Great article by Megan Favignano at New Press Now. Original article at http://www.newspressnow.com/news/local_news/data-continues-to-influence-policing/article_ef968ba2-389c-5289-b341-a9818ae231d7.html
A copy of the article follows:
 A recent report questions how some police departments are using data to forecast future crimes.
A recent report questions how some police departments are using data to forecast future crimes.
The report examined how departments are utilizing predictive policing, a computer software that uses data to forecast where crime may happen, who may commit it and who could be potential victims.
Upturn, an analysis organization out of Washington, D.C., that works with a variety of groups, published the report “Stuck in a Pattern” last month. “Predictive policing,” the report states, is a marketing term popularized by vendors who sell the software.
 How police departments nationwide utilize crime statistics and the software available to patrol officers monitoring incidents has evolved a lot in the past couple decades, Sgt. Tracy Barton with the St. Joseph Police Department said. Barton started as a patrol officer 20 years ago. He said having software like police have today would have been useful.
How police departments nationwide utilize crime statistics and the software available to patrol officers monitoring incidents has evolved a lot in the past couple decades, Sgt. Tracy Barton with the St. Joseph Police Department said. Barton started as a patrol officer 20 years ago. He said having software like police have today would have been useful.
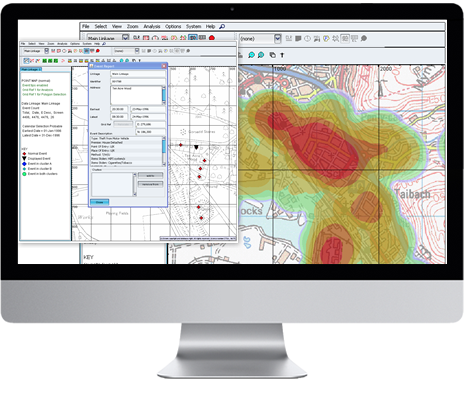
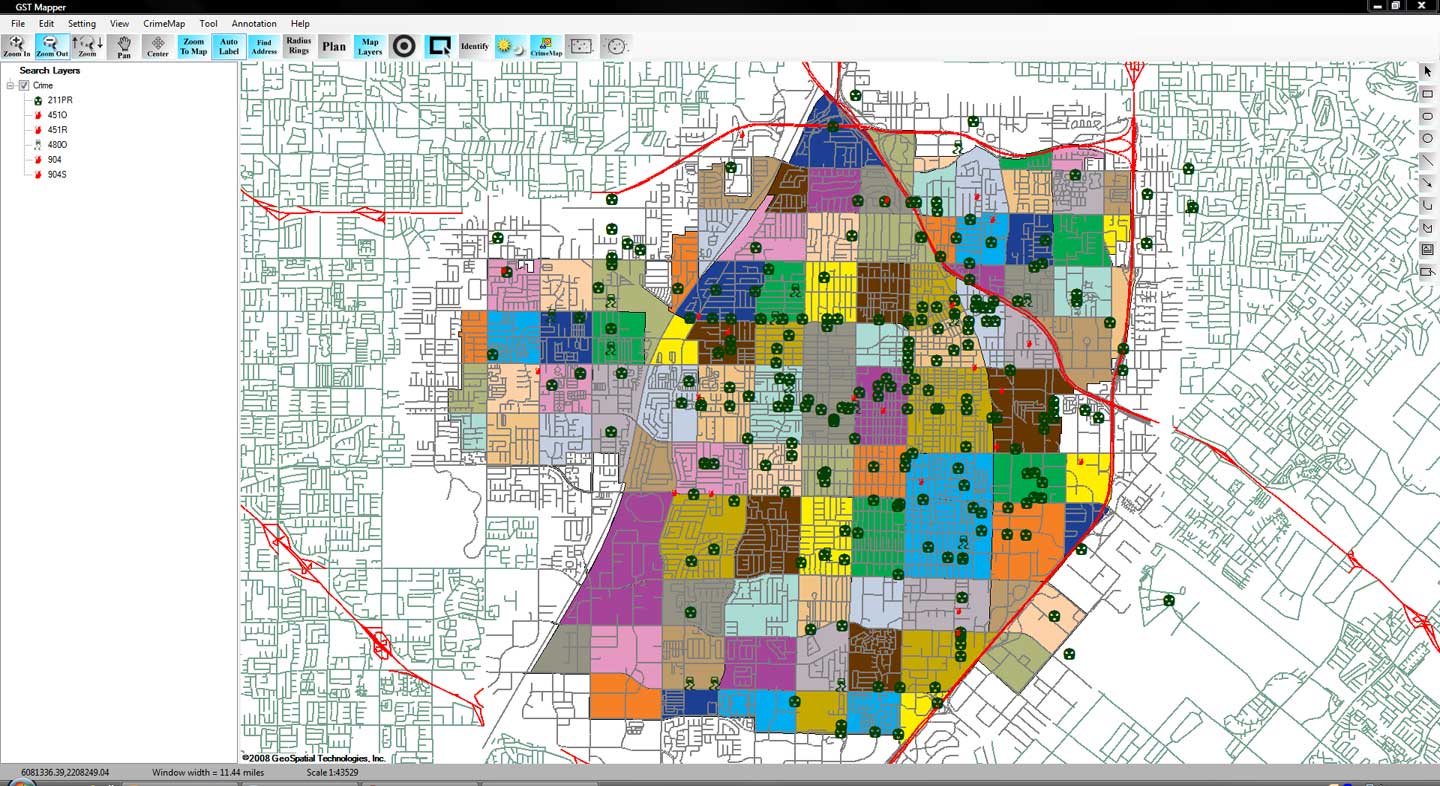
In the past, crime analysts used physical maps and mathematical algorithms to do what software does instantly today. Barton, the St. Joseph Police Department’s crime analyst, uses software that takes into account crimes reported to police to show crime hot spots in the city. A map of those hot spots is available online. Officers, he said, have access to a more in-depth version of that hot spots map, which includes extra details about the area and the crimes occurring.
