these types of crimes, you’re full of passion. Best practices, however, show that it is equally important to be full of actionable facts, evidence, and proof.
Therefore, best practices suggest that you build a ‘case file’ as you prepare to meet with law enforcement or senior management. On television, they sometimes call the visual representation of this case file a ‘murder board’. Make sure you have one. Make sure your case file lists ALL of the entities involved in your case. Make sure it includes all of the specific actions you’ve taken. Make sure it includes all of the audio, video, photos, and other evidence you’ve gathered.
Make sure the case file clearly shows the human trafficking operation. Who is in charge? Who are victims? What locations are involved? Who are the supporting witnesses?
Without an easy-to-digest case file, your chance of getting senior law enforcement’s attention diminishes quickly. So, utilize your case management system to very clearly outline the case in a compelling and thorough manner.
Best Practice #5 – Plan, Plan, and Plan Again
The final best practice is Operational Planning. Not to overstate it, but as I’ve said earlier human traffickers are cockroaches. At the first sign of light, you’ll lose them. Every time.
The final best practice for investigating human trafficking is perhaps the most important. Plan.

Plan, then plan again, and then plan once more. Plan your response to every initial tip. Plan your initial investigation work into every case. Plan the tasks and mission of every operative involved in your case. Plan how to get case information into the hands of those who need it in real-time. Plan to keep the investigation quiet so as not to risk the cockroaches running.
Plan every covert operation as if lives depended upon it. They might. Plan in advance what the ‘panic’ word is. Plan in advance what hand signals your operative might use if audio fails. Plan in advance to know where the nearest trauma center is. Plan in advance to know what other risks are present. Dogs? Security? Children?
Plan and make that plan available to everyone who needs to see it. Share that plan in your case management system and know when every user has read it.
Finally, plan to present your case in a compelling manner to senior law enforcement officials. And then work with them on a plan to successfully pull victims out of harm’s way and arrest the bad guys.
Summary of Best Practices

We have covered some of the key ingredients to a successful human trafficking investigation and rescue. Of course, no operation ever goes exactly as you expect, but by ensuring that you are following these best practices – staying organized, sharing internal information, maintaining investigation integrity, effectively engaging with senior law enforcement officials, and conducting meticulous planning – you greatly increase the likelihood that your efforts will result in the wonderful rescue of victims and the prosecution and incarceration of the perpetrators.
By Douglas Wood, entrepreneur and investigation management professional.
Copyright 2021 Case Closed Software™


 Douglas Wood is CEO of
Douglas Wood is CEO of 


 Douglas Wood is CEO of
Douglas Wood is CEO of 


 Case Closed Software
Case Closed Software


 Posted by Tyler Wood, Director of Operations at Case Closed Software.
Posted by Tyler Wood, Director of Operations at Case Closed Software.
 El Paso, TX – Gang investigators were told a suspect in surveillance footage matched the description of “Flaco”, a known gang member in the area.
El Paso, TX – Gang investigators were told a suspect in surveillance footage matched the description of “Flaco”, a known gang member in the area.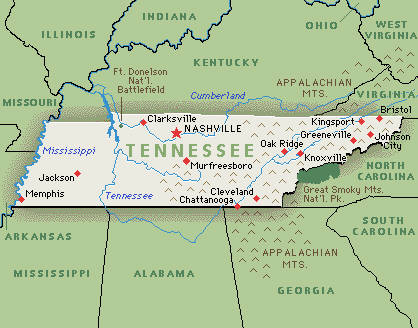 The mid-sized Sheriff’s Department in the Volunteer State chose Case Closed Software after a long, thorough search for a solution provider capable of delivering “a feature-rich, affordable solution for managing investigations and the investigative unit”. The core modules of the software include
The mid-sized Sheriff’s Department in the Volunteer State chose Case Closed Software after a long, thorough search for a solution provider capable of delivering “a feature-rich, affordable solution for managing investigations and the investigative unit”. The core modules of the software include 
 Per Wynyard Group officials, the company has placed itself in voluntary administration as it battles crippling losses and missed revenue forecasts, leaving customers in the dark as to the future of their investment in the crime fighting technology.
Per Wynyard Group officials, the company has placed itself in voluntary administration as it battles crippling losses and missed revenue forecasts, leaving customers in the dark as to the future of their investment in the crime fighting technology.
