Sponsored by Case Closed Software, this 25 minute video features author and former law enforcement official Daniel McDevitt as he overviews some of the best practices developed over his 40+ year career in criminal investigations.
Daniel is the author of Managing The Investigation Unit, and Major Case Management, and is recognized across the country as a leading expert in this field.
Grab a coffee, sit back, and watch the video HERE on YouTube.
Category Archives: Investigation Software
Investigative Link Analysis: Consider the Source
Posted by Tyler Wood, Operations Manager at Case Closed Software and Crime Tech Solutions
Investigative link analysis and visualization software is a powerful tool for both law enforcement agencies and the private sector investigators alike. It allows investigators to visualize the hidden, non-obvious connections that would likely otherwise go undetected. After all, we know that the human brain is much more easily able to make connections when information is presented via images rather than text.
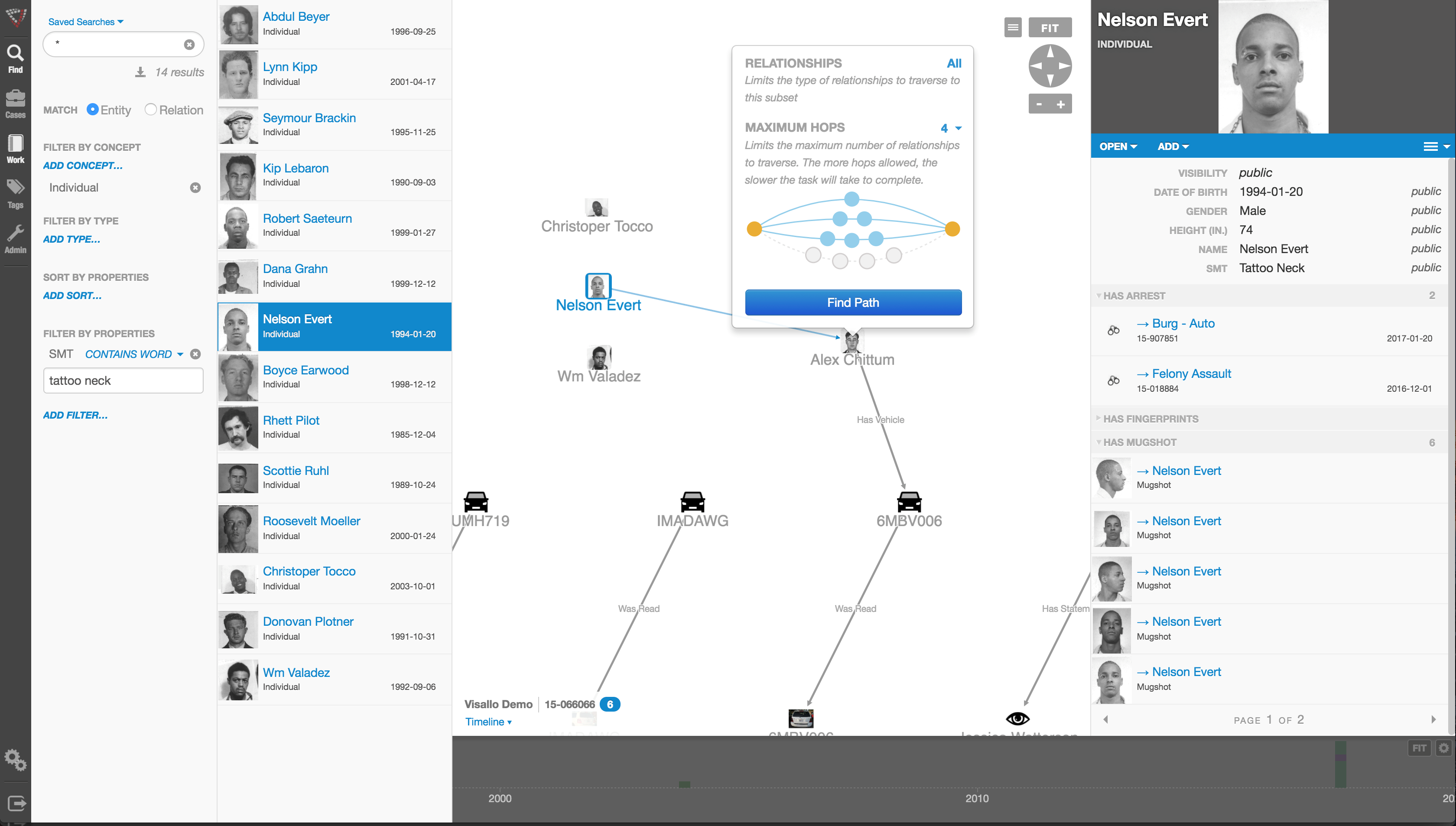
The software does, however, need a human to tell it what to look for, and where to look for it. Information is visualized in link analysis software by importing or querying a set of data, and then organizing that data according to parameters set by an investigator. The investigator is responsible for telling the software how to organize the data, and where to gather it from.
