To all of our readers… Have a great Christmas season and see you in 2014!
Posted by Douglas Wood, Editor. http://www.linkedin.com/in/dougwood
Another case of worker’s compensation premium fraud. You may recall my previous post on this subject. It’s worth reading.
http://manasquan.patch.com/groups/police-and-fire/p/owner-of-wallbased-roofing-company-indicted-for-fraud-and-theft
You’ve heard of robbing the cradle. This is robbing the casket, I suppose…
http://www.13abc.com/story/24279926/funeral-home-owner-charged-with-theft-fraud
He’ll have 8 years to choo choo choose a new way to make a living…
http://newyork.cbslocal.com/2013/12/21/8-years-in-prison-for-former-lirr-conductor-in-fraud-scheme/
What happens in Vegas… Stays in a federal penitentiary.
http://www.lasvegassun.com/news/2013/dec/20/man-gets-11-years-15-million-mortgage-fraud-scheme/
Tag Archives: Doug Wood
Part 2: Investigating the Investigations – X Marks the Spot
Posted by Douglas Wood, Editor. http://www.linkedin.com/in/dougwood
Part One of this series is HERE.
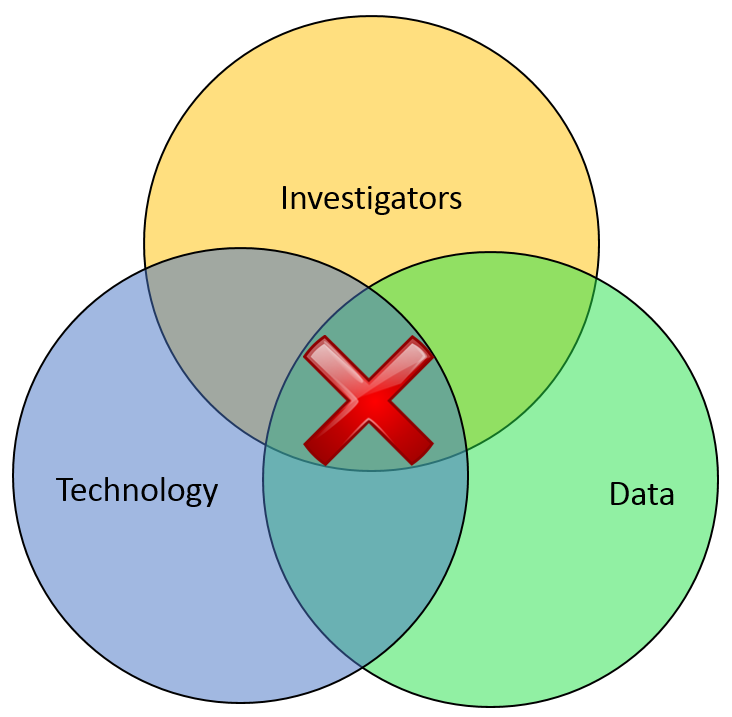
Most of the financial crimes investigators I know live in a world where they dream of moving things from their Inbox to their Outbox. Oh, like everyone else, they also dream about winning the lottery, flying without wings, and being naked in public. But in terms of the important roles they perform within both public and private sectors, there is simply Investigating (Inbox) and Adjudication (Outbox). Getting there requires a unique blend of their own capabilities, the availability of data, and the technology that allows them to operate. In the diagram below, ‘X‘ marks the spot where crimes are moved from the Inbox to the Outbox. Without any of those three components, an investigation becomes exponentially more difficult to conclude.
In part one of this article two weeks ago, I wrote about the Investigation Management & Adjudication (IMA) side of financial crimes investigations. I coined that term to call out what is arguably the most integral component of any enterprise fraud management (EFM) ecosystem. The original EFM overview is here.
