(January 20, 2017) Crime Tech Solutions, LLC – a fast-growing and vibrant investigation and crime analytics software company based in Austin, TX – today announced that they have secured a multi-year contract to provide advanced criminal intelligence and crime analysis software to a progressive Northern California police department.
 The Bay Area city of approximately 300,000 residents is implementing the software company’s IntelNexus™ and Sentinel Visualizer™ solutions. IntelNexus is criminal intelligence database management system designed to help the department gather, store, and disseminate sensitive criminal intelligence data. The program complies with the US federal regulation 28 CFR Part 23, which is a set of guidelines that help law enforcement agencies balance the need to collect and store criminal intelligence with the individual civil liberties of residents. The software ensures that only the correct type of data is stored, and that it is disseminated to authorized users only on a need-to-know basis.
The Bay Area city of approximately 300,000 residents is implementing the software company’s IntelNexus™ and Sentinel Visualizer™ solutions. IntelNexus is criminal intelligence database management system designed to help the department gather, store, and disseminate sensitive criminal intelligence data. The program complies with the US federal regulation 28 CFR Part 23, which is a set of guidelines that help law enforcement agencies balance the need to collect and store criminal intelligence with the individual civil liberties of residents. The software ensures that only the correct type of data is stored, and that it is disseminated to authorized users only on a need-to-know basis.
Sentinel Visualizer is a sophisticated data visualization software program that assists crime analysts by finding and displaying non-obvious connections between people, places, and other entities. The link analysis software clearly displays how entities are connected with each other, and is rapidly becoming a staple of investigators and analysts across the country.
Crime Tech Solutions also develops powerful investigation management software called Case Closed™.
Category Archives: crime analysis
The Case for Investigative Case Management
Lost in the news of the recent demise of New Zealand based crime-fighting software developer Wynyard Group, is an interesting report published just weeks before the company ceased operations.
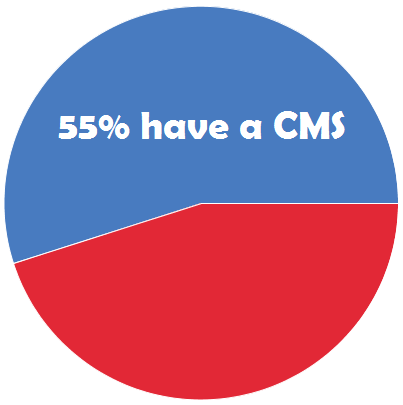 According to the study, just 55% of U.S. law enforcement agencies currently utilize investigative case management software (CMS), and the majority of users are unhappy with their current systems.
According to the study, just 55% of U.S. law enforcement agencies currently utilize investigative case management software (CMS), and the majority of users are unhappy with their current systems.
Thirty-seven percent of the study respondents are not currently using any type of automated system, and rely mainly on paper files and spreadsheets to manage their investigations.
Investigative case management software has long been the domain of larger agencies and departments, and is only now truly affordable for smaller departments. The software allows investigators to manage the investigation process from start to finish. The more robust software allows agencies to assign cases and tasks, manage deadlines, store and maintain physical and multimedia evidence, and to search for relevant information across disparate databases.
According to a press release issued at the time, the survey queried users on how likely they would be to recommend their current system to another agency. While most users were unhappy with their current investigative case management system, there was a clear difference between agencies using commercial-off-the-shelf (COTS) software and those using home grown, legacy systems. The latter fared very poorly in the survey results.
The survey also measured the use of smart devices by front-line officers. Forty three percent indicated that they currently utilize smart phones and tablet computers, and 23% indicated they had neither device.
The most-desired features in investigative management software include:
- Management Dashboards
- Reports – Standard and ad hoc
- Case Assignment and Reminders
- Actions and Incident Management
- Mobile and Front-Line Case Access
- Evidence Management and Chain-of-Custody
- Multimedia Handling
- Audit Logs
- Collaboration
- Gangs and Organized Crime Management
- Data Visualization and Link Analysis
- Case Closure / Evidence Brief
An investigative case management system for law enforcement and commercial investigation agencies is rapidly becoming a ‘must-have’. In an era of shrinking budgets and competing resources, a high value is placed on getting the biggest ‘bang for the buck’. The study indicates that agencies are looking to maximize the value of their investigative case management software by incorporating a robust feature set with an affordable price.
Case Closed Software, a division of Crime Tech Solutions, is a powerful and affordable investigative case management solution for law enforcement agencies. Case Closed is also available via the cloud with the innovative Case Closed Cloud. Created by former law enforcement investigators, the COTS software is designed with ease-of-use in mind. The software is deployed in agencies – large and small – across the country.
The CalGang Audit: Lessons Learned for Law Enforcement.
The following article is a continuation, of sorts, to our article ‘Intelligent Gang Intelligence’ on September 28…
CalGang is a California statewide database that law enforcement agencies use to store and disseminate information about gang activities and suspected gang members. The system has been in place for more than ten years, but has remained largely hidden from public scrutiny.
Shirley Weber, a California Assemblyperson has been working diligently to make CalGang more transparent, and her efforts have recently begun to pay off.

Last year, Ms. Weber requested an audit of the CalGang system. The database contains activities, addresses, names, aliases and other information related to people that are either known gang members or affiliates. According to an article by The San Diego Union-Tribune, the database has approximately 150,000 entries.