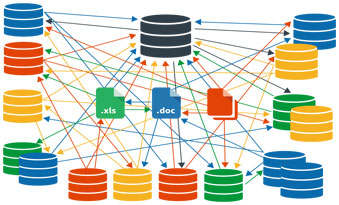
A smart investigator will utilize multiple sources when visualizing software. The majority of the time, not all the information needed for an investigation will come from the same source.
Law Enforcement investigators may need to pull RMS data, cell phone records, case management records, and even third party data, etc, to fully understand the big picture in a scenario. By using link analysis to cross-reference these data clusters against each other, the investigator is able to see even more connections, and find even more relevant data that may be crucial in solving a case.
It is important for investigators to exhaust all their resources so they can paint the clearest picture possible. This marriage of intuition and technology ensures that no connections stay hidden from investigation.
The key, as in all of life, is considering the source.
Contact us for more information about how powerful investigation big data link analysis can help your agency today.
[contact-form][contact-field label=”Name” type=”name” required=”1″ /][contact-field label=”Email” type=”email” required=”1″ /][contact-field label=”Website” type=”url” /][contact-field label=”Comment” type=”textarea” required=”1″ /][/contact-form]
Must Read: The Rise of Big Data Policing
 Here’s an excellent, must-read article from Andrew Guthrie Ferguson, a Professor of Law at the UDC David A. Clarke School of Law and author of the book The Rise of Big Data Policing: Surveillance, Race, and the Future of Law Enforcement (NYU Press 2017).
Here’s an excellent, must-read article from Andrew Guthrie Ferguson, a Professor of Law at the UDC David A. Clarke School of Law and author of the book The Rise of Big Data Policing: Surveillance, Race, and the Future of Law Enforcement (NYU Press 2017).
“The big data policing revolution has arrived. The singular insight of this innovation is that data-driven predictive technologies can identify and forecast risk for the future. Risk identification is also the goal of this book — to forecast the potential problems of big data policing as it reshapes law enforcement.”
Read the full article HERE.
In the meantime,  Case Closed Software™ reminds you that, as the only true alternative to Palantir®, we specialize in big data investigation analytics combined with the industry’s most robust investigative case management solution.
Case Closed Software™ reminds you that, as the only true alternative to Palantir®, we specialize in big data investigation analytics combined with the industry’s most robust investigative case management solution.
We are “Palantir® without the price tag and data-lock”.
Contact us for more information below:
[contact-form][contact-field label=”Name” type=”name” required=”1″ /][contact-field label=”Email” type=”email” required=”1″ /][contact-field label=”Website” type=”url” /][contact-field label=”Comment” type=”textarea” required=”1″ /][/contact-form]
Big Data Surveillance: The Case of Policing
Posted by Douglas Wood, CEO of Case Closed Software – a leader in investigation software and analytics for law enforcement.
Headquartered here in Central Texas, I recently had an opportunity to have coffee with Dr. Sarah Brayne, Assistant Professor, Department of Sociology at The University of Texas at Austin. Ms. Brayne had just published an interesting article in The American Sociological Review. The article is titled Big Data Surveillance: The Case of Policing.
The article examines the intersection of two emerging developments: the increase in surveillance and the massive exploration of “big data.” Drawing on observations and interviews conducted within the Los Angeles Police Department, Sarah offers an empirical account of how the adoption of big data analytics does—and does not—transform police surveillance practices.
She argues that the adoption of big data analytics facilitates may amplify previous surveillance practices, and outlines the following findings:
- Discretionary assessments of risk are supplemented and quantified using risk scores.