“The job is almost unrecognizable to those who once used rotary phones in smoke filled offices…
Twenty years ago, IMA was based primarily upon human eyes. Yes, there were technology tools available such as Wordperfect charts and Lotus 1-2-3 spreadsheets, but ultimately it was the investigator who was tasked with finding interesting connections across an array of data elements including handwritten briefs, telephone bills, lists of suspect information, and discussions with other investigators. The job got done, though. Things moved from the Inbox to the Outbox, arrests were made and prosecutions were successful. Kudos, therefore, to all of the investigators who worked in this environment.
Fast forward to today, and the investigator’s world is dramatically different. The job is the same, of course, but the tools and mass availability of data has made the job almost unrecognizable to those who once used rotary phones in smoke filled offices. Organizations began building enterprise data warehouses designed to provide a single version of the truth. Identity Resolution technology was implemented to help investigators recognize similarities between entities in that data warehouse. And today, powerful new IMA tools are allowing easy ingestion of that data, improved methods for securely sharing across jurisdictions, automated link discovery, non-obvious relationship detection, and interactive visualization tools, and -importantly – packaged e-briefs which can be understood and used by law enforcement, prosecutors, or adjudication experts.
“Without any of these components, everything risks falling to the outhouse…
With all these new technologies, surely the job of the Investigator is becoming easier? Not so fast.
IMA tools – and other EFM tools – do nothing by themselves. The data – big data – does nothing by itself. It just sits there. The best investigators – without tools or data – are rendered impotent. Only the combination of skilled, trained investigators using the best IMA tools to analyze the most useful data available results in moving things from the Inbox to the Outbox. Without any of these components… everything eventually risks falling to the Outhouse.
Kudos again, Mr. and Mrs. Investigator. You’ll always be at the heart of every investigation. Here’s hoping you solve for X every day.
Bananas, Politicians and Navy Blue: Selected Financial Crimes Snapshot 01/02/2013
Posted by Douglas Wood, Editor. http://www.linkedin.com/in/dougwood
Be sure to check out “Investigating the Investigations” Part One and Two! In the meantime, here are this week’s weird headlines:
I can’t believe he tried to slip this one past investigators. Maybe he’ll win on a peel…
http://www.wjla.com/articles/2013/12/maurice-owens-to-appear-in-court-on-metro-banana-peel-fraud-charges-97541.html
A dishonest politician? Now I’ve heard everything!
http://www.wishtv.com/news/indiana/nw-indiana-politician-to-admit-6-wire-fraud-counts
He couldn’t just wait for Black Friday like everyone else?
http://www.hillsdale.net/article/20131202/NEWS/131209942
Navy blue about this one…
http://www.pbs.org/newshour/bb/military/july-dec13/navy_11-27.html
Death Deterrents, Texas Teeth, and 'The Big Easy' Money – Selected Financial Crimes Snapshot 11/07/2013
Posted by Douglas Wood, Editor. http://www.linkedin.com/in/dougwood
Chinese woman sentenced to death for fraud. Ouch. That’s definitely a deterrent…
http://abcnews.go.com/International/wireStory/chinese-woman-sentenced-death-200m-fraud-20785445
70 year old Orthodontist sentenced to two years. Fraud laws in Texas have some real teeth in them…
http://www.kfdm.com/shared/news/top-stories/stories/kfdm_vid_7425.shtml
Think they’ll throw the (school) book at her?…
http://www.philly.com/philly/news/local/20131107_Charter_school_founder_s_fraud_trial_gets_underway.html
New Orleans cops charged. To Protect and Serve (themselves)…
http://www.wwltv.com/news/eyewitness/mikeperlstein/Two-NOPD-officers-have-first-court-date-on-payroll-fraud-issue-231068431.html
To 314(b) or not to 314(b)?
Posted by Douglas Wood, Editor. http://www.linkedin.com/in/dougwood
FinCEN today (November 1, 2013) released a fact sheet regarding data sharing between financial institutions under the Section 314(b) of the US Patriot Act.