California law enforcement agencies are not obligated to notify individuals whose names appear in the system, unless that person is a minor. The average length of time that an individual had existed in CalGang was approximately 5.5 years.
The CalGang audit requested by Ms.Weber was released in August of this year, and reveals that the database may contain a significant number of errors including the presence of dozens of individuals who were less than one year old when first added to the system. The audit also showed that hundreds of individuals that ought to have been removed from the system were, in fact, not.
The findings led Governor Jerry Brown to sign a bill in September that requires law enforcement to notify individuals whose names are added to CalGang, unless it can be shown that providing that disclosure would impact an ongoing criminal investigation.
The audit has shed some light on how gang databases are operated in general, and offers an opportunity for agencies across the country to improve policies and processes. Specifically, 28 Code of Federal Regulations (CFR) Part 23 (28 CFR Part 23) is a U.S. Department of Justice regulation that governs “the operation of criminal intelligence systems that are operated by and principally for the benefit of state, local, tribal, or territorial law enforcement agencies.”

28 CFR Part 23 was designed as a regulation specific to multi-jurisdictional criminal intelligence (gang database) systems that receive federal grant funds. It is an excellent guide for intelligence agencies, as it attempts to fairly balance the intelligence needs of law enforcement with an individual’s rights to privacy.
Followed appropriately, 28 CFR Part 23 guidelines would minimize criticism of CalGang and other intelligence management systems.
“This report concluded that CalGang’s current oversight structure does not ensure that law enforcement agencies collect and maintain criminal intelligence in a manner that preserves individuals’ privacy rights,” wrote state auditor Elaine Howle in a letter to the governor and Legislature.
Of concern, the audit of CalGang also uncovered some instances where the data was used for purposes other than intended. Some agencies used the database for employment background screening, as an example.
The guidelines and regulations contained within 28 CFR Part 23 work to prevent these embarrassing and potentially unlawful scenarios by enforcing strict policies related to the input, storage, and dissemination of data.

Gang and criminal intelligence data is defined within 28 CFR Part 23 as “data which has been evaluated to determine that:
A) it is relevant to the identification of, and the criminal activity engaged in by, an individual who – or an organization which – is reasonably suspected of involvement in criminal activity, and
B) meets criminal intelligence system submission criteria”
The ‘submission criteria’ is essentially the basis for something to be entered into the gang intelligence system. The criteria include the following:
- A reasonable suspicion that an individual is relevant to the criminal activity
- Prospective information to be entered is relevant to the criminal activity
- Information does not include data related to political, religious, or social views unless that information related directly to the criminal activity that formed the basis for focus on the gang or group
- Information was not obtained in violation of any federal, state, or local law or ordinance
- Information establishes sufficient facts to give trained law enforcement officials a basis to believe that an individual or gang/organization is involved in a definable criminal activity
Data that is deemed to be irrelevant and unimportant should be purged from the system. This is true even if the data is discovered to be noncompliant before five years.
Perhaps the most important element of a gang database system complying with 28 CFR Part 23 is that no information whatsoever from the database should be disseminated without a legitimate law enforcement reason, such as criminal investigation cases and charges being filed against a suspect.
CalGang is an important and vital part of California law enforcement’s ability to deter and investigate gang related activities. A system this large is bound to contain some errors – both in data and judgement. That said, following and adhering to the guidelines of 28 CFR Part 23 may just prevent other agencies from undergoing such a painful public flogging.
About the Author
Tyler Wood is Operations Director of Austin, TX based Crime Tech Solutions (www.crimetechsolutions.com). The company develops and deploys low price / high performance software for law enforcement including Case Closed™ investigative case management software, sophisticated Sentinel Visualizer™ link analysis and data visualization software, and CrimeMap Pro™ advanced crime analytics. The company also develops the popular GangBuster™ gang database, and IntelNexus™ criminal intelligence software for 28 CFR Part 23 compliance.
Social Media leads to Hate crimes
The following article appears in California State University’s Coyote Chronicle, written by Geraldine Carrillo. Crime Tech Weekly has reposted the article in full for our readers’ convenience…
“There is going to be a fight today after school on Walnut St.,” was a post on Facebook from one of my friends during my sophomore year of high school.

Soon after this post, other students then replied with the location and time of the fight on social media to create an audience for that fight as an amusement to go watch.
This made safety patrols aware, which led to a raid by police.
Keeping an eye on social media has been a good way to prevent hate crimes throughout the new digital era.
But the extent to which it has been utilized is ridiculous compared to the hike in the number of committed crimes.
Hate crime is a crime motivated by racial, religious, gender, sexual orientation or other prejudice, according to legaldictionary.com.
“More than 250,000 Americans over the age of 12 are victimized every year by hate criminals, according to a new government study that puts the number some 50,000 higher than the best earlier analyses,” stated Senior Fellow, Southern Poverty Law Center, Mark Potok.
I believe that social media has been used as a tool not only for our daily lives, but also to stop the bad and the unjust that is presented by reckless people.
“I think social media is a good way to prevent hate crimes t hat sometimes aren’t reported, because people are scared or just don’t want to get involved,” said student Brian Romero.
hat sometimes aren’t reported, because people are scared or just don’t want to get involved,” said student Brian Romero.