- Data tends to be used for predictive, rather than reactive or explanatory, purposes. (Here, Crime Tech Weekly would want to differentiate between predictive analytics and investigation analytics)
- The proliferation of automatic alert systems makes it possible to systematically surveil an unprecedentedly large number of people.
- The threshold for inclusion in law enforcement databases (gang databases, criminal intelligence data, etc) is lower, now including individuals who have not had direct police contact. (Here again, Crime Tech Weekly would point out that adherence to criminal intelligence best practices vastly reduces this likelihood)
- Previously separate data systems are merged, facilitating the spread of surveillance into a wide range of institutions.
Based on these findings, Sarah develops a theoretical model of big data surveillance that can be applied to institutional domains beyond the criminal justice system. Finally, she highlights the social consequences of big data surveillance for law and social inequality.
The full PDF report can be downloaded via Sage Publishing by clicking here. Or, if you have general comments or questions and do not wish to download the full version, please feel free to contact us through the form below. Crime Tech Weekly will be happy to weigh in.
[contact-form][contact-field label=”Name” type=”name” required=”1″ /][contact-field label=”Email” type=”email” required=”1″ /][contact-field label=”Website” type=”url” /][contact-field label=”Comment” type=”textarea” required=”1″ /][/contact-form]
Data Analytics Transforms Policing
 Great article from our friends at Visallo!
Great article from our friends at Visallo!
As police find new methods of tracking and solving crime, their needs and priorities in a data analytics strategy are bound to continuously evolve.
Be sure to read the article at the popular Visallo Blog, and for more information on how Visallo and Crime Tech Solutions are changing the investigation analytics world, contact us with the form below.
[contact-form][contact-field label=”Name” type=”name” required=”1″ /][contact-field label=”Email” type=”email” required=”1″ /][contact-field label=”Website” type=”url” /][contact-field label=”Comment” type=”textarea” required=”1″ /][/contact-form]
The benefits of investigation case management software
You needn’t be a criminal investigator for particularly long before beginning to feel overwhelmed. Even the most seasoned detectives can be torn between competing priorities such as internal briefings, public scrutiny, phone calls, emails, and the general business that police officers experience every day.
Causing even more grief – and consuming additional time and resources – are the routine tasks of managing investigation case files, documents, interviews, supplemental reports, as well as preparing for DA meetings, court dates, and so on. The manual effort of attempting to locate specific pieces of evidence or paper documents, and then trying to determine how they fit together and disseminating the conclusions is massive.
Managing a criminal investigation becomes more and more difficult each day, given the sheer amount of information generated. Evidence and clues must be garnered from things such as call detail records, body cam video, crime scene photos, arrest records, calls for service data, search warrant results, physical evidence management, and so on… and they all combine to make management of individual cases nearly impossible without the appropriate resources
In an era where senior law enforcement officials are being asked to do ‘more’ with ‘less’, however, those resources can rarely come by way of additional staff. Instead, there are technology solutions, thankfully, that ease the pain that lies in the process of managing criminal investigations.
Investigation Case Management Software (ICMS) such as Case Closed Software provides investigation units with a solution that reduces the paper chase, keeps everything in order, and helps investigators close more cases, more quickly. Case Closed is also available via the cloud with Case Closed Cloud.
From a resource utilization perspective, effective ICMS automates the time-consuming tasks of:
- Storing and retrieving documents such as witness statements, complaints, and supplemental reports
- Locating and managing important audio and video files
- Tracking physical evidence
- Effectively communicating with counterparts
- Keeping up with assigned tasks
- Managing incoming tips and leads
- Developing and understanding connections across incidents and cases
- And much, much more.
From a productivity perspective, the benefits are also wide and varied:
- ICMS saves everything in real time. Detectives never have to worry about losing important documents.
- Allows case data to be entered anywhere – in the office, in the field, or at home.
- Makes everything searchable. People. Places. Things… everything is cross-indexed and easily ‘findable’.
- Provides real-time alerts to notify agents when and if information matches something already in the system.
- Generates standard reports with a few keystrokes based on information in the system.
- Easy preparation for internal status update meetings.
- Allows investigators to share case files internally – or externally to the DA.
- Etcetera, etcetera, etcetera!
