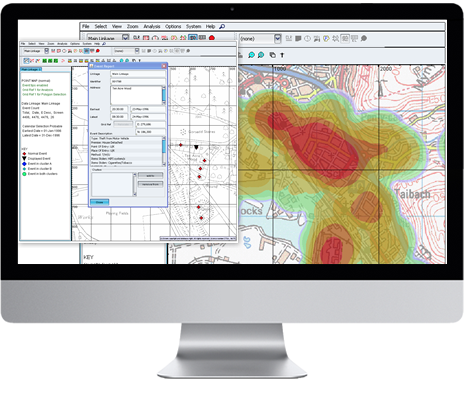
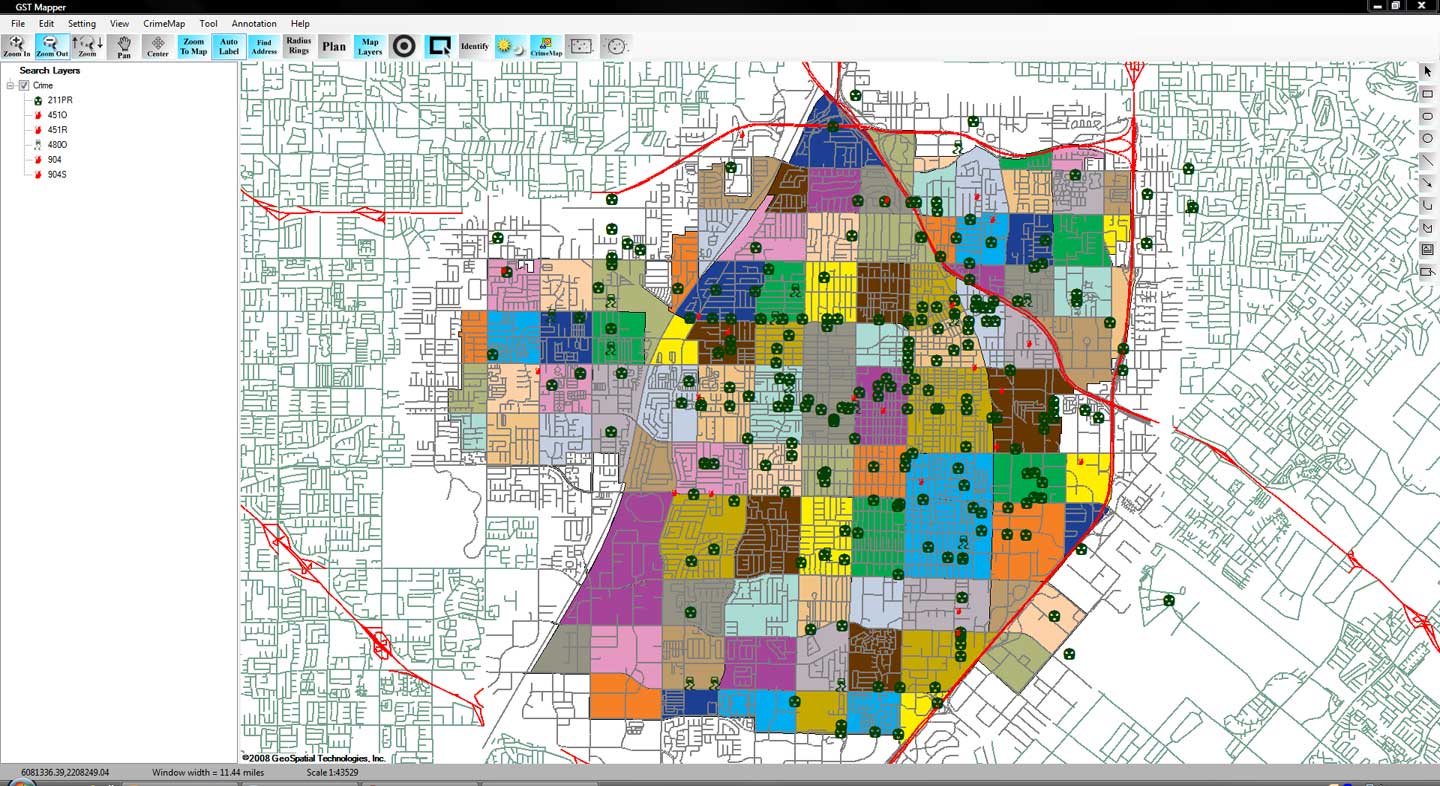
Lost in the news of the recent demise of New Zealand based crime-fighting software developer Wynyard Group, is an interesting report published just weeks before the company ceased operations.