314(b) provides financial institutions with the ability to share information with one another, under a safe harbor that offers protections from liability, in order to better identify and report potential money laundering or terrorist activities. 314(b) information sharing is a voluntary program, and FinCEN has always encouraged its use.
A few years ago, I spent considerable time looking at the overall 314(b) program. I interviewed dozens of Chief Compliance Officers (CCO) and AML/Fraud experts. I found that, despite the benefits to financial institutions – reduction of fraud loss, more complete SARs filings, shedding light on financial trails, etc – the program was not particularly well-utilized. The system, for all it’s good intentions, is very manual.
Imagine you are a 314(b) officer at a financial institution. Your job is to facilitate the data sharing amongst the community. So, much of your time is spent interacting with your CCO on which specific cases should be shared, and with whom. When you get that information, you open up you financial crimes investigation tools, and begin contacting your counterparts across the U.S. and asking them “Hey, do you know anything about Douglas Wood?” You’re calling the other officers completely blind with no idea whatsoever if they know Doug. In the meantime, your voicemail inbox is being flooded with other calls from other institutions asking if you know a bunch of other people (or entities).
Finding the institutions that know Douglas Wood is a lot like looking for a needle in a haystack… except you don’t know which haystacks to look in. The system too often grinds to a halt, despite some excellent work being done by 314(b) officers across the country. There has to be a better way, and some have proposed a data contribution system where financial institutions upload their bad guy data into one large third-party haystack, making the needle a little easier to find. As an advocate for the use of technology in the fight against financial crimes, I hope that model finds some success. The problem, of course, is that banks are LOATHED to put their data in the hands of a third party. Also, it’s typically up to each individual bank to decide if and when they choose to upload their data to be inter-mingled with other institutions. Far too often, it is not entirely reliable and not particularly current.
There is a better way. Several years ago, working with some tech-savvy employees, I envisioned a member-based 314(b) program where each institution maintained total control of their data. The model does not require individual banks to contribute their data for inter-mingling. All ‘bad guy’ data sits and remains securely behind the banks’ respective firewalls. When an individual bank sends out a request to find out who, if anyone, may have information about a suspicious entity, the request is systematically sent out to all members using a secure network such as SWIFT, for example. That electronic search returns to the querying bank only a risk score which indicates the likelihood that another member is investigating the same entity.
No personally identifiable information (PII) is ever shared, yet the search is productive. The enquiring bank now knows that the person of interest was found in the bad guy data from other participating institutions. With this information in hand, the respective 314(b) officers can move their voicemail exchanges from “Have you ever heard of Douglas Wood” to “We’re both investigating Douglas Wood… let’s do it together.” The time-consuming, manual efforts are dramatically reduced and more bad guys are put away.
So if the question is to 314(b) or not to 314(b), perhaps the answer lies in data privacy compliant technology.
Drag Queens, Silk Road Shutdowns, and Video Killed the Real Estate Fraud – Selected Financial Crimes Snapshot 10/29/2013
Posted by Douglas Wood, Editor. http://www.linkedin.com/in/dougwood
Perhaps there is no Spanish term for “lay low, fraudster”?
http://www.latimes.com/local/lanow/la-me-ln-youtube-video-leads-to-arrest-of-man-wanted-in-fraud-case-20131010,0,1636077.story#axzz2j9ClBao3
Feds take down “eBay for drugs” site. I wonder if “Buy it Now” was popular?
http://krebsonsecurity.com/2013/10/feds-take-down-online-fraud-bazaar-silk-road-arrest-alleged-mastermind/
Drag Queen Shakedowns… Only on Bourbon Street.
http://theadvocate.com/news/7402011-123/celebrity-scam-artist-arrested-in
Lottery Fraud – How lucky can you get?
Posted by Douglas Wood, Editor.
Two weeks ago, I wrote in this space about some interesting experiences I’d had working through Workers Compensation Premium Fraud at a government run program. This week, I received a fraud alert about a retailer being banned from ever selling lottery tickets, and it reminded me of a great exercise I underwent with a government run Lottery corporation several years ago.