Many agencies are still operating investigations on paper files or antiquated, unfriendly systems because they believe the cost of implementing ICMS is prohibitive. Nothing could be further from the truth. The cost of effective software is now well within reach of the vast majority of law enforcement agencies. More importantly, the benefits far outweigh these costs.
Spend less. Solve more cases. Case Closed Software. Download a free brochure.
Visallo and Crime Tech Solutions: Partners in Crime-Fighting Software
Sterling, VA (August 24, 2017) – Visallo, the Sterling, VA based provider of investigation analytics software, and only true competitor to Silicon Valley giant Palantir, today announced a strategic partnership with Crime Tech Solutions out of Leander, TX.
 According to Jeff Kunkle, President of Visallo, the partnership enhances his company’s suite of easy-to-use, web-based data visualization tools for investigative link analysis, data discovery, crime analytics and geospatial analysis with Crime Tech Solutions’ powerful and flexible Case Closed investigation case management software.
According to Jeff Kunkle, President of Visallo, the partnership enhances his company’s suite of easy-to-use, web-based data visualization tools for investigative link analysis, data discovery, crime analytics and geospatial analysis with Crime Tech Solutions’ powerful and flexible Case Closed investigation case management software.
“Visallo is designed for intelligence analysts, law enforcement investigators, and fraud analysts who need easy to use tools to help them discover and visualize complex relationships within vast amounts of data without resorting to time-consuming, ad-hoc, and error-prone manual processes,” said Mr. Kunkle. “These are analysts that want to make sure they don’t miss important non-obvious insights during their investigations, want to produce more accurate, thorough, and defensible conclusions, and ultimately seek to be more accomplished investigators able to tackle the toughest cases.”
Tyler Wood, VP of Operations at Crime Tech Solutions added, “Where Visallo does much of the big data analytics, the Case Closed software is specifically designed for investigative process and major case management. The software manages the entire investigation workflow from start to finish and includes functionality such as task management, alerting, communications, evidence management, and a great deal more.”
Until now, investigative agencies had to turn to multi-million dollar solutions from behemoth multinational companies for this combined functionality. The partnership is designed to give customers more investigation functionality at a price point that can scale down to smaller groups. “For years, only the largest law enforcement and federal agencies could afford to purchase these types of advanced tools,” added Mr. Kunkle. “The partnership between Visallo and Crime Tech Solutions changes that reality.”
The companies have indicated that integration efforts are already underway to ensure a seamless and user-friendly experience.
About Visallo
Visallo helps investigators of all types produce more accurate, thorough, and timely analysis with a software platform to help them discover, visualize, and understand complex relationships hidden in massive amounts of data. Visallo’s all-in-one suite of easy-to-use, web-based, visualization tools and machine learning data analysis algorithms augment the investigator’s hard-earned experience and intuition with data-driven insights that would be difficult, if not impossible, to discover otherwise.
About Crime Tech Solutions
Crime Tech Solutions develops and markets a robust suite of powerful software solutions designed for intelligence and investigation teams. Their flagship products include the popular Case Closed™ investigation platform and IntelNexus™, an advanced criminal intelligence management software.
Big Data Investigation Analytics: A Difference Maker for Law Enforcement
How Investigative Agencies do More with Less!
The investigative units of law enforcement agencies all around the world face many of the same challenges. Chief among those challenges is the fact that budgets are tightening, while resources are becoming more and more scarce. Even in the face of reduced funding, investigators are asked to deliver higher levels of service in their quest to solve and deter crime.
The key to doing ‘more’ with ‘less’ in law enforcement is really no different than in any other industry. That is, deploying resources in the most effective manner possible for the maximum value possible. The trick is using what the agency already knows to determine what the future may hold. What that all boils down to is Big Data Investigation Analytics.
Data in Law Enforcement comes in many forms, and is typically stored in disparate silos. Arrest records, calls for service, criminal intelligence, field reports, human resource data, telephone records, case management files, and so on. Together, the data from those systems can represent a virtual goldmine of investigative information if used correctly.
 ‘Correctly’ is the operative term, of course. The ability to turn these large data stores into actionable investigation intelligence requires more than a simple data warehouse or data mining tool, and for the most part police departments recognize this need. They understand that their data holds the key to understanding the hidden connections between people, places, and things – the lynchpin of any successful investigation.