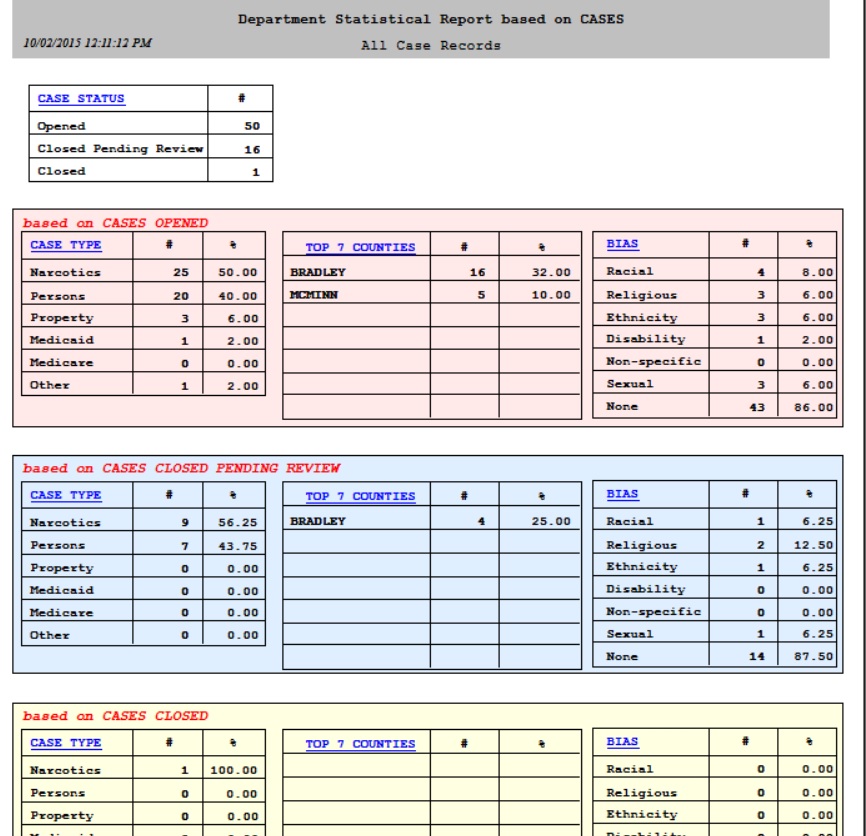
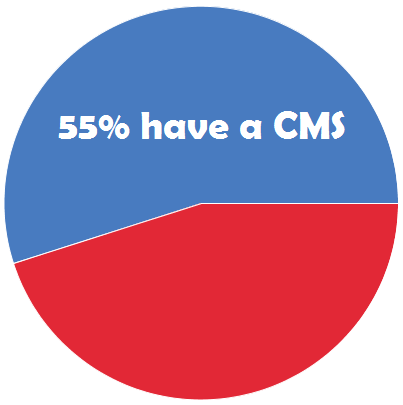 According to the study, just 55% of U.S. law enforcement agencies currently utilize investigative case management software (CMS), and the majority of users are unhappy with their current systems.
According to the study, just 55% of U.S. law enforcement agencies currently utilize investigative case management software (CMS), and the majority of users are unhappy with their current systems.
Thirty-seven percent of the study respondents are not currently using any type of automated system, and rely mainly on paper files and spreadsheets to manage their investigations.
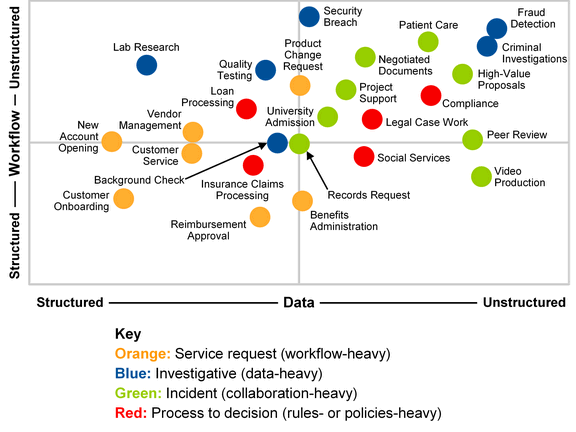
Investigative case management software has long been the domain of larger agencies and departments, and is only now truly affordable for smaller departments. The software allows investigators to manage the investigation process from start to finish. The more robust software allows agencies to assign cases and tasks, manage deadlines, store and maintain physical and multimedia evidence, and to search for relevant information across disparate databases.
According to a press release issued at the time, the survey queried users on how likely they would be to recommend their current system to another agency. While most users were unhappy with their current investigative case management system, there was a clear difference between agencies using commercial-off-the-shelf (COTS) software and those using home grown, legacy systems. The latter fared very poorly in the survey results.
The survey also measured the use of smart devices by front-line officers. Forty three percent indicated that they currently utilize smart phones and tablet computers, and 23% indicated they had neither device.
The most-desired features in investigative management software include:
- Management Dashboards
- Reports – Standard and ad hoc
- Case Assignment and Reminders
- Actions and Incident Management
- Mobile and Front-Line Case Access
- Evidence Management and Chain-of-Custody
- Multimedia Handling
- Audit Logs
- Collaboration
- Gangs and Organized Crime Management
- Data Visualization and Link Analysis
- Case Closure / Evidence Brief
An investigative case management system for law enforcement and commercial investigation agencies is rapidly becoming a ‘must-have’. In an era of shrinking budgets and competing resources, a high value is placed on getting the biggest ‘bang for the buck’. The study indicates that agencies are looking to maximize the value of their investigative case management software by incorporating a robust feature set with an affordable price.
