The following article is the work of Joe Muscolino and originally appears at http://www.signature-reads.com/2017/02/jill-leovy-on-preventive-policing-and-its-effect-on-black-communities/ .
Crime Tech Weekly, is reposting for the convenience of our readers.
This may not come as a shock: there’s very little incentive in America to fix the homicide rates plaguing the poorer parts of our country’s cities. The fact that it’s not that shocking is perhaps part of the problem, and it’s one of the many points finely sharpened and well-defended by Jill Leovy in Ghettoside, a book that both documents a single murder investigation as well as zooms out to offer a searing look at the stasis we’ve settled into as a country.
Leovy, a reporter for the Los Angeles Times and creator of The Homicide Report, joins Signature in the video above to discuss the consequences to the policy of preventive policing. The upshot of preventive policing, Leovy argues, is the enforcement of minor crimes: “The result of that when you’re in it is that your son is getting pulled over every day, and humiliated, and hemmed up against a wall for seemingly no reason. And yet, your nephew’s murder is still unsolved.” This, in turn, encourages communities to enter the lawless world of self-policing.
The relationship between our nation’s police force and black communities remains so rocky and so politically charged that simply raising the subject is like blowing a battle horn. Leovy, though, does so in a way that antagonizes no one and instead, with empathy and insight, seeks to answer how we as a community and country can simply do better to solve the problem. Read on for the transcript of the video, or visit the ten most salient lessons we learned from Leovy’s book here.
We’ve always had these ways of kind of clearing the streets of people who might be threatening and might be menacing, and yet having a very poor record of solving homicides. You have a history of policing that focuses on nuisance policing, predictive policing, preventive policing, which translated means enforcing minor crimes.
