Several times each week, I receive an inquiry from a PD, task force, or Sheriff’s office asking if my investigation case management software, Case Closed Software, can interface with a particular Records Management System (RMS). The question stems from the investigation unit’s desire to have a purpose-built, flexible solution designed to help their agents stay organized and work more efficiently.
Let’s face it… RMS software, by and large, is not designed for managing major cases. Agencies know it, and the RMS vendors know it. For them, the notion of managing the complexities of major case investigations is an afterthought at best.
(The answer I give to these inquiries, by the way, is that any good investigation management software should have capabilities to ingest data from other law enforcement products, including RMS).
The more important point, however, is recognizing that criminal investigators gather vasts amounts of information during the course of an investigation. Witness statements, interviews, interrogations, tips, leads, informant statements, audio files, video files, photos, and much more. Too often, agents must rely on their RMS systems which, per above, are not purpose-built for investigations. Investigators also rely heavily on paper files and file cabinets full of notes, search warrants, and physical evidence.
Fortunately, there is an alternative… purpose built investigation case management software that utilizes what I call ‘Case Actions’ as the underlying workflow. Case Actions are the individual actions that an investigation unit takes in pursuit of closing a case. Case Actions are expansive in nature, and include:
- Crime Scene Visits
- Interviews
- Interrogations
- Knock ‘n Talks
- Surveillance
- DNA
- Search Warrants
- Affidavits
- Controlled Buys
- Arrests
… and much, much more. You get the idea, though.
By effectively logging each Case Action in a particular Case, the investigators (and management) are able to quickly and visually recognize the status of the case, and what further actions should be taken. Each Case Action leads to new information… which leads to new Case Actions. And the beat goes on. Hopefully, sooner rather than later, enough information is garnered to close the case. That’s the power of Case Action based workflow.
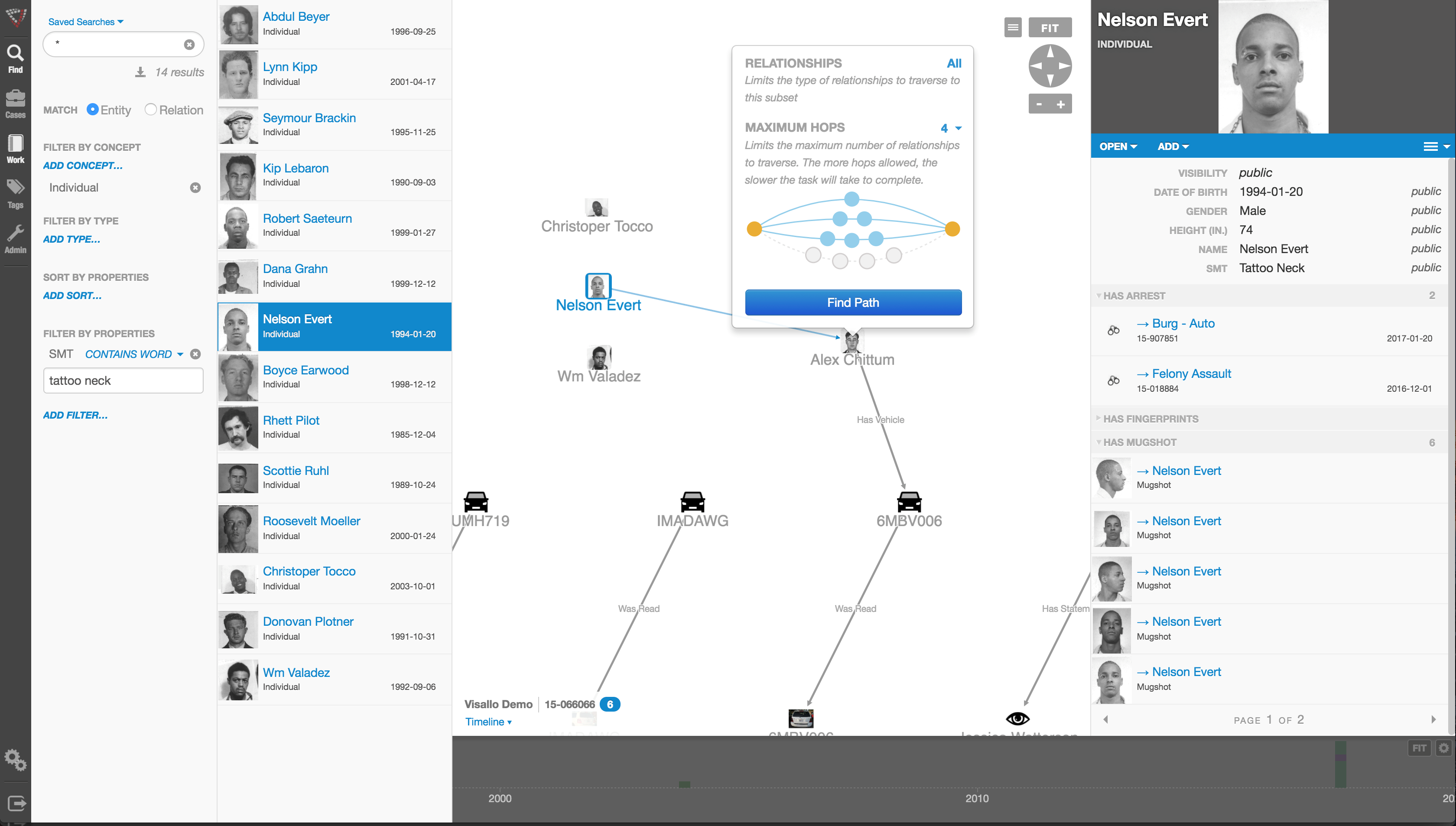
WIth the Case Action based approach, each Case Action is tied to Persons, Locations, Vehicles, etc. As a result, robust dossiers of these things are built without the individual agent(s) even realizing it.
