 Posted by Crime Tech Solutions
Posted by Crime Tech Solutions
Law enforcement agencies everywhere are tasked with reducing and investigating crime with fewer and fewer resources at their disposal. “To protect and serve” is the highest responsibilities one can sign up for, particularly in light of recent well-publicized criticisms of police by activists in every city.
That responsibility weighs even heavier in a world with no shortage of criminals and terrorists. There’s never enough money in the budget to adequately deal with all of the issues that face an individual agency on a daily basis. Never enough feet on the street, as they say.
New Tools for Age-Old Problems
Perhaps that’s why agencies everywhere are moving to fight crime with an evolving 21st century weapon – law enforcement software including investigative case management, link and social network analysis, and, importantly, crime analytics with geospatial and temporal mapping.

Crime analytics and investigation software have proven themselves to be valuable tools in thwarting criminal activity by helping to better define resource allocation, target investigations more accurately, and enhancing public safety,
According to some reports, law enforcement budgets have been reduced by over 80% since the early 2000s. Still, agencies are asked to do more and more, with less and less.
Analytics in Policing

Analytics in law enforcement play a key role in helping law enforcement agencies better forecast what types of crimes are most likely to occur in a certain area within a certain window of time. While no predictive analytics solution offers the clarity of a crystal ball, they can be effective in affecting crime reduction and public safety.
Predictive analysis, in essence, is taking data from disparate sources, analyzing them and then using the results to anticipate, prevent and respond more effectively to future crime. Those disparate data sources typically include historical crime data from records management systems, calls for service/dispatch information, tip lines, confidential informant information, and specialized criminal intelligence data.
The Five W’s of Predictive Analytics
Within this disparate data lie the 5 W’s of information that can be used by crime analysis software to build predictions. Those key pieces include:
- Arrest records – who committed crimes
- Geospatial data – where crimes have occurred
- Temporal data – when crimes have occurred
- Statistical data – what crimes have occurred
- Investigation data – why (and how) the crimes occurred
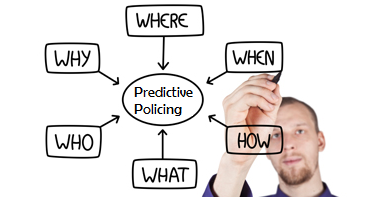
Using the 5 W’s, agencies are able to gain insight and make predictions about likely future criminal behavior. For example, if a certain type of crime (what) tends to occur in ‘this’ area (where) at ‘this’ time (when), and by ‘this’ type of individual (who) for ‘this’ reason (why)… it would be wise to deploy resources in that area at that time in order to prevent the incidents from ever occurring. This, of course, is a dramatic over-simplification of the types of analytics that make up predictive policing, but illustrates the general concept well.
Although criminals will always try to be one step ahead of the law, agencies deploying predictive analytics are able to maximize the effectiveness of its staff and other resources, increasing public safety, and keeping bad guys off the street.
More about Crime Tech Solutions
Crime Tech Solutions is an Austin, TX based provider of crime and fraud analytics software for commercial and law enforcement groups. Our offerings include sophisticated Case Closed™ investigative case management and major case management, GangBuster™ gang intelligence software, powerful link analysis software, evidence management, mobile applications for law enforcement, comprehensive crime analytics with mapping and temporal reporting, and 28 CFR Part 23 compliant criminal intelligence database management systems.