‘Correctly’ is the operative term, of course. The ability to turn these large data stores into actionable investigation intelligence requires more than a simple data warehouse or data mining tool, and for the most part police departments recognize this need. They understand that their data holds the key to understanding the hidden connections between people, places, and things – the lynchpin of any successful investigation.
For years, law enforcement agencies and commercial organizations have built data mining tools and data warehouses. Unfortunately, these analytical techniques are no longer sufficient in an age of rapidly growing data. Moreover, much of the data that investigators need to access is unstructured text – word processing documents, narratives, search warrants, witness statements, email text, and more. By applying big data text analytics, investigators can begin to extract actionable insights from both structured and unstructured data.
 Big Data Investigation Analytics – such as those provided by Virginia based Visallo and California’s Palantir Technologies – are two examples that provide a powerful indexing architecture allowing investigators to find non-textual data, including multimedia files such as 911 calls, interrogation videos, and images. This architecture helps investigators find things that they simply could not find otherwise.
Big Data Investigation Analytics – such as those provided by Virginia based Visallo and California’s Palantir Technologies – are two examples that provide a powerful indexing architecture allowing investigators to find non-textual data, including multimedia files such as 911 calls, interrogation videos, and images. This architecture helps investigators find things that they simply could not find otherwise.
Finally, world-class investigation analytics provide a flexible graph visualization tool, as well. This user interface allows investigators to organize data through a variety of layout options, find hidden and non-obvious relationships between entities, and perform a variety of what-if scenarios.
 When paired with the robust investigative case management and criminal intelligence systems available from Crime Tech Solutions, big data investigation analytics build a foundation upon which investigators can solve more crimes, more quickly.
When paired with the robust investigative case management and criminal intelligence systems available from Crime Tech Solutions, big data investigation analytics build a foundation upon which investigators can solve more crimes, more quickly.
Without advanced investigation analytics, agencies often find themselves looking for a needle in a haystack. In fact, too often the needle is broken into several pieces spread across multiple haystacks. To simplify these tasks, investigative agencies must deploy the correct analytical technologies which have become a key element of doing more with less in the global investigation market. For more information on how Crime Tech Solutions and Visallo are changing the law enforcement analytics landscape, please contact us below!
[contact-form][contact-field label=”Name” type=”name” required=”1″ /][contact-field label=”Email” type=”email” required=”1″ /][contact-field label=”Website” type=”url” /][contact-field label=”Comment” type=”textarea” required=”1″ /][/contact-form]
SoCal City Selects Crime Tech Solutions for Link Analysis.
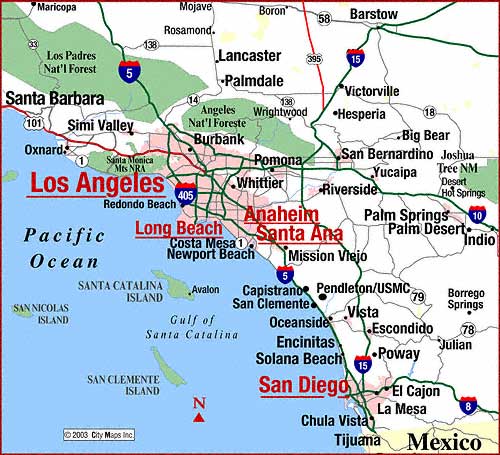 Crime Tech Solutions, LLC – a fast growing, vibrant software company based in Leander, TX today announced that a large, coastal city in California has selected them to provide sophisticated link and social network analysis software.
Crime Tech Solutions, LLC – a fast growing, vibrant software company based in Leander, TX today announced that a large, coastal city in California has selected them to provide sophisticated link and social network analysis software.
Crime Tech Solutions was awarded the contract based upon its price/performance leadership in the world of big data analytics for law enforcement and other investigative agencies.
Link analysis software is used by investigators to visualize hidden connections between people, places, and things within large and disparate data sets.
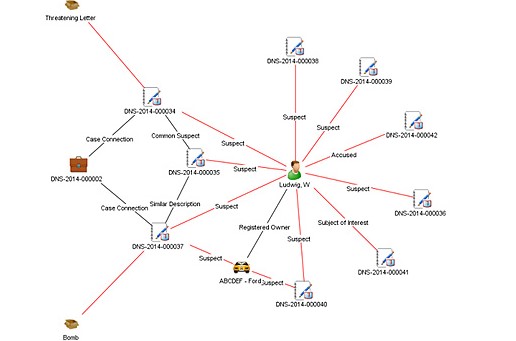
“Our link analysis software gives investigators an edge in the way they analyze data”, said Crime Tech Solutions’ CEO, Doug Wood. “By finding and displaying those hard to find connections and anomalies that reside in different data stores, our software helps investigative agencies more clearly see how networks of entities exist.”
