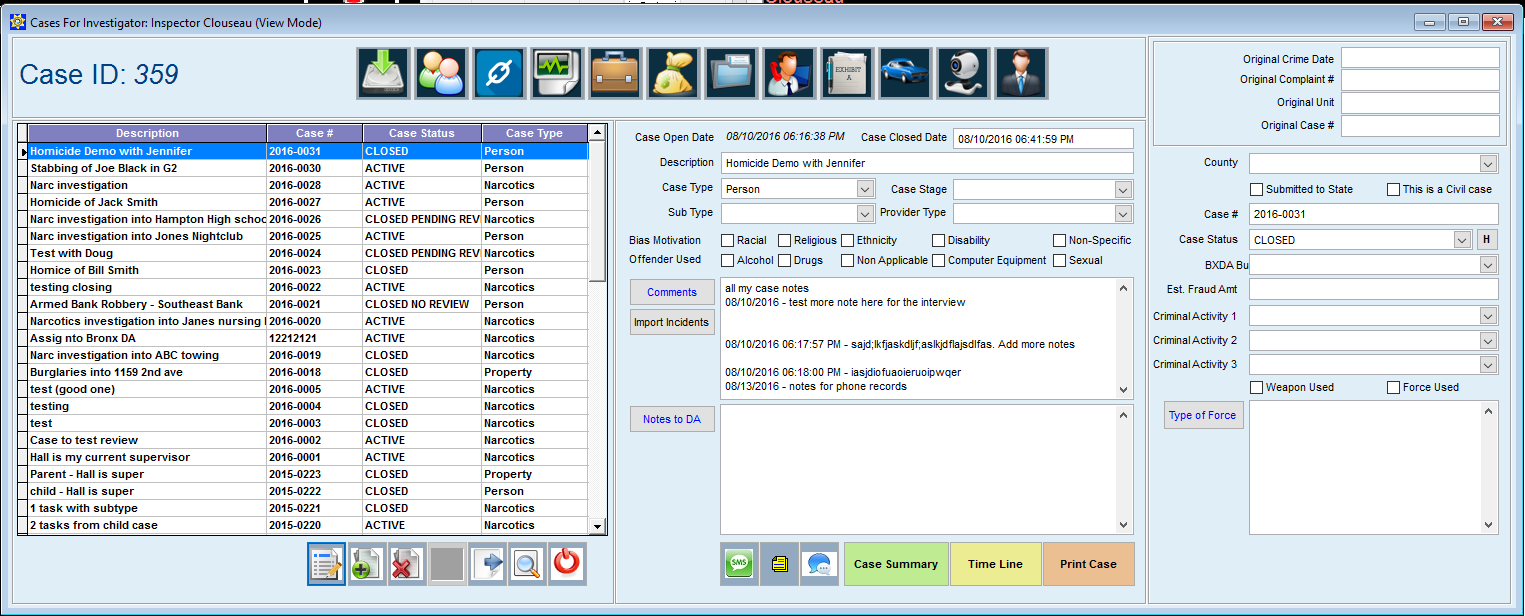
In a February 2014 report, Critical Capabilities for Case Management, Gartner Group® defined the following 11 critical capabilities for investigative case management solutions. Crime Tech Solutions applies all of these critical capabilities to the powerful CASE CLOSED™ SOFTWARE for deployment at government and commercial investigative groups.
 Investigative case management solutions always require a broad range of data types, from highly structured data (such as an individual’s name, address or ID) to highly unstructured data (such as scanned images, blueprints, faxes, email communications, and audio or video files). CASE CLOSED supports this requirement with unique and patented functionality that allows investigators to interact with this content, using capabilities such as view or read, comment, highlight, update or change, and append.