The result of that when you’re in it is that your son is getting pulled over every day, and humiliated, and hemmed up against a wall for seemingly no reason. And yet, your nephew’s murder is still unsolved. You can’t but be infuriated by it, and many people are infuriated. It’s a huge incentive for retaliation if someone killed your brother and they’re walking around the neighborhood and the police aren’t going to do anything about it. The temptation to retaliate yourself becomes much greater.
I interviewed a mother of a murder victim the day after her son was murdered who told me that she knew who did it, they were neighbors down the street, and that they had come to her door after he died and taunted her and laughed at her for her grief, and told her that if she told police they would kill her, and so she was remaining silent and not cooperating with the police investigation. Even an outsider almost wants to kill in a situation like that, so for the people living this everyday it’s a constant temptation to self-police, and indeed you do see this high rate of self-policing in these neighborhoods.
-end-
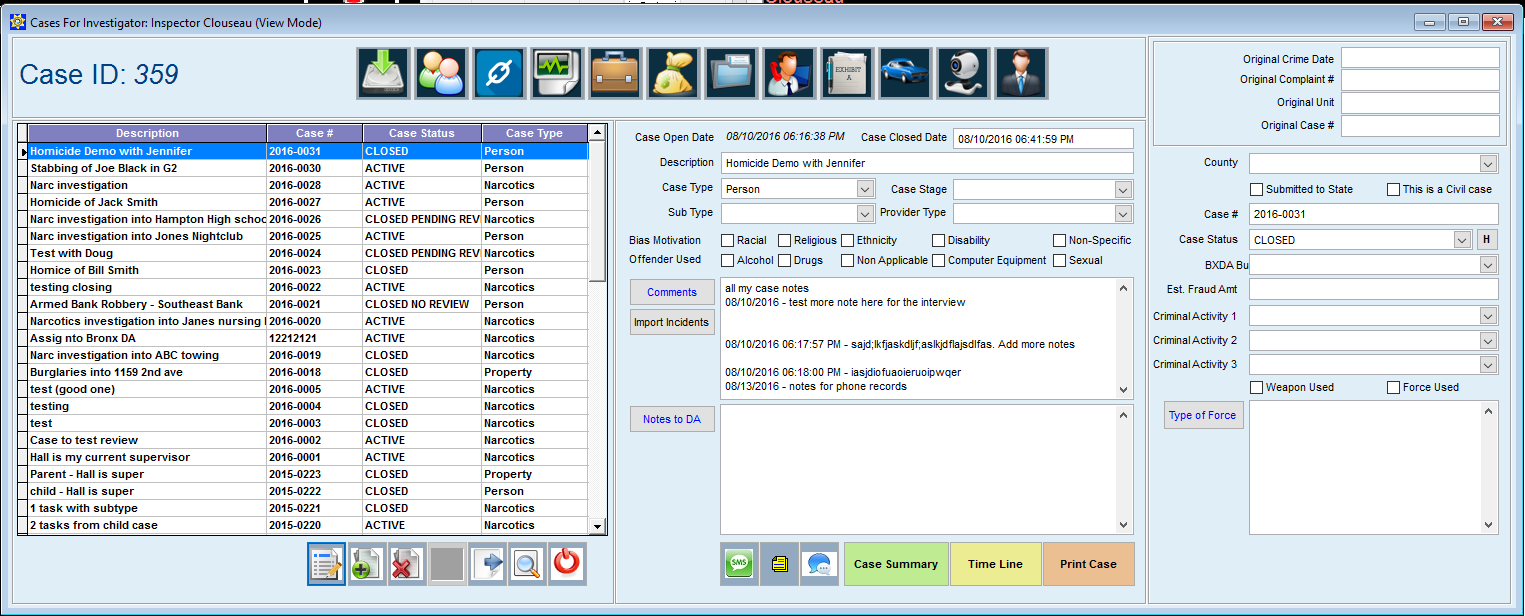
 The mid-sized Hawkeye State police department selected Case Closed due to its robust Property & Evidence functionality, along with its highly-regarded Investigation Case Management capabilities. Case Closed software is a feature-rich, affordable solution for agencies of all size. The core modules of the software include
The mid-sized Hawkeye State police department selected Case Closed due to its robust Property & Evidence functionality, along with its highly-regarded Investigation Case Management capabilities. Case Closed software is a feature-rich, affordable solution for agencies of all size. The core modules of the software include 