In fact, according to the Justice Department, “Approximately 293,800 nonfatal violent and property hate crimes occurred in 2012, but about 60 percent of those crimes went unreported. One theory suggests victims who are non-citizens remain silent out of fear of deportation.”
We often see negativity on social media that can easily escalate to an actual offense against the law, using predictive policing can help prevent these wrongdoings from happening.
“In recent years, predictive policing has become increasingly important, utilizing the advancements of analytics like data mining and machine-learning methods,” stated Pete Burnap of Cardiff University’s School of Computer Science and Informatics.
I believe tracking hate crime is important because we underestimate how frequent these offenses occur and are reported.
Most crimes go unreported which makes social media a platform to engage people in sharing and spreading the events of situations to justice.
“At the same time, the study found that in recent years only about one in three hate crimes are ever reported to law enforcement officials,” continued Potok.
This should be a huge eye opener to people who don’t think hate crimes are occurring let alone existing.
 Some people may not agree because it abides by the First Amendment, and not all hate crimes show their intention online, although it is a step in the right direction to monitor those that are.
Some people may not agree because it abides by the First Amendment, and not all hate crimes show their intention online, although it is a step in the right direction to monitor those that are.
Discrimination or any act of offense towards others should not be permitted and stopped while it escalates out into society.
We have to keep in mind that not only adults monitor social media, but also young children and teenagers are monitoring these acts and are being affected.
End of article.
Crime Tech Solutions (www.crimetechsolutions.com) is a fast growing software company based in Austin, TX. The company focuses on crime analytics, criminal intelligence, link analysis, and investigative case management solutions.
Hunting for D.B. Cooper – A study in analytics.
The following article originally appeared at In Public Safety, and is a highly recommended read. It was written by Erik Kleinsmith at American Military University.
Crime Tech Weekly is posting the article in its entirety for our readers’ convenience…
By Erik Kleinsmith
Staff, Intelligence Studies, American Military University
On November 24, 1971, a man using the name Dan Cooper purchased a $35 one-way airline ticket from Portland, Oregon, to Seattle, Washington. Not long after takeoff, he hijacked Northwest Orient Flight 305 and demanded $200,000 in cash along with two parachutes, which he received upon landing in Seattle. He then ordered the plane to take off and fly to Mexico City; during that flight, he jumped from the aircraft into the Oregon wilderness, securing his place as the only unsolved case in FAA history.

In early 2011, following a host of other investigations — both private and government-led — Tom Colbert picked up the trail of the man now known as D.B. Cooper. As an investigative reporter and producer living in Southern California, Colbert was tipped off by a source in the illicit drug trade who had credible — albeit circumstantial — evidence that D.B. Cooper was alive and living in California. Over the next few years, Colbert invested incredible amounts of time and personal resources toward tackling a 45-year-old mystery that so many other investigators before him had failed to solve.
A New Approach to Finding D.B. Cooper
Colbert assembled a large group of leading private investigators, detectives, attorneys, profilers and other subject matter experts into a group he called the “Cold Case Team.” He also knew he needed the expertise of intelligence professionals to help him organize and analyze all the evidence related to this case. While intelligence analysts almost always focus on using their skills for predictive analysis predictive analysis (i.e., what’s going to happen), Colbert knew having people proficient in intelligence collection and analysis would provide unique insight into a case that was decades old.
In December 2011, Colbert elicited my help while I was involved in an Army intelligence training contract. We had been associates and friends for a few years and he knew about my involvement in the Able Danger program. As a student, practitioner, developer and instructor of intelligence methodology, I was interested in his investigation because it was another chance for me to adapt intelligence analytical methods to a cold (very cold) case. I immediately agreed to support his efforts; he sent me a copy of a dossier on the man he suspected was D.B. Cooper.
It contained photos, maps, interview summaries and many other pieces of evidence connecting this man to the D.B. Cooper incident. Much of the initial information was secondhand and circumstantial, so Colbert was using it to provide further investigative leads for the Cold Case Team members.
Here is where I make my quick disclaimer: Collecting information on U.S. persons for intelligence purposes is prohibited by several federal regulations with very few specific exceptions. Even though I would be supporting a private investigation, I was working as a defense contractor at the time and therefore felt it was important to follow the spirit of these restrictions by creating products based only upon what the Cold Case Team provided. Neither myself nor my colleague independently searched for or collected any additional information for any part of this investigation.
That being said, it was an exceptional opportunity to use analytical intelligence techniques to assist in this investigation.
Using Link Analysis Techniques in the Investigation
In his meetings with various law enforcement officials, Colbert had grown frustrated that no one was taking the time to look through the dossier and consider the evidence. I gave it to one of my senior instructors, David D’Alessio, and asked him to make a link chart of associations using one of the best link analysis software programs available to us. A link chart is a graphic representation of the people, events, and significant items of interest (such as a bank account or address) associated with a particular subject. The key to these charts are the associations or “links” between each of the people, events and items in it.