The hot spots approach St. Joseph police use is most helpful in preventing crime when a series of crimes occur or when there is a crime pattern in a given area, he said. St. Joseph’s small size, Barton added, poses an extra challenge.
The St. Joseph Police Department has had its current software for just a few years. It doesn’t fit the definition of the predictive policing software Upturn outlines in the recent report. The software used locally depends on crime reports police receive. Predictive policing also looks at what types of business are located in an area, if repeat offenders live nearby and other information to predict where crimes may occur. Typically, according to the recent report, predictive policing takes one of two approaches, focusing either on place-based data or person-based data to make predictions.
Kevin Bryant, sociology and criminology professor at Benedictine College, said when people hear predictive policing described, they often think of the movie “Minority Report.” The software, he said, is nothing like in the movies.
“Predictive policing now has kind of morphed into better proactive methods that are based on prediction to some extent in forecasting risk,” Bryant said of how data-driven policing has changed over time. “But what we’ve learned through evaluation studies is that it’s really more important what the police do when they’re in a crime hot spot.”
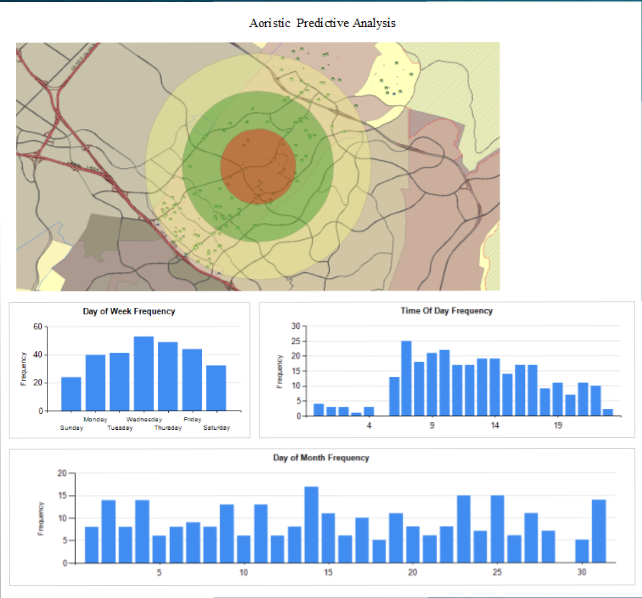 ryant worked with the Shawnee, Kansas, Police Department on research that looked at what he calls “smart policing.” In his research and in other work he has read, Bryant said it’s important for police to have a high visibility in crime hot spots, for officers to make connections with the public and for them to avoid staying in crime hot spots for extended periods of time.
ryant worked with the Shawnee, Kansas, Police Department on research that looked at what he calls “smart policing.” In his research and in other work he has read, Bryant said it’s important for police to have a high visibility in crime hot spots, for officers to make connections with the public and for them to avoid staying in crime hot spots for extended periods of time.When police are in a hot spot for too long, public surveys show area residents feel like they are being picked on rather than protected, he said. Predictive policing takes into account businesses in a given area. Bryant said some types of facilities are at a higher risk of victimization and others can attract crime to an area.
“Knowing where bars, taverns, restaurants, gas stations, convenience stores are, we can actually use their locations as a means of forecasting where crime might emerge at a later date,” Bryant said. “Part of predictive policing is predicting who the risky offenders are and that can be controversial.”
Upturn’s report also explored an ongoing debate among criminologists on the impact of using crime reports when determining patrol.
“Criminologists have long emphasized that crime reports and other statistics gathered by the police are not an accurate record of the crime that happens in a community,” the report states.