Lottery retailer fraud is simple and widespread. NBC Dateline ran a two hour episode several years ago, outlining the problem and going undercover to catch some bad guys in action.
In a nutshell, there are many unscrupulous retailers who outright lie to patrons when asked to check their numbers. Joe the customer hands the ticket over to the clerk and asks her to see if it’s a winner. She scans the barcode and says “Sorry, Joe… you didn’t win“. Then, as Joe heads out the door, she picks the ticket up from the trash bin knowing full well that it’s a big winner. Here’s a real life example.
How bad is the problem? According to Dateline NBC, a Philadelphia retailer cashed eighteen lottery tickets in three months for a total of $45,000. In New Jersey, a retailer cashed 105 lottery tickets for more than $236,000. In Illinois, it found one store where four employees and five of their relatives cashed a total of 556 winning tickets, for more than $1,600,000. In California, lottery investigators were seeing the same thing. In fact, in 2007, the five most frequent winners in California were retailers. One store owner in Los Angeles allegedly cashed 121 tickets for more than $160,000.
As a result of shrinking public trust and outrage, many lottery corporations have taken to more tightly scrutinize ‘winning’ ticket claims from lottery retailers. What, though, if the lottery clerk has her husband cash the ticket? Or her next door neighbor? How can you scrutinize large winning ticket claims without grinding the process to a halt?
That’s precisely where my customer was when they called me.
As with any fraud prevention program, the availability of data was of utmost importance as we scoped out the technology solution. The lottery corporation obviously knew who their retailers were (XYZ Groceries, ABC Petroleum, etc) but how did that help point to a specific Suzie Employee within that retailer? After all, companies weren’t cashing in winning tickets. People were.
Well, we helped them realize that they had employee names as a result of the mandatory training they offered retailers for handling sales of lottery tickets. Each employee of a retailer was required to take a brief online course for certification purposes, and entered some of their personal data (name, date of birth) in order to begin the training.
That got us through step one – the employees. In order to get to the next level of culprit (the family or neighbors of employees), we incorporated publicly available data into the mix.
Through a defined process of business discovery and problem resolution, we designed a process where individuals redeeming winning tickets above a certain value would be compared to the data of retail employees. If it was determined that a winner closely resembled a retail employee, an alert was automatically generated for investigators.
If a winner was determined to be closely acquainted to a retail employee via relationship-detection technology and public data, an alert was again generated. The specifics of how relationships were determined and analyzed won’t be disclosed for obvious reasons, but one example would be a shared address or telephone number.
This particularly lottery corporation was fortunate that they had a mechanism by which to collect employee data. In meeting with dozens of other Lotteries in the years since, I’ve learned that not enough of them have a similar process in place. Unfortunately, without that initial data set, it’s more difficult to detect this type of fraud.
In the case of my client, however, they began immediately seeing benefits in the new process and several fraudulent retailers were exposed. It was some very interesting work, and a cool exercise in problem solving for complex fraud.
Posted by Douglas G. Wood. Check out my site at www.crimetechsolutions.com
Shockers, Lawyers, and Worst Boss Ever – Selected Financial Crimes Snapshot 10/11/2013
Posted by Douglas Wood, Editor. http://www.linkedin.com/in/dougwood
Shipping a car to Nigeria? Seems like an awful lot of work for a fairly stupid scam…
http://finance.yahoo.com/news/fraud-conviction-man-reported-car-133000007.html
SHOCKER! Online advertising is often fraudulent!
http://www.sfgate.com/technology/businessinsider/article/4-Ad-Execs-Just-Admitted-That-Online-Adtech-Is-4888221.php
Why is it so darned hard to feel sorry for lawyers?
http://www.sun-sentinel.com/news/local/crime/fl-rothstein-attorney-arraign-20131011,0,4341539.story
“Here’s your paycheck. Gonna need half of it back, though.” Worst. Boss. Ever.