Crime Tech Solutions said that the software implementation is already underway, and that the software will make life a little more miserable for criminals in the Southern California city.
The company also develops investigative case management and criminal intelligence software for law enforcement agencies of all sizes.
Criminal Intelligence Databases: Violations of privacy rights are the exception, not the rule.
 The notion that law enforcement fusion centers regularly violate individuals’ privacy rights as they capture intelligence on gangs, terrorist activities, organized crime, and other threats to public safety is simply not true. That, according to a study published in the Journal of Police and Criminal Psychology.
The notion that law enforcement fusion centers regularly violate individuals’ privacy rights as they capture intelligence on gangs, terrorist activities, organized crime, and other threats to public safety is simply not true. That, according to a study published in the Journal of Police and Criminal Psychology.The paper, “Law Enforcement Fusion Centers: Cultivating an Information Sharing Environment while Safeguarding Privacy,” was authored by Jeremy Carter, an assistant professor of Public and Environmental Affairs at Indiana University-Purdue University Indianapolis. His article carefully addresses the privacy-rights issue of criminal intelligence gathering, among others.
 There are approximately 80 fusion centers in the United States. They were created in response to the 9/11 terrorist attacks. The attacks exposed the requirement for greater information sharing and improved intelligence capabilities at all law enforcement levels. According to the article’s author, the idea was to have the key pieces of data funneled into fusion centers so that highly trained analysts could stay atop of threats and correspond with local law enforcement agencies on these potential threats.
There are approximately 80 fusion centers in the United States. They were created in response to the 9/11 terrorist attacks. The attacks exposed the requirement for greater information sharing and improved intelligence capabilities at all law enforcement levels. According to the article’s author, the idea was to have the key pieces of data funneled into fusion centers so that highly trained analysts could stay atop of threats and correspond with local law enforcement agencies on these potential threats.Designed with a view to enhance information-sharing among agencies, fusion centers act as ‘hubs’ of data and intelligence on gang activities, terrorist cells, organized crime, and other public safety threats. Vast amounts have data has been collected, and concerns about individual privacy and civil rights have ensued. The very legitimacy of these fusion centers has been called into question.
 The notion that law enforcement fusion centers represent ‘Big Brother’, and that data is being stored and disseminated about people irrespective of whether they are suspected of criminal activity is simply wrong, according to Professor Carter.
The notion that law enforcement fusion centers represent ‘Big Brother’, and that data is being stored and disseminated about people irrespective of whether they are suspected of criminal activity is simply wrong, according to Professor Carter.Still, concerns remain about who can access the data, and for what purpose. However, a survey of fusion centers across the country suggests that they take appropriate steps to safeguard individual privacy via something called Federal Regulatory Code CFR 28 Part 23.
 “Fusion centers are following the federal regulatory code, 28 CFR Part 23, that is the legal standard for collecting information,” Carter said. “That code says you have to establish a criminal predicate, basically probable cause, to keep information on identifiable individuals.”
“Fusion centers are following the federal regulatory code, 28 CFR Part 23, that is the legal standard for collecting information,” Carter said. “That code says you have to establish a criminal predicate, basically probable cause, to keep information on identifiable individuals.”Additionally, the majority of the fusion centers have implemented strong controls that provide built-in safeguards that protect the privacy of individuals. The fusion centers are also regularly audited to ensure that only the correct type of data is gathered, and that is stored and disseminated in a need-to-know basis.
 Crime Tech Solutions develops and markets a suite of crime fighting software including IntelNexus™, a criminal intelligence database system that complies with the above mentioned code 28 CFR Part 23. The company also provides software for investigation case management, advanced crime analytics, and link/social network analysis.
Crime Tech Solutions develops and markets a suite of crime fighting software including IntelNexus™, a criminal intelligence database system that complies with the above mentioned code 28 CFR Part 23. The company also provides software for investigation case management, advanced crime analytics, and link/social network analysis.