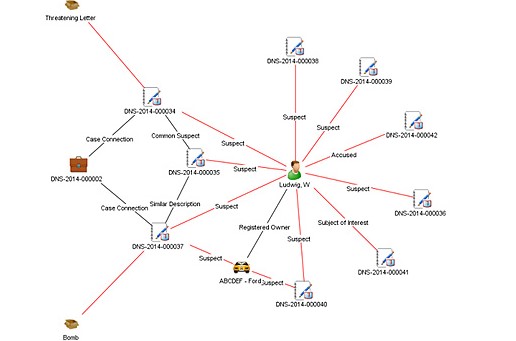
Creating this chart was a painstaking process because D’Alessio had to go through each paragraph line by line, identify the relative linkages between entities and enter them into the software program. The initial link chart started with the main suspect and then drew graphic linkages to all his known associates their connections to third parties, and a host of other associations to events, locations, aliases and specific pieces of physical evidence. Working with D’Alessio and Colbert over several iterations of this chart, we ended up with a 3×2 foot poster that, to the untrained eye, looked a lot like charts shown in court or on television shows like Law and Order. There were hundreds of links to the main suspect, the many aliases he used over the years to include military records and associations that placed him in the vicinity of the Portland, Oregon area during the time of the hijacking.
The benefit of link analysis charts is that they do more than just show connections between entities. A link chart tells a comprehensive visual story and conveys a dynamic and detailed summary of information from the document supporting it. This technique proved immensely successful, as the visual representation helped capture attention and interest from outside parties.
How Intelligence Analysis Aided in the Investigation
Besides taking text-based information and turning it into a graphic visualization for presentation purposes, a link chart also helped the investigation in other ways. First, Colbert and his team were able to see gaps in the information where investigators needed to dig deeper. He could also see which links were strong and which were weak or tenuous. The team could then plan their investigations more effectively by identifying which gaps needed to be filled and prioritize how to best use their limited resources.
This chart also had a psychological value to the Cold Case Team. In 2013, one of the team’s private investigators presented it directly to the suspect and asked him to come forward. The hope was that once the suspect knew there was a vast amount of information on the identity of D.B. Cooper (not to mention it featured his picture right at the center). Revealing this chart helped Colbert enter into negotiations with the suspect’s lawyer and he came very close to a deal that would potentially involve an admission. Unfortunately, Colbert and the Cold Case Team were turned down at the last minute due to what we believe was his fear of being connected to other illicit activities.
Why Law Enforcement Must Partner More Often with Intelligence Agencies
 Ultimately, this case demonstrates that intelligence analysis can play a crucial part in law enforcement investigations, both as a predictive asset as well as an investigative one. The D.B. Cooper investigation is decades old, but there are many other cases that are not. Other law enforcement agencies can use the techniques tested in this case to assist with other unsolved crimes, missing persons and patterns of criminal activity. It’s important for law enforcement authorities to remember that analysts in the intelligence field bring with them a toolkit that provides both unique and specialized analytical methods that can offer new perspectives. Bringing intelligence analysts into the fold of law enforcement can enhance a crime-solving team.
Ultimately, this case demonstrates that intelligence analysis can play a crucial part in law enforcement investigations, both as a predictive asset as well as an investigative one. The D.B. Cooper investigation is decades old, but there are many other cases that are not. Other law enforcement agencies can use the techniques tested in this case to assist with other unsolved crimes, missing persons and patterns of criminal activity. It’s important for law enforcement authorities to remember that analysts in the intelligence field bring with them a toolkit that provides both unique and specialized analytical methods that can offer new perspectives. Bringing intelligence analysts into the fold of law enforcement can enhance a crime-solving team.
The federal government has awesome capabilities in intelligence collection and investigation but they are not alone. There is an equally awesome, yet untapped capability, in the commercial sector and among academia to support investigations like this and other more current cases. There are uncounted numbers of undergraduate and graduate students in criminal justice, data analysis and intelligence studies courses who would be eager to support a future case. In addition, there are also many retired law enforcement and intelligence professionals who would be eager to lend their experience and subject matter expertise to similar cases and problem sets, if only to satisfy the investigative bug still within them.
While the FBI officially closed its investigation in the D.B. Cooper case earlier this year, it has not been closed in the eyes of the Cold Case Team. This team continues to move forward with its own investigation, relying on intelligence analysis methods to support them and continue to evaluate every bit of evidence in new ways.

Wynyard Group's slow, painful death arrives. Now, what about the customers?
October 28, 2016 – Crime Tech Solutions, a fast-growing and vibrant investigation software company based in Austin, TX, today announced a migration path for software users affected by the recent failure of New Zealand based Wynyard Group. Wynyard had positioned itself as a ‘leader in crime fighting software’, but never did find traction in the markets they coveted.
 Per Wynyard Group officials, the company has placed itself in voluntary administration as it battles crippling losses and missed revenue forecasts, leaving customers in the dark as to the future of their investment in the crime fighting technology.
Per Wynyard Group officials, the company has placed itself in voluntary administration as it battles crippling losses and missed revenue forecasts, leaving customers in the dark as to the future of their investment in the crime fighting technology.
For users of the Wynyard Group case management software, Crime Tech Solutions has introduced a comprehensive ‘path forward’ that includes, in some cases, a license-cost-free replacement of the Wynyard Group system with the popular and robust Case Closed™ investigative case management solution for law enforcement and commercial investigation agencies.
Case Closed Software was developed by investigation professionals and for investigation professionals, and is widely used by investigative agencies across North America.
“The objective”, said Crime Tech Solutions’ CTO Keith Weigand, “is to provide Case Closed software licenses to interested customers in exchange for the monies they already pay in annual maintenance and support.”
Tyler Wood, Operations Manager at Crime Tech Solutions, added “In essence, it’s a way to put what we think is better case management software into customers’ hands without the need to pay for expensive new software licenses.” While Wood acknowledges that there are internal costs associated with converting to any new solution, he feels that the intuitive and flexible nature of Case Closed is designed to mitigate those costs as much as possible.
About Crime Tech Solutions

Crime Tech Solutions is a low price / high performance innovator in crime analytics and law enforcement crime-fighting software. The clear price/performance leader for crime fighting software, the company’s offerings include Case Closed™ investigative case management and major case management, GangBuster™ gang intelligence software, powerful Sentinel Visualizer link analysis software, evidence management, mobile applications for law enforcement, comprehensive crime analytics with mapping and predictive policing, and 28 CFR Part 23 compliant criminal intelligence database management systems.
Critical Capabilities for Case Management Software? Case Closed!
In a February 2014 report, Critical Capabilities for Case Management, Gartner Group® defined the following 11 critical capabilities for investigative case management solutions. Crime Tech Solutions applies all of these critical capabilities to the powerful CASE CLOSED™ SOFTWARE for deployment at government and commercial investigative groups.
 Investigative case management solutions always require a broad range of data types, from highly structured data (such as an individual’s name, address or ID) to highly unstructured data (such as scanned images, blueprints, faxes, email communications, and audio or video files). CASE CLOSED supports this requirement with unique and patented functionality that allows investigators to interact with this content, using capabilities such as view or read, comment, highlight, update or change, and append.
Investigative case management solutions always require a broad range of data types, from highly structured data (such as an individual’s name, address or ID) to highly unstructured data (such as scanned images, blueprints, faxes, email communications, and audio or video files). CASE CLOSED supports this requirement with unique and patented functionality that allows investigators to interact with this content, using capabilities such as view or read, comment, highlight, update or change, and append.- Supports a broad range of collaboration services to facilitate individual and group interactions among all (internal and external) case participants. Collaboration among people (and even potentially with third party software) is incorporated into CASE CLOSED so that all interactions are recorded as part of the audit trail of how a case is handled. CASE CLOSED’s built-in support for e-mail communications, messaging, and alerting further supports collaboration efforts – across the aisle or across departments.
- Interoperates well with other external content and process services. Successful investigations and prosecutions often depend on external content and process services from repositories and applications. The attraction of CASE CLOSED’s open, standard specifications is that enterprises will know that integration with content repositories, web portals, and external software will require less custom code or specialized adapters.
- Provides vertical – and horizontal – specific data models, nomenclature, hierarchies and case life cycle management. Crime Tech Solutions has substantial experience in specific domains such as financial crimes and law enforcement investigations. We have transferred the lessons learned from consistent use cases and data definitions directly into CASE CLOSED. Because investigative case management solutions are difficult to design and architect, such out-of-the-box configuration patterns tend to accelerate the implementation time.
- Provides application adapters to industry and domain-specific environments. Crime Tech Solutions constantly endeavors to integrate with our customers’ critical systems of record. Crime Tech Solutions is well-acquainted with the specialized applications and data sources that dominate certain industries and domains, and thus CASE CLOSED offers accelerated integration with core systems of record.
- Provides comprehensive, highly configurable, role-based user experiences. Designed by former law enforcement officials, CASE CLOSED offers role-based user interfaces that tend to focus and simplify case handling – a critical step toward productivity gains. Crime Tech Solutions idealizes the interface between case workers, the content in cases and the managers who make decisions based on the work in progress.
- Provides business-role-friendly dashboards, metrics and reporting. Investigative groups want flexible and powerful case management solutions that allow them to manage and modify their own solutions, and to get meaningful information from them. As a result, CASE CLOSED provides access to case execution history, as well as appropriate dashboards, models, visualizations, reports and other tools to monitor, analyze and report on case handling.
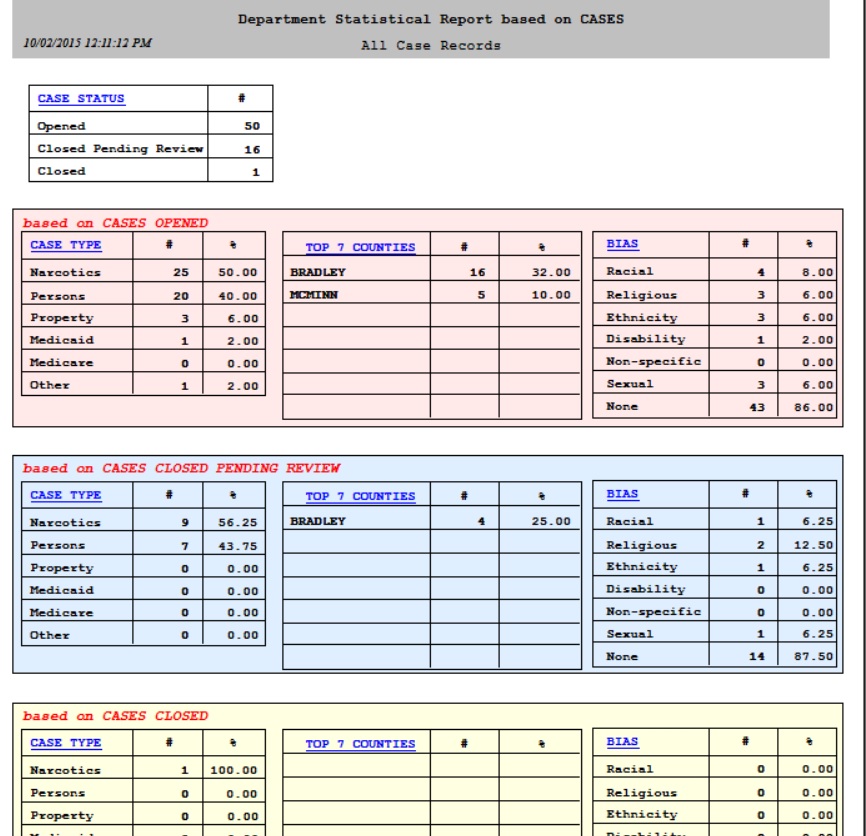
- Supports a broad range of case orchestration, from highly structured to highly unstructured flows. CASE CLOSED provides case orchestration for a spectrum of applications, ranging from very structured (predictable sequences of activities, usually represented in a flow model) to very unstructured (where progression is not easily predictable, and ad hoc activities may be invoked during the execution of the case). CASE CLOSED is also designed to easily adapt to the investigation group’s evolving business processes.
- Has been proven in deployments with 100,000 cases or more annually which is especially important for areas such as claims management and fraud investigations. While some investigative case management deployments do not require the volume capabilities of 100,000 cases or more, others do. Crime Tech Solutions’ software has been designed – and has been deployed – with very large scale case handling as a critical capability.
- Provides intelligent and versatile on-ramps and off-ramps for incorporating content (such as document capture, mobile phone cameras, fax servers and e-forms). It doesn’t matter how the information exists, whether on paper, in a digital document, as an image, in an email, in a voice mail or on the internet: CASE CLOSED is designed to allow capture and control with as much upfront intelligence as possible. Coupled with the ability to deliver various inbound content objects to a case folder is the ability for CASE CLOSED to generate outbound content (such as e-Brief), and the ability to export case data.
- Leverages models for easy adaptability of the solution. CASE CLOSED leverages appropriate data models to enable business and technical roles to easily adjust their solutions as needed. This includes easy adaptation of the design as well as easy adaptation of executable behavior. Importantly, CASE CLOSED provides the ability for dynamic and ad hoc adjustments to in-flight work. This means that the execution path of in-flight cases can be immediately adjusted in an unanticipated (ad hoc) way.
According to Gartner, investigative cases are the most complex in terms of process (workflow) and content (data). These cases are data-heavy. Often, data is captured as part of the case and relationships between data elements emerge over time. Patterns in the data are discovered, evaluated and acted on. Sequencing of actions on the case is very ad hoc, and event/milestone-driven.
Figure 1 shows examples of case-based processes that fall under each of these four use-case categories, and shows the structured vs. unstructured nature of the processes and data associated with each.
Figure 1. Case-Based Processes
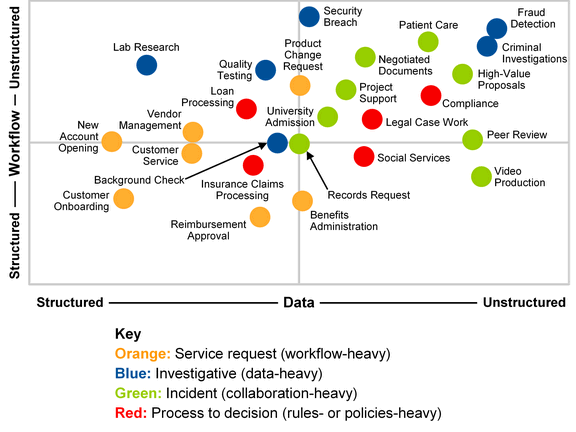
Source: Gartner (February 2014)
CASE CLOSED SOFTWARE from Crime Tech Solutions is designed specifically for the Investigative (data-heavy) market and resides in the upper right quadrant of diagram.
About the Author
Tyler Wood is Operations Director of Austin, TX based Crime Tech Solutions (www.crimetechsolutions.com). The company develops and deploys low price / high performance software for law enforcement including Case Closed™ investigative case management software, sophisticated Sentinel Visualizer™ link analysis and data visualization software, and CrimeMap Pro™ advanced crime analytics. The company also develops the popular GangBuster™ gang database, and IntelNexus™ criminal intelligence software for 28 CFR Part 23 compliance.
Another report slams predictive policing
Another report suggests that PredPol® (Predictive Policing) software does little to expand the tent when it comes to arrests.
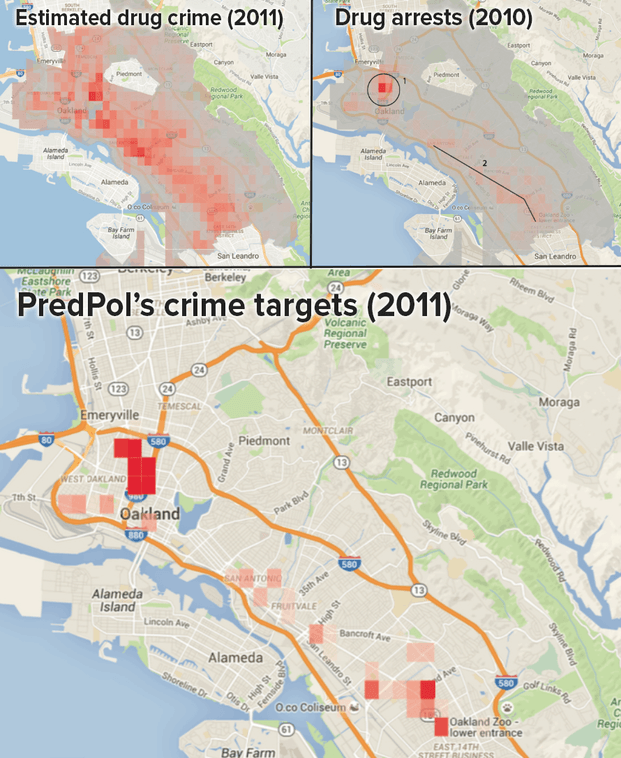
The full article at Boing Boing is HERE.
What's with all the "Creepy Clowns"?
It had to be in the weeks running up to Halloween, of course.
 Unless you’ve been hiding under a big red nose and novelty wig, you probably know that there has been a rash of ‘creepy clown’ sightings in communities across the country. These creepy clowns – and the related threats they seem to pose – seem to range from crazy hoaxes to credible events. So what in the name of big, floppy shoes is going on here?
Unless you’ve been hiding under a big red nose and novelty wig, you probably know that there has been a rash of ‘creepy clown’ sightings in communities across the country. These creepy clowns – and the related threats they seem to pose – seem to range from crazy hoaxes to credible events. So what in the name of big, floppy shoes is going on here?
Some arrests have been made. Schools have sent out warning letters. Social media is crawling with creepy, homemade clown videos. And the subject even came up at the White House media briefing this week.
We need an explanation for why, all of a sudden, there are creepy clowns running around our neighborhoods and – in some cases – our wild imaginations.
CNN posted six possibilities in an attempt to answer that very question. It’s a very good article and accompanying video. The possibilities, according to the folks they’ve interviewed range from folklore to viral marketing, and more. Of interest is the viewpoint of Benjamin Radford, author of the book “Bad Clowns“.
As the Los Angeles Times points out in an article HERE, the stupidity began in South Carolina with upsetting accounts of clowns attempting to lure children into the woods. (Those accounts seem to have proven false, by the way.) That said, the craze has expanded and, according to the same LA Times article, clown sightings were reported in Modesto, CA prompting police to issue a notice to residents that read: “If you see anything or anyone suspicious, including individuals dressed as clowns, to avoid contact and report the circumstances to us immediately.”

Even the Insane Clown Posse has weighed in on the subject. The Detroit-based hip-hop duo suggests the phenomenon is “basically nothing more than mass hysteria and moral panic.”
“Believe it or not, the same thing happened in 1981, too. Long before social media, Stephen King wrote (the horror classic) ‘It’ and Insane Clown Posse were in GRADE SCHOOL at the time! So there ARE no ‘killer clowns’ — it’s just jackasses being jackasses. Everyone relax!”, they posted.
In an article posted at Michigan Live HERE, it is pointed out that Loren Coleman, a cryptozoologist who studies the folklore behind mythical beasts such as Bigfoot and the Loch Ness Monster, came up with something called “The Phantom Clown Theory,” which attributes the proliferation of clown sightings to mass hysteria.
After some thorough research, it seems that the prevailing thought is that there are no credible threats from Creepy Clowns. Fuelling the hysteria, of course, are utterly false reports that continue to make the rounds in social media. Snopes, the myth debunking (or confirming) website talks about a report that creepy clowns are responsible for two dozen murders in Canada. Spoiler alert: It’s not true.
 Perhaps the biggest concern is that these creepy clowns take it too far, a la the snowball effect. We should be concerned that someone could be legitimately hurt as the trend grows. It’s even more possible that someone will take one of these creepy clowns as a legitimate threat and take matters into their own hands. We hope neither of those things happen, but we’d sure love to see a lot less of this clowning around.
Perhaps the biggest concern is that these creepy clowns take it too far, a la the snowball effect. We should be concerned that someone could be legitimately hurt as the trend grows. It’s even more possible that someone will take one of these creepy clowns as a legitimate threat and take matters into their own hands. We hope neither of those things happen, but we’d sure love to see a lot less of this clowning around.
About the Author
Tyler Wood is Operations Director of Austin, TX based Crime Tech Solutions (www.crimetechsolutions.com). The company develops and deploys low price / high performance software for law enforcement including Case Closed™ investigative case management software, sophisticated Sentinel Visualizer™ link analysis and data visualization software, and CrimeMap Pro™ advanced crime analytics. The company also develops the popular GangBuster™ gang database, and IntelNexus™ criminal intelligence software for 28 CFR Part 23 compliance.
Intelligent Gang Intelligence
The backbone of any functioning criminal intelligence unit is the strength of its intel files and/or gang records. Best practices for gang intelligence suggests that agencies should regularly update and contribute gang intelligence to a specialized gang intelligence system (aka gang database). These intelligence systems can manage and store thousands or millions of records of gangs, their activities, and their members.
With gang intelligence software, authorized users may read and update specific files, search and retrieve photos/videos/audio, and generally utilize the solution to assist investigation efforts. An example of some attributes stored within a gang intelligence system are:
- Activities

- Locations
- Names
- Vehicles
- Addresses
- Tattoos
- Marks and Scars
- Incidents
- Reports
- Tips
- Aliases
Properly utilized, the gang intelligence system should allow the collection, analysis, storage and retrieval of data that qualifies as criminal intelligence. The data should only be disseminated to agency members with a specific need, and that need should be logged as part of the dissemination.
Gang Intelligence Integrity
With a gang intelligence database, agencies must preserve the integrity of the system through security and access restriction from unauthorized users – internal and external – because of constitutional protection for individuals whose personal information is contained within the system.
Importantly, for gang intelligence, a rigid purging process must be adhered to as this ensures the integrity and credibility of the data. If, for example, a record has not been reviewed or appended for a period of five years, best practices suggest that the record be purged.
Access governance is also critical to gang intelligence systems to ensure integrity of the data entered and maintained and, importantly, to comply with applicable regional, state, and federal laws.
Gang / Criminal Intelligence and U.S. Law
 The United States Constitution prohibits the criminalization of mere membership in a gang (or other similar organization). There is nothing illegal about being a gang member, according to our country’s laws. However, it is perfectly legal for agencies to add gang members to the database even if no crime has been committed by that member.
The United States Constitution prohibits the criminalization of mere membership in a gang (or other similar organization). There is nothing illegal about being a gang member, according to our country’s laws. However, it is perfectly legal for agencies to add gang members to the database even if no crime has been committed by that member.
The tracking and storage of this data is widely criticized, however. Opponents suggest that agencies are profiling or targeting groups that are not engaged in criminal activities, and/or installing a ‘guilt by association’ mentality by tracking those members.
Conversely, advocates of gang intelligence database systems know that law enforcement has a legitimate interest in monitoring the individuals and groups engaged in ‘group criminal behavior’.
The back-and-forth between sides creates tension between the rights of society to be protected by law enforcement, and the individual privacy expectations of gang members.
CFR 28 Part 23
The result of these competing interests is something called Code of Federal Regulations, Title 28, Part 23 (CFR 28 Part 23) which details the requirements for gathering, entering, storing, and disseminating information about individuals and organizations (gangs) into an intelligence system.
 28 CFR Part 23 was designed as a regulation specific to multi-jurisdictional intelligence systems that have received federal grant funds for the development or purchase of the gang database. It is, however, an excellent guide for individual agencies, as the regulation attempts to fairly balance the intelligence needs of law enforcement against individual privacy requirements. In other words, it helps agencies get their jobs done without violating individual rights.
28 CFR Part 23 was designed as a regulation specific to multi-jurisdictional intelligence systems that have received federal grant funds for the development or purchase of the gang database. It is, however, an excellent guide for individual agencies, as the regulation attempts to fairly balance the intelligence needs of law enforcement against individual privacy requirements. In other words, it helps agencies get their jobs done without violating individual rights.
Compliance with 28 CFR Part 23 in Gang Intelligence
Gang and criminal intelligence data is defined within 28 CFR Part 23 as “data which has been evaluated to determine that:
A) it is relevant to the identification of, and the criminal activity engaged in by, an individual who – or an organization which – is reasonably suspected of involvement in criminal activity, and
B) meets criminal intelligence system submission criteria”
The ‘submission criteria’ is essentially the basis for something to be entered into the gang intelligence system. The criteria include the following:
- A reasonable suspicion that an individual is relevant to the criminal activity
- Prospective information to be entered is relevant to the criminal activity
- Information does not include data related to political, religious, or social views unless that information related directly to the criminal activity that formed the basis for focus on the gang or group
- Information was not obtained in violation of any federal, state, or local law or ordinance
- Information establishes sufficient facts to give trained law enforcement officials a basis to believe that an individual or gang/organization is involved in a definable criminal activity

As referenced above, 28 CFR Part 23 also indicates that information contained within a compliant database or criminal intelligence system must be reviewed and evaluated for relevance and importance every five years. Data that is deemed to be irrelevant and unimportant should be purged from the system. This is true even if the data is discovered to be noncompliant before five years.
Perhaps the most important element of a gang database system complying with 28 CFR Part 23 is that no information whatsoever from the database should be disseminated without a legitimate law enforcement reason, such as criminal investigation cases and charges being filed against a suspect.
Conclusion
If managing a gang intelligence system seems intimidating, it ought not be. If an agency desires to comply with 28 CFR Part 23, the rules for managing such as system are clearly spelled out. If an agency simply wants to collect and manage data outside of the federal guidelines – and has not accepted federal grant monies for such a program – they are free to do so as long as the system meets the security and ‘common sense’ guidelines that protect an individual’s right to privacy.
About the Author
Tyler Wood is Operations Director of Austin, TX based Crime Tech Solutions (www.crimetechsolutions.com). The company develops and deploys low price / high performance software for law enforcement including Case Closed™ investigative case management software, sophisticated Sentinel Visualizer™ link analysis and data visualization software, and CrimeMap Pro™ advanced crime analytics. The company also develops the popular GangBuster™ gang database, and IntelNexus™ criminal intelligence software for 28 CFR Part 23 compliance.