http://www.latimes.com/local/lanow/la-me-ln-contractor-indicted-fraud-wages-20131010,0,296609.story
Posted by Douglas G. Wood. Click on ABOUT for more information and follow Financial Crimes Weekly on Twitter @FightFinCrime
Gypsies, Tramps, and Thieves – Selected Financial Crimes Snapshot 10/4/2013
Posted by Douglas Wood, Editor. http://www.linkedin.com/in/dougwood
I’m sure the Gypsies just wanted to help… No?
http://www.greeleygazette.com/press/?p=23299
You just can’t make this stuff up. Thai prostitutes hired to kill rhinos in trophy hunting scam.
http://planetsave.com/2011/07/24/thai-prostitutes-hired-to-kill-rhinos-in-south-african-trophy-hunting-scam/
Ummm… she may have had a ‘brain injury’ when she thought this one up….
http://www.cnn.com/2013/09/30/justice/boston-one-fund/index.html
Good cop? No… bad cop
http://www.upi.com/Top_News/US/2013/10/04/Miami-police-officer-found-guilty-of-identity-theft-tax-fraud/UPI-26251380893747/
Posted by Douglas G. Wood. Click on ABOUT for more information and follow Financial Crimes Weekly on Twitter @FightFinCrime
Premium Fraud – Piano Tuners and Window Washers?
Posted by Douglas Wood, Editor.
I came across a news article earlier this week regarding a business owner convicted of fraudulently avoiding worker’s compensation premiums. The link to that news article is below.
It brought to mind some fascinating work I was involved with a few years ago to help a state run Worker’s Compensation Bureau more effectively detect this kind of fraud. Their biggest concern was recovering monies owed by companies who illegally misrepresent themselves for the purpose of reducing or avoiding the payment of premiums. Here’s how these scams work…
Intentional Misclassification: A crooked business claims that employees work safer jobs than they really do. Perhaps a high-rise window washer is falsely classified as a piano tuner. Much lower premiums, obviously.
Employee Misrepresentation: A business says it has fewer employees or a lower payroll than it actually does.
Coverage Avoidance/Experience Modification: A business simply doesn’t buy the required insurance, hoping state officials won’t notice. If the state learns of the avoidance, the company will simply close, then re-emerge as a ‘new’ company’ in order to avoid the payments.
So the state bureau I worked with needed to understand when, for example, a ‘piano tuner’ was requesting a permit for high rise window washing. Red flag, right? Or when an five separate claims were filed by employees of a company who stated they had only 3 employees. Another red flag.
Oh, and what about a new company registrant whose owners, address, telephone number, and line of business are all suspiciously similar to those of a recently closed business who owed thousands of dollars in back premiums. BIG red flag.
The state itself had all of the data it needed to detect this fraud. The problem, as is often the case, is that the data sat in different jurisdictions. Working with our client, we helped those other jurisdictions – Business Registrations, Building Permits, Tax Departments, etc. – understand the value of sharing that data. That’s the key to this success story – data sharing. Without it, problems are much more difficult to solve.
Ultimately, we delivered a system that included business rules, anomaly detection, and social network analysis. It provided the bureau with the ability to flag those anomalies using their existing data infrastructure and fraud alert output from those other state agencies.
With the tools in place to trigger those red flags, the agency immediately began recovering lost premiums, prosecuting offenders, and ultimately adding much needed revenue to the state coffers.
Fraudsters who choose to commit financial crimes are always coming up with new scams. Those of us committed to delivering true technology innovations through data sharing are starting to put a real dent in their chosen profession, though.
Maybe they can tune pianos instead. Do they need a building permit for that?
http://www.workerscompensation.com/compnewsnetwork/mobile/news/17511-investigation-leads-to-conviction-of-ca-business-owner-for-insurance-fraud.htmlgus
Posted by Douglas G. Wood. Click on ABOUT for more information and follow Financial Crimes Weekly on Twitter @FightFinCrime