By utilizing an investigation case management solution that is based upon Case Actions, law enforcement can leverage information from previously-entered data such as telephone numbers, evidence items, addresses, persons, gang members, etc. The Case Actions feed themselves – and each other – to build a valuable repository of investigative information.
An example: A detective has received a tip that Doug Wood is involved in a particular criminal activity. By accessing her Case Action-based system, she quickly learns that Doug Wood has been a Suspect in Case 1 (belonging to an entirely different investigator), and a Witness in Case 2 (belonging to a third investigator).
She also learns (via Case Actions performed by the Gang Unit) that Doug Wood shares an address with a confirmed Gang Member and goes by the nickname ‘Woody’. She also sees Doug’s previous addresses, telephone numbers, work history, social media accounts and so on… each of which has been logged as part of completely unique Case Actions.
That is the power of Case Actions based investigation management software. Because each previous Case Action involving Doug Wood was logged, the current investigator has a goldmine of information at her fingertips.
Case Closed Software is the leading provider of Case Action based investigation case management software for law enforcement. Contact Us for a demo today!

 Here’s an excellent, must-read article from Andrew Guthrie Ferguson, a Professor of Law at the
Here’s an excellent, must-read article from Andrew Guthrie Ferguson, a Professor of Law at the  Case Closed Software™
Case Closed Software™
 Great article from our friends at
Great article from our friends at  The notion that law enforcement fusion centers regularly violate individuals’ privacy rights as they capture intelligence on gangs, terrorist activities, organized crime, and other threats to public safety is simply not true. That, according to a study published in the
The notion that law enforcement fusion centers regularly violate individuals’ privacy rights as they capture intelligence on gangs, terrorist activities, organized crime, and other threats to public safety is simply not true. That, according to a study published in the 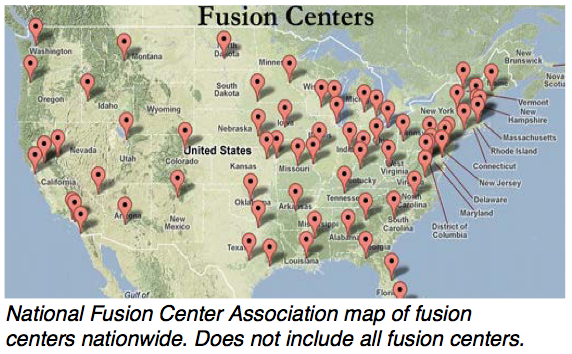 There are approximately 80 fusion centers in the United States. They were created in response to the 9/11 terrorist attacks. The attacks exposed the requirement for greater information sharing and improved intelligence capabilities at all law enforcement levels. According to the article’s author, the idea was to have the key pieces of data funneled into fusion centers so that highly trained analysts could stay atop of threats and correspond with local law enforcement agencies on these potential threats.
There are approximately 80 fusion centers in the United States. They were created in response to the 9/11 terrorist attacks. The attacks exposed the requirement for greater information sharing and improved intelligence capabilities at all law enforcement levels. According to the article’s author, the idea was to have the key pieces of data funneled into fusion centers so that highly trained analysts could stay atop of threats and correspond with local law enforcement agencies on these potential threats. The notion that law enforcement fusion centers represent ‘Big Brother’, and that data is being stored and disseminated about people irrespective of whether they are suspected of criminal activity is simply wrong, according to Professor Carter.
The notion that law enforcement fusion centers represent ‘Big Brother’, and that data is being stored and disseminated about people irrespective of whether they are suspected of criminal activity is simply wrong, according to Professor Carter. “Fusion centers are following the federal regulatory code, 28 CFR Part 23, that is the legal standard for collecting information,” Carter said. “That code says you have to establish a criminal predicate, basically probable cause, to keep information on identifiable individuals.”
“Fusion centers are following the federal regulatory code, 28 CFR Part 23, that is the legal standard for collecting information,” Carter said. “That code says you have to establish a criminal predicate, basically probable cause, to keep information on identifiable individuals.” Crime Tech Solutions
Crime Tech Solutions The mid-sized Sheriff’s Department in the Volunteer State chose Case Closed Software after a long, thorough search for a solution provider capable of delivering “a feature-rich, affordable solution for managing investigations and the investigative unit”. The core modules of the software include
The mid-sized Sheriff’s Department in the Volunteer State chose Case Closed Software after a long, thorough search for a solution provider capable of delivering “a feature-rich, affordable solution for managing investigations and the investigative unit”. The core modules of the software include 
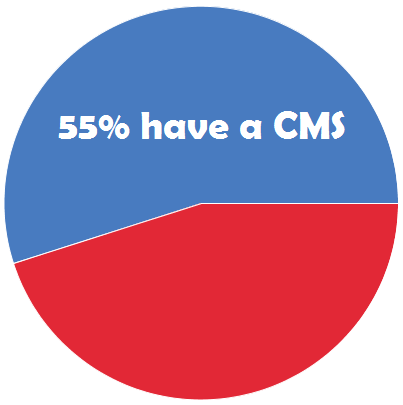 According to the study, just 55% of U.S. law enforcement agencies currently utilize investigative case management software (CMS), and the majority of users are unhappy with their current systems.
According to the study, just 55% of U.S. law enforcement agencies currently utilize investigative case management software (CMS), and the majority of users are unhappy with their current systems.