Investigative case management solutions always require a broad range of data types, from highly structured data (such as an individual’s name, address or ID) to highly unstructured data (such as scanned images, blueprints, faxes, email communications, and audio or video files). CASE CLOSED supports this requirement with unique and patented functionality that allows investigators to interact with this content, using capabilities such as view or read, comment, highlight, update or change, and append.- Supports a broad range of collaboration services to facilitate individual and group interactions among all (internal and external) case participants. Collaboration among people (and even potentially with third party software) is incorporated into CASE CLOSED so that all interactions are recorded as part of the audit trail of how a case is handled. CASE CLOSED’s built-in support for e-mail communications, messaging, and alerting further supports collaboration efforts – across the aisle or across departments.
- Interoperates well with other external content and process services. Successful investigations and prosecutions often depend on external content and process services from repositories and applications. The attraction of CASE CLOSED’s open, standard specifications is that enterprises will know that integration with content repositories, web portals, and external software will require less custom code or specialized adapters.
- Provides vertical – and horizontal – specific data models, nomenclature, hierarchies and case life cycle management. Crime Tech Solutions has substantial experience in specific domains such as financial crimes and law enforcement investigations. We have transferred the lessons learned from consistent use cases and data definitions directly into CASE CLOSED. Because investigative case management solutions are difficult to design and architect, such out-of-the-box configuration patterns tend to accelerate the implementation time.
- Provides application adapters to industry and domain-specific environments. Crime Tech Solutions constantly endeavors to integrate with our customers’ critical systems of record. Crime Tech Solutions is well-acquainted with the specialized applications and data sources that dominate certain industries and domains, and thus CASE CLOSED offers accelerated integration with core systems of record.
- Provides comprehensive, highly configurable, role-based user experiences. Designed by former law enforcement officials, CASE CLOSED offers role-based user interfaces that tend to focus and simplify case handling – a critical step toward productivity gains. Crime Tech Solutions idealizes the interface between case workers, the content in cases and the managers who make decisions based on the work in progress.
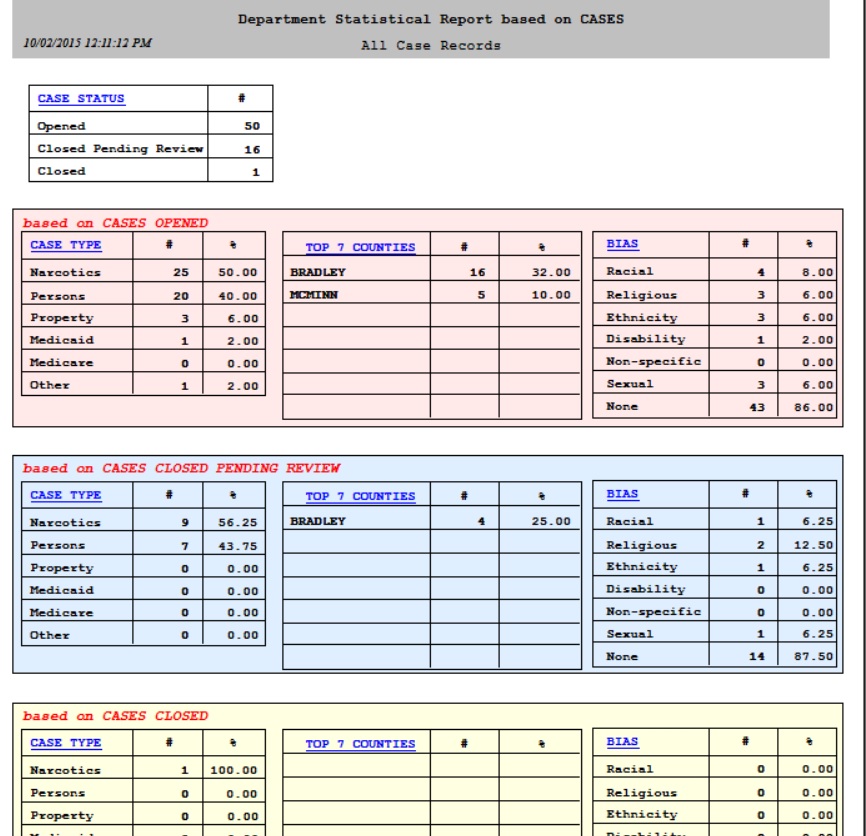
- Provides business-role-friendly dashboards, metrics and reporting. Investigative groups want flexible and powerful case management solutions that allow them to manage and modify their own solutions, and to get meaningful information from them. As a result, CASE CLOSED provides access to case execution history, as well as appropriate dashboards, models, visualizations, reports and other tools to monitor, analyze and report on case handling.
- Supports a broad range of case orchestration, from highly structured to highly unstructured flows. CASE CLOSED provides case orchestration for a spectrum of applications, ranging from very structured (predictable sequences of activities, usually represented in a flow model) to very unstructured (where progression is not easily predictable, and ad hoc activities may be invoked during the execution of the case). CASE CLOSED is also designed to easily adapt to the investigation group’s evolving business processes.
- Has been proven in deployments with 100,000 cases or more annually which is especially important for areas such as claims management and fraud investigations. While some investigative case management deployments do not require the volume capabilities of 100,000 cases or more, others do. Crime Tech Solutions’ software has been designed – and has been deployed – with very large scale case handling as a critical capability.
- Provides intelligent and versatile on-ramps and off-ramps for incorporating content (such as document capture, mobile phone cameras, fax servers and e-forms). It doesn’t matter how the information exists, whether on paper, in a digital document, as an image, in an email, in a voice mail or on the internet: CASE CLOSED is designed to allow capture and control with as much upfront intelligence as possible. Coupled with the ability to deliver various inbound content objects to a case folder is the ability for CASE CLOSED to generate outbound content (such as e-Brief), and the ability to export case data.
- Leverages models for easy adaptability of the solution. CASE CLOSED leverages appropriate data models to enable business and technical roles to easily adjust their solutions as needed. This includes easy adaptation of the design as well as easy adaptation of executable behavior. Importantly, CASE CLOSED provides the ability for dynamic and ad hoc adjustments to in-flight work. This means that the execution path of in-flight cases can be immediately adjusted in an unanticipated (ad hoc) way.
According to Gartner, investigative cases are the most complex in terms of process (workflow) and content (data). These cases are data-heavy. Often, data is captured as part of the case and relationships between data elements emerge over time. Patterns in the data are discovered, evaluated and acted on. Sequencing of actions on the case is very ad hoc, and event/milestone-driven.
Figure 1 shows examples of case-based processes that fall under each of these four use-case categories, and shows the structured vs. unstructured nature of the processes and data associated with each.
Figure 1. Case-Based Processes
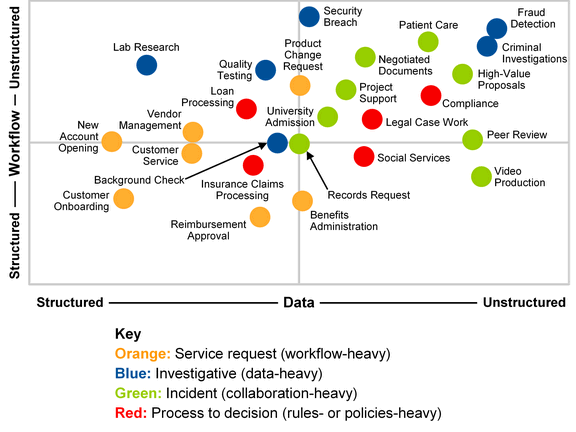
Source: Gartner (February 2014)
CASE CLOSED SOFTWARE from Crime Tech Solutions is designed specifically for the Investigative (data-heavy) market and resides in the upper right quadrant of diagram.
About the Author
Tyler Wood is Operations Director of Austin, TX based Crime Tech Solutions (www.crimetechsolutions.com). The company develops and deploys low price / high performance software for law enforcement including Case Closed™ investigative case management software, sophisticated Sentinel Visualizer™ link analysis and data visualization software, and CrimeMap Pro™ advanced crime analytics. The company also develops the popular GangBuster™ gang database, and IntelNexus™ criminal intelligence software for 28 CFR Part 23 compliance.