 The Bay Area city of approximately 300,000 residents is implementing the software company’s
The Bay Area city of approximately 300,000 residents is implementing the software company’s 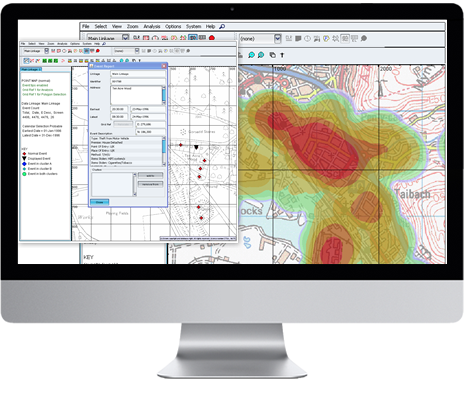 As we have written before, the true lifeblood of
As we have written before, the true lifeblood of 
 An
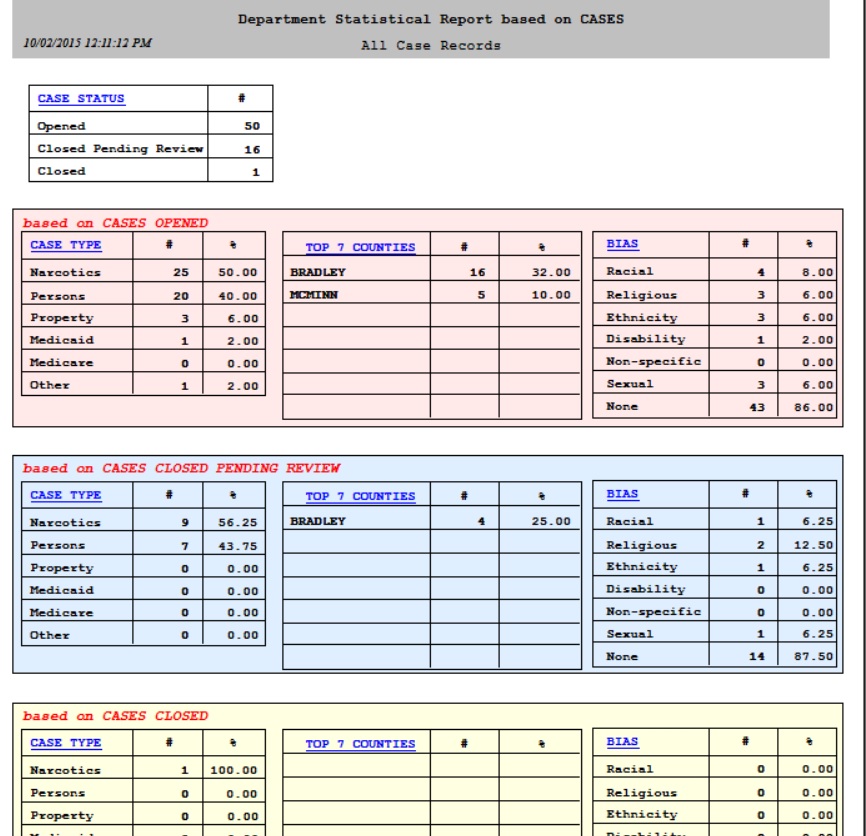
An 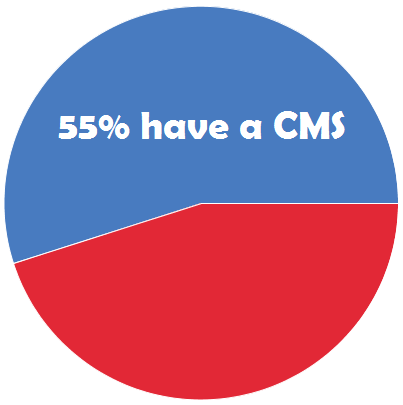 According to the study, just 55% of U.S. law enforcement agencies currently utilize investigative case management software (CMS), and the majority of users are unhappy with their current systems.
According to the study, just 55% of U.S. law enforcement agencies currently utilize investigative case management software (CMS), and the majority of users are unhappy with their current systems.




 hat sometimes aren’t reported, because people are scared or just don’t want to get involved,” said student Brian Romero.
hat sometimes aren’t reported, because people are scared or just don’t want to get involved,” said student Brian Romero. Some people may not agree because it abides by the First Amendment, and not all hate crimes show their intention online, although it is a step in the right direction to monitor those that are.
Some people may not agree because it abides by the First Amendment, and not all hate crimes show their intention online, although it is a step in the right direction to monitor those that are.

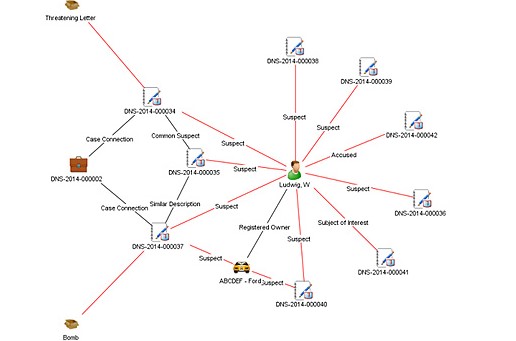

 Per Wynyard Group officials, the company has placed itself in voluntary administration as it battles crippling losses and missed revenue forecasts, leaving customers in the dark as to the future of their investment in the crime fighting technology.
Per Wynyard Group officials, the company has placed itself in voluntary administration as it battles crippling losses and missed revenue forecasts, leaving customers in the dark as to the future of their investment in the crime fighting technology.