Case Closed Software, a division of Crime Tech Solutions, is a powerful and affordable investigative case management solution for law enforcement agencies. Case Closed is also available via the cloud with the innovative Case Closed Cloud. Created by former law enforcement investigators, the COTS software is designed with ease-of-use in mind. The software is deployed in agencies – large and small – across the country.
El Paso, TX – Gang investigators were told a suspect in surveillance footage matched the description of “Flaco”, a known gang member in the area.
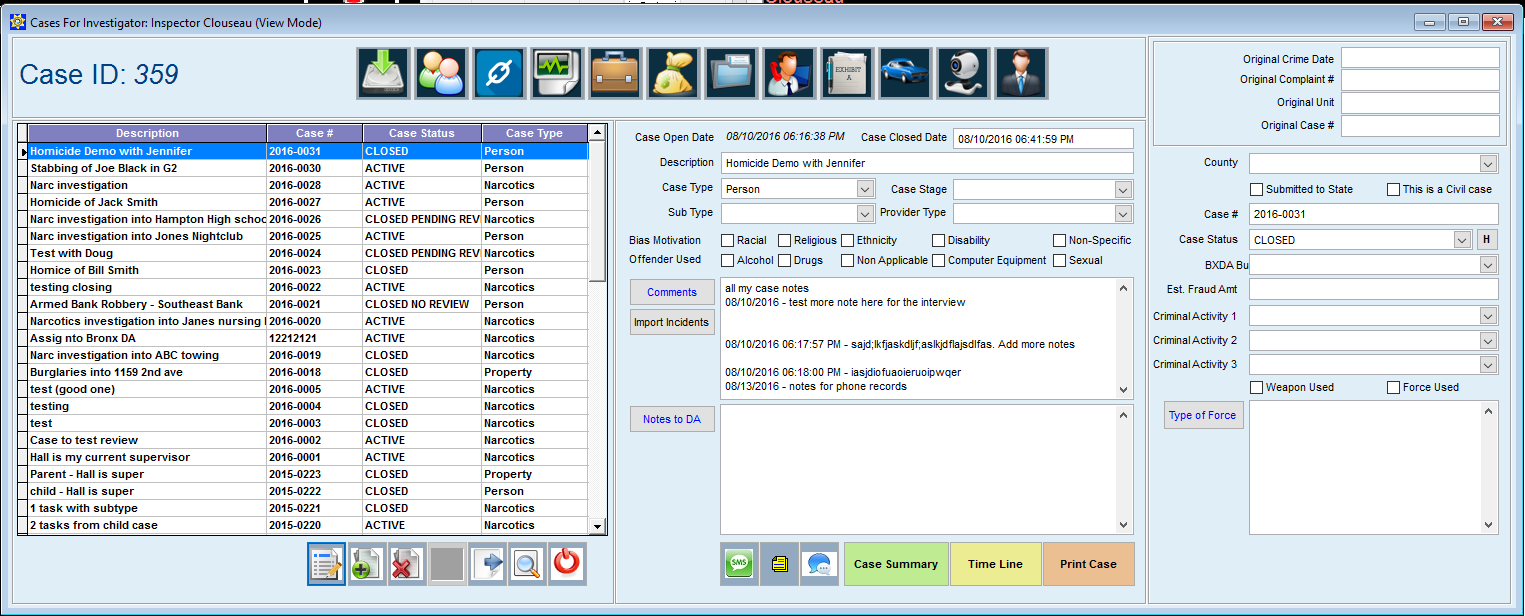
 The mid-sized Sheriff’s Department in the Volunteer State chose Case Closed Software after a long, thorough search for a solution provider capable of delivering “a feature-rich, affordable solution for managing investigations and the investigative unit”. The core modules of the software include
The mid-sized Sheriff’s Department in the Volunteer State chose Case Closed Software after a long, thorough search for a solution provider capable of delivering “a feature-rich, affordable solution for managing investigations and the investigative unit”. The core modules of the software include 
 According to the study, just 55% of U.S. law enforcement agencies currently utilize investigative case management software (CMS), and the majority of users are unhappy with their current systems.
According to the study, just 55% of U.S. law enforcement agencies currently utilize investigative case management software (CMS), and the majority of users are unhappy with their current systems. Per Wynyard Group officials, the company has placed itself in voluntary administration as it battles crippling losses and missed revenue forecasts, leaving customers in the dark as to the future of their investment in the crime fighting technology.
Per Wynyard Group officials, the company has placed itself in voluntary administration as it battles crippling losses and missed revenue forecasts, leaving customers in the dark as to the future of their investment in the crime fighting technology.




 Posted by
Posted by 

 Great article on how
